Question
The operating system is the physical environment where applications run. Any vulnerability in the operating system could compromise the security of one or more applications.
The operating system is the physical environment where applications run. Any vulnerability in the operating system could compromise the security of one or more applications. Threats can come through the Web, but they can also come from a physical terminal. Even if the Web access is very secure, if an attacker obtains physical access to a server, breaking into a system is much easier.
Suppose you are a Cyber Security Analyst at IT-Security Solutions Ltd, located across Australia. Your new client is going to deploy operating systems (OS) for their office. They have identified Microsoft Windows Server 2022 for their server OS and Microsoft Windows 11 for employee desktop OS. The client wants to strengthen their computer network against future cyber-attacks. Therefore, they have contacted your company for conducting a through vulnerability assessment. The team leader in the vulnerability assessment team has allocated this task to you. As a Cyber Security Analyst, you have been asked to conduct an analysis about recent vulnerabilities associated with Microsoft Windows Server 2022 and Microsoft Windows 11. You will provide a report to your team leader based on the findings. The report should include the following sections:
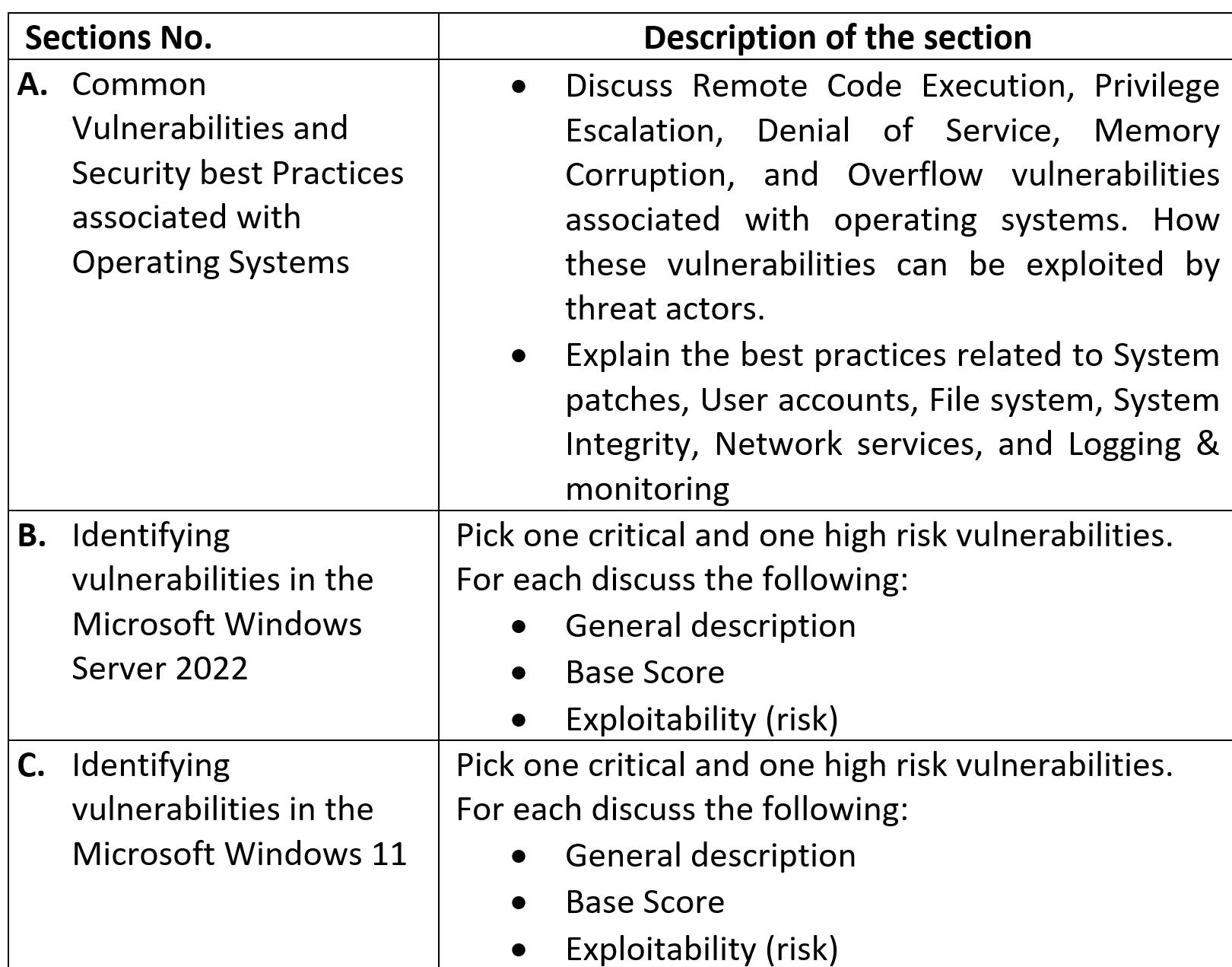
A.Common Vulnerabilities and Best Practices to secure Operating
Some of the most common vulnerabilities associated with operating systems are Remote Code Execution, Privilege Escalation, Denial of Service, Memory Corruption, and Overflow. Discuss these vulnerabilities. How these can be exploited by threat actors. Explain the best practices in terms of system patches, user accounts, file system, system integrity, network services, and logging & monitoring to secure Operating Systems in the Organisation.
B.Analysis about potential security vulnerabilities in the Microsoft Windows Server 2022
Perform internet research to find about known exploitable vulnerabilities in the Microsoft Windows Server 2022. Pick two different vulnerabilities, one critical and one high-risk. You need to have sound knowledge about CVSS and CVE for that. For this you need go through NIST's National Vulnerability database (https://nvd.nist.gov/vuln) and Mitre's CVE database (https://cve.mitre.org/).
C.Analysis about potential security vulnerabilities in the Microsoft Windows 11
Perform internet research to find about known exploitable vulnerabilities in the Microsoft Windows 11. Pick two different vulnerabilities one critical and one high-risk. For this you need go through NIST's National Vulnerability database (https://nvd.nist.gov/vuln) and Mitre's CVE database (https://cve.mitre.org/).
Sections No. A. Common Vulnerabilities and Security best Practices associated with Operating Systems B. Identifying vulnerabilities in the Microsoft Windows Server 2022 C. Identifying vulnerabilities in the Microsoft Windows 11 Description of the section Discuss Remote Code Execution, Privilege Escalation, Denial of Service, Memory Corruption, and Overflow vulnerabilities associated with operating systems. How these vulnerabilities can be exploited by threat actors. Explain the best practices related to System patches, User accounts, File system, System Integrity, Network services, and Logging & monitoring Pick one critical and one high risk vulnerabilities. For each discuss the following: General description Base Score Exploitability (risk) Pick one critical and one high risk vulnerabilities. For each discuss the following: General description Base Score Exploitability (risk)
Step by Step Solution
3.45 Rating (155 Votes )
There are 3 Steps involved in it
Step: 1
A Common Vulnerabilities and Best Practices to Secure Operating Systems COMMON VULNERABILITIES The ability to remotely execute arbitrary code on a target machine is known as remote code execution RCE ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


