Answered step by step
Verified Expert Solution
Question
1 Approved Answer
The Vigen re cipher is a method of encrypting alphabetic text using a series of interwoven Caesar ciphers, based on letters of a keyword. Notice
The Vigenre cipher is a method of encrypting alphabetic text using a series of interwoven Caesar ciphers, based on letters of a keyword.
Notice how in a caesar cipher, you shifted the alphabet by some integer value. Consider a mapping that maps alphabetic letters into numbers and vice versa The main difference between a Vigenre cipher and the Caesar cipher, is that the Vigenre cipher changes the shift value for every character, depending on a key.
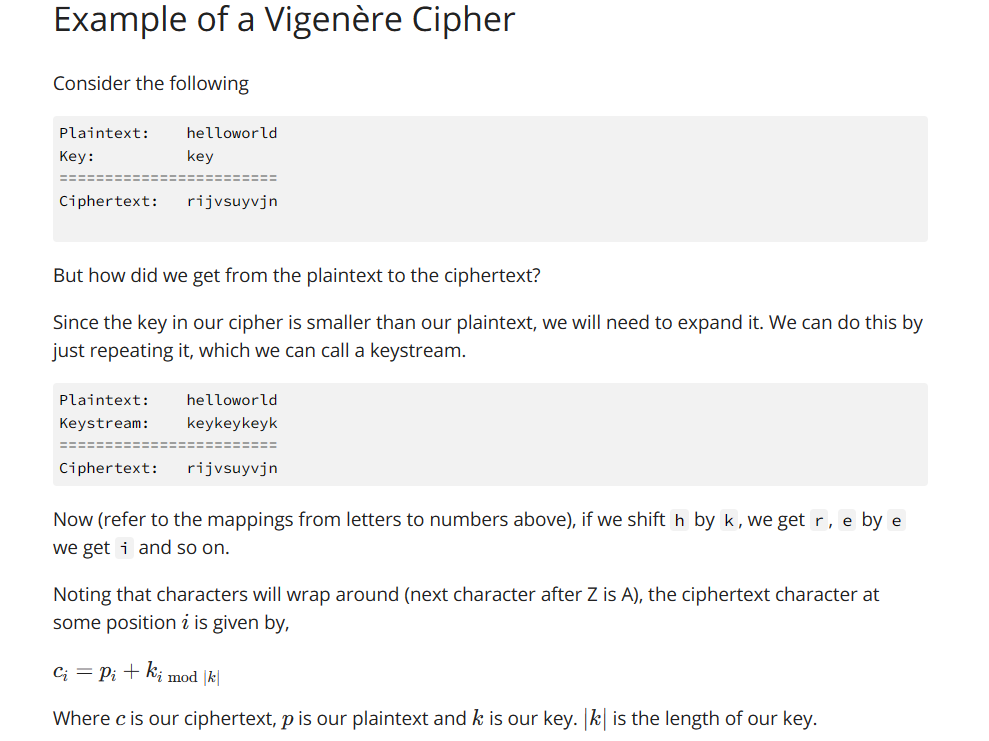
Example of a Vigenre Cipher
Consider the following Example of a Vigenre Cipher
Consider the followingendarray
Ciphertext:
rijvsuyvin
But how did we get from the plaintext to the ciphertext?
Since the key in our cipher is smaller than our plaintext, we will need to expand it We can do this by
just repeating it which we can call a keystream.
Now refer to the mappings from letters to numbers above if we shift by we get e by e
we get i and so on
Noting that characters will wrap around next character after is the ciphertext character at
some position is given by
Where is our ciphertext, is our plaintext and is our key. is the length of our key. Requirements
Your program will be required to both encrypt and decrypt ciphertext. The mode is specified by a
program argument flag, e for encrypt mode, and d for decrypt mode.
Your program should work for both upper and lowercase plaintextciphertextkeys even if the key
and plaintextciphertext do not have the same case as eachother.
Your program should also have another option for grouping output characters together. This can be
specified by the flag. What this will do is strip the ciphertext or plaintext of any non
alphabetic characters and group the output into spaceseparated groups consisting of The precedence of argument error handling follows the order of: program mode, and then
grouping. That is you only print one error even if there is more than one, following that order.
Examples
The # symbol denotes user input
$ python
vigenere.py e
Enter the key: #helloworld
Enter the plaintext: #The quick brown fox jumps over the lazy dog.
Ciphertext is: Alp bieqb muvay qct xlxsz sgpf pvv wdgc ozu.
$ python
vigenere.py d
Enter the key: #helloworld
Enter the ciphertext: #Alp bieqb muvay qct xlxsz sgpf pvv wdgc ozu.
Plaintext is: The quick brown fox jumps over the lazy dog.
Grouping
$ python
vigenere.py e g
Enter the key: #helloworld
Enter the plaintext: #The quick brown fox jumps over the lazy dog.
Ciphertext is: ALPBI EQBMU VAYQC TXLXS ZSGPF PVVWD GCOZU
$ python
vigenere.py d g
Enter the key: #helloworld $ python
vigenere.py d g
Enter the key: #helloworld
Enter the ciphertext: #Alp bieqb muvay qct xlxsz sgpf pvv wdgc ozu.
Plaintext is: THEQU ICKBR OWNFO XJUMP SOVER THELA ZYDOG
$ python
vigenere.py e g
Enter the key: #helloworld
Enter the plaintext: #The quick brown fox.
Ciphertext is: ALPBI EQBMU VAYQC T
In the third example, since we didn't have enough characters to make a full group, our last group
just wont have the full amount.
Errors
$ python
vigenere.py e d
Error: Cannot have both encrypt and decrypt mode.
$ python
vigenere.py g
Error: Program mode was not specified. Use e for encrypt and d for decrypt.
$ python
vigenere.py
Error: Program mode was not specified. Use e for encrypt and d for decrypt.
$ python
vigenere.py
Error: You must supply an integer of at least zero with the grouping flag.It is okay for the user to not enter a message. The key is required, though. You should keep asking
for the key until a valid one is provided by the user.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


