Question: The data flowing through the Smart Grid's communication networks offers manifold utilities [4]. Utility companies can leverage this data for demand forecasting, ensuring grid reliability,
The data flowing through the Smart Grid's communication networks offers manifold utilities [4]. Utility companies can leverage this data for demand forecasting, ensuring grid reliability, and fostering efficient energy distribution [6]. Moreover, the data can inform dynamic pricing models, facilitate remote grid monitoring, and enhance customer service [9]. Additionally, the data can guide infrastructure development, bolster security measures, and aid in the integration of renewable energy sources [7]. Ensuring the confidentiality, integrity, and availability (CIA) of this data is of paramount importance [12]. The confidentiality of data ensures that sensitive information, such as user consumption patterns or grid operational details, remains inaccessible to unauthorized entities [9]. Breaches in confidentiality could lead to scenarios where malicious actors manipulate energy prices or target specific households [10]. For instance, if an attacker gains knowledge about when a household consumes the least amount of energy, they might infer the residents are not home, making the house a potential target for burglary [11]. Integrity ensures that the data remains unaltered during transmission and storage [5]. Any compromise in integrity can have grave repercussions. For example, if an attacker tampers with consumption data, they could artificially inflate energy bills or even cause grid imbalances by falsifying demand data [4]. Lastly, availability ensures that data is accessible when needed [2]. DDoS attacks targeting grid communication networks could render essential data inaccessible, leading to grid inefficiencies, blackouts, or even catastrophic system failures [3]. Ensuring uninterrupted data access is crucial for maintaining grid stability and efficient operations. In summary, the Smart Grid's data is not only vital for operational efficiency but also for the safety and security of the entire energy infrastructure. Properly harnessed and secured, this data can propel the Smart Grid towards optimal performance, environmental sustainability, and robust security [12].
My questions are below.
- Create an accurate CORAS asset diagram. An asset diagram contains the party, direct asset and indirect asset.
- Create a high-level analysis of a list of unwanted incidents, threats, vulnerabilities and threat scenarios. high level analysis has only 3 rows. row 1 is who/what causes it row 2 Risk description is how?what is the senario or incident? what is harmed row 3 is What causes it?
- Create an accurate CORAS threat diagram that describes, identifies and estimates threats
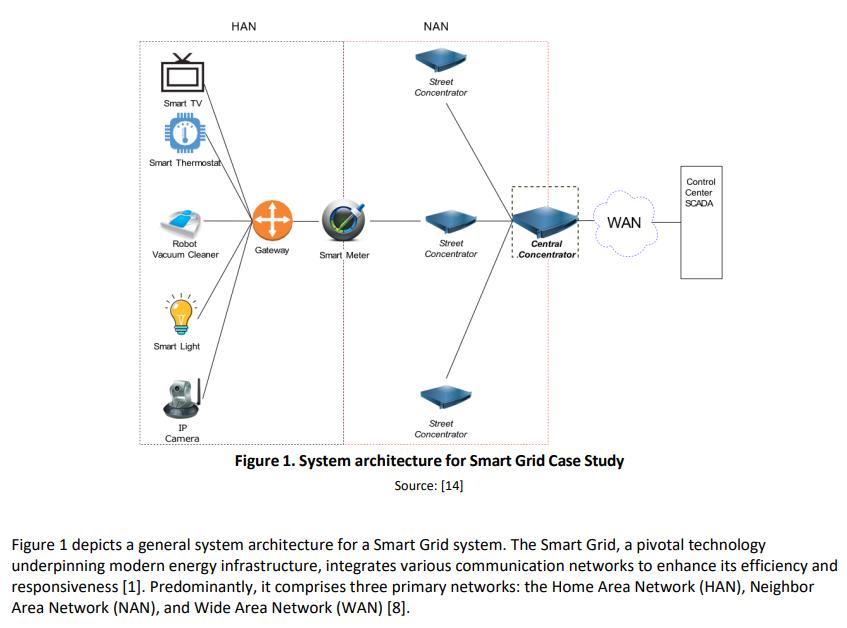
Smart TV Smart Thermostar Robot Vacuum Cleaner Smart Light IP Camera HAN + Gateway Smart Meter NAN Street Concentrator Street Concentrator Street Concentrator Central Concentrator WAN Figure 1. System architecture for Smart Grid Case Study Source: [14] Control Center SCADA Figure 1 depicts a general system architecture for a Smart Grid system. The Smart Grid, a pivotal technology underpinning modern energy infrastructure, integrates various communication networks to enhance its efficiency and responsiveness [1]. Predominantly, it comprises three primary networks: the Home Area Network (HAN), Neighbor Area Network (NAN), and Wide Area Network (WAN) [8].
Step by Step Solution
There are 3 Steps involved in it
Solutions Step 1 CORAS Asset Diagram Party Utility Company Direct Asset Smart Grid Data Indirect Asset Smart Grid Communication Network HighLevel Analysis of Unwanted Incidents Threats Vulnerabilities ... View full answer

Get step-by-step solutions from verified subject matter experts


