Answered step by step
Verified Expert Solution
Question
1 Approved Answer
The Unix command dd is a utility primarily used for converting or copying files. Users specify an input file path, output file path, and
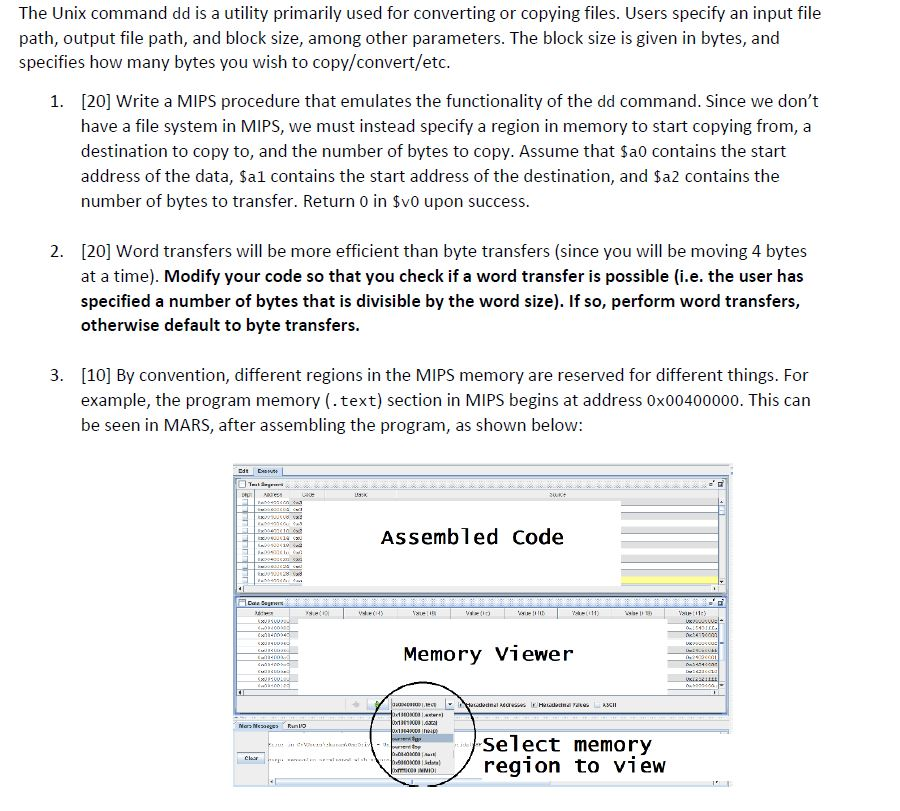
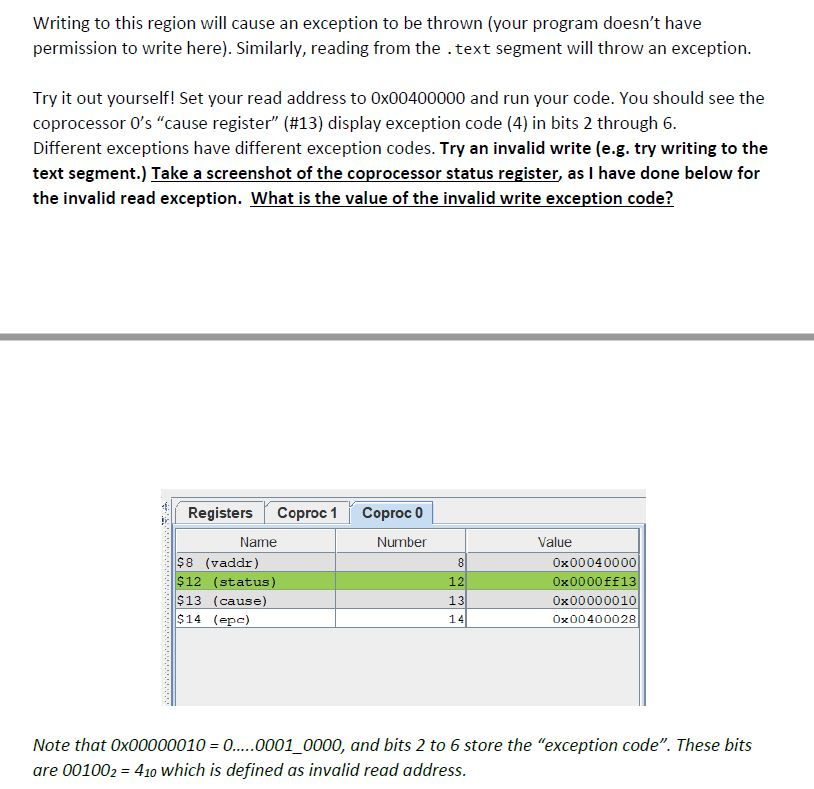
The Unix command dd is a utility primarily used for converting or copying files. Users specify an input file path, output file path, and block size, among other parameters. The block size is given in bytes, and specifies how many bytes you wish to copy/convert/etc. 1. [20] Write a MIPS procedure that emulates the functionality of the dd command. Since we don't have a file system in MIPS, we must instead specify a region in memory to start copying from, a destination to copy to, and the number of bytes to copy. Assume that $a0 contains the start address of the data, $al contains the start address of the destination, and $a2 contains the number of bytes to transfer. Return 0 in $v0 upon success. 2. [20] Word transfers will be more efficient than byte transfers (since you will be moving 4 bytes at a time). Modify your code so that you check if a word transfer is possible (i.e. the user has specified a number of bytes that is divisible by the word size). If so, perform word transfers, otherwise default to byte transfers. 3. [10] By convention, different regions in the MIPS memory are reserved for different things. For example, the program memory (.text) section in MIPS begins at address Ox00400000. This can be seen in MARS, after assembling the program, as shown below: Edt Dev 00002410 Ex0000128 Categ Ca SXESUL Cave K Assembled Code (14) V 10200 Memory Viewer x1300000 dedal Mo M Run 131000 x13040000 Clear Veke(111) wwwwwwww 15451 100000 ASCII 0.0840000 Coco INMID Select memory region to view 1221 Writing to this region will cause an exception to be thrown (your program doesn't have permission to write here). Similarly, reading from the text segment will throw an exception. Try it out yourself! Set your read address to Ox00400000 and run your code. You should see the coprocessor O's "cause register" (#13) display exception code (4) in bits 2 through 6. Different exceptions have different exception codes. Try an invalid write (e.g. try writing to the text segment.) Take a screenshot of the coprocessor status register, as I have done below for the invalid read exception. What is the value of the invalid write exception code? Registers Coproc 1 Coproc 0 Name $8 (vaddr) $12 (status) $13 (cause) $14 (epc) Number Value 8 0x00040000 12 13 14 234 0x0000ff13 0x00000010 0x00400028 Note that Ox00000010 = 0.....0001_0000, and bits 2 to 6 store the "exception code". These bits are 001002 = 410 which is defined as invalid read address. 4. [10] Modify your code so that it verifies (before any copying takes place) that the user hasn't specified an illegal region of memory to read from or copy to. If this occurs, return -1 to indicate an INVALID_READ, and -2 to indicate an INVALID_WRITE. 5. [20] Many command line utilities provide a "dry run" feature, where the console displays what would happen if the command were executed, without actually changing anything. Implement a dry run option for your procedure by adding a 4th parameter (passed in $a3) that optionally prints the source address and the data ($a3 = 1). For example, if the first 3 words are Address Content [0x10010000] 0x3408010a [0x10010004] 0x3409000c [0x10010008] 0x01195120 calling jal dd [$a0 = 0x10010000, $al the console should look like = , $a2 = 12, $a3 = 1], [0x10010000] 0x3408010a [0x10010004] 0x3409000c [0x10010008] 0x01195120 And if $a2 is not a multiple of 4 (so you cannot do word-level transfers, and are instead doing byte-level transfers), the console should look like this [0x10010000] 0x0a [0x10010001] 0x01 [0x10010002] 0x08
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


