Question
The First part of the questionbwas already sloved . Step 2: The input after IP will be spilt into two parts: left 32-bit and right
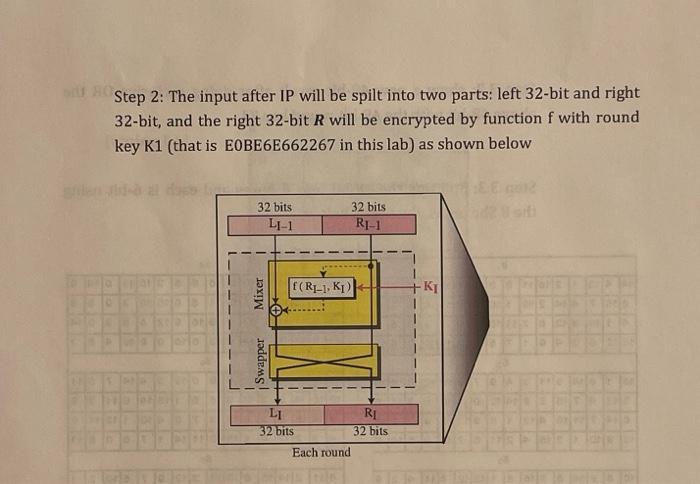

The First part of the questionbwas already sloved .
Step 2: The input after IP will be spilt into two parts: left 32-bit and right 32-bit, and the right 32-bit R will be encrypted by function f with round key K1 (that is EOBE6E662267 in this lab) as shown below Swapper LI 32 bits Mixer 32 bits. LI-1 32 bits RI-1 f(R1-1, K1) KI Each round RI 32 bits
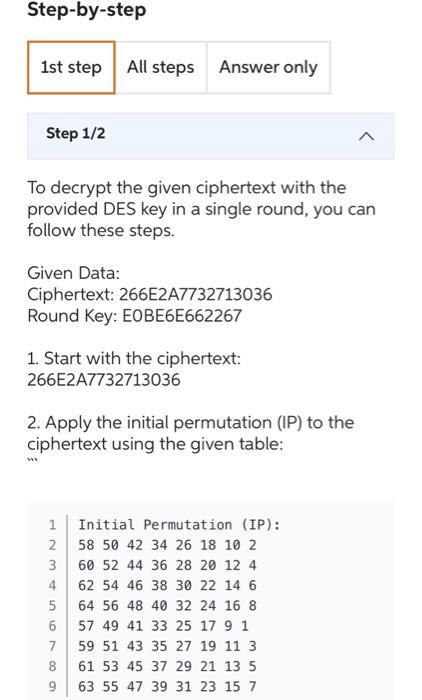
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get StartedRecommended Textbook for
Numerical Methods With Chemical Engineering Applications
Authors: Kevin D. Dorfman, Prodromos Daoutidis
1st Edition
1107135117, 978-1107135116
Students also viewed these Programming questions
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
View Answer in SolutionInn App



