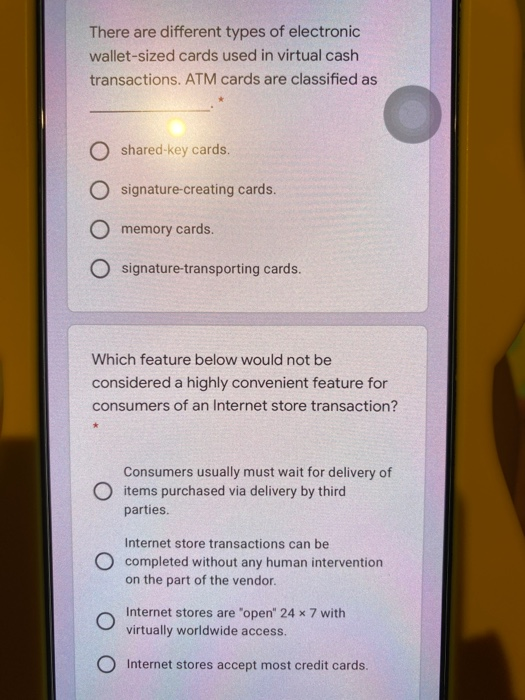
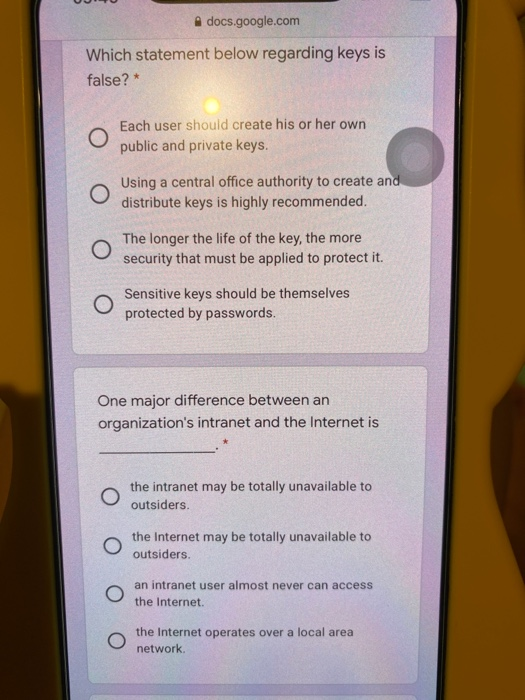
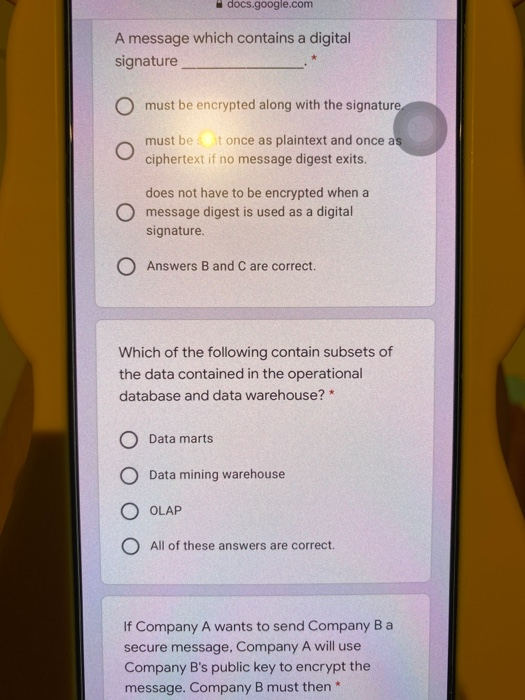
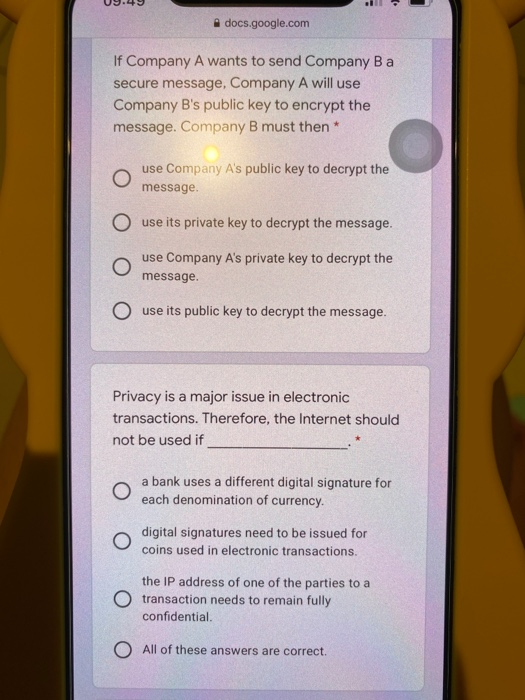
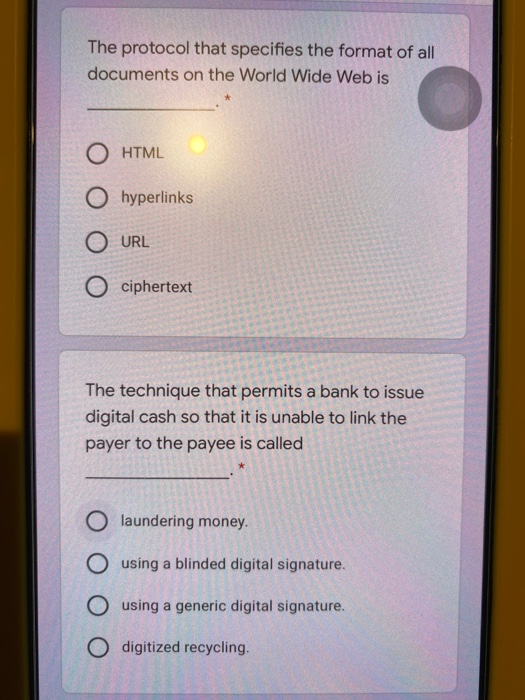
There are different types of electronic wallet-sized cards used in virtual cash transactions. ATM cards are classified as O shared-key cards O signature-creating cards. O memory cards. O signature-transporting cards. Which feature below would not be considered a highly convenient feature for consumers of an Internet store transaction? Consumers usually must wait for delivery of O items purchased via delivery by third parties. Internet store transactions can be O completed without any human intervention on the part of the vendor. Internet stores are "open" 24 x 7 with virtually worldwide access. O Internet stores accept most credit cards. docs.google.com Which statement below regarding keys is false? * Each user should create his or her own public and private keys. Using a central office authority to create and distribute keys is highly recommended. The longer the life of the key, the more security that must be applied to protect it. Sensitive keys should be themselves protected by passwords. One major difference between an organization's intranet and the Internet is the intranet may be totally unavailable to outsiders O the Internet may be totally unavailable to outsiders. an intranet user almost never can access the Internet. the Internet operates over a local area network docs.google.com A message which contains a digital signature O must be encrypted along with the signature must be it once as plaintext and once as ciphertext if no message digest exits. does not have to be encrypted when a O message digest is used as a digital signature O Answers B and C are correct. Which of the following contain subsets of the data contained in the operational database and data warehouse?* Data marts Data mining warehouse O OLAP O All of these answers are correct. If Company A wants to send Company B a secure message, Company A will use Company B's public key to encrypt the message. Company B must then docs.google.com If Company A wants to send Company B a secure message, Company A will use Company B's public key to encrypt the message. Company B must then * use Company A's public key to decrypt the message: O use its private key to decrypt the message. use Company A's private key to decrypt the message. O use its public key to decrypt the message. Privacy is a major issue in electronic transactions. Therefore, the Internet should not be used if O a bank uses a different digital signature for each denomination of currency. O digital signatures need to be issued for coins used in electronic transactions. the IP address of one of the parties to a O transaction needs to remain fully confidential All of these answers are correct. The protocol that specifies the format of all documents on the World Wide Web is O HTML O hyperlinks O URL ciphertext The technique that permits a bank to issue digital cash so that it is unable to link the payer to the payee is called O laundering money. O using a blinded digital signature. O using a generic digital signature. O digitized recycling. There are different types of electronic wallet-sized cards used in virtual cash transactions. ATM cards are classified as O shared-key cards O signature-creating cards. O memory cards. O signature-transporting cards. Which feature below would not be considered a highly convenient feature for consumers of an Internet store transaction? Consumers usually must wait for delivery of O items purchased via delivery by third parties. Internet store transactions can be O completed without any human intervention on the part of the vendor. Internet stores are "open" 24 x 7 with virtually worldwide access. O Internet stores accept most credit cards. docs.google.com Which statement below regarding keys is false? * Each user should create his or her own public and private keys. Using a central office authority to create and distribute keys is highly recommended. The longer the life of the key, the more security that must be applied to protect it. Sensitive keys should be themselves protected by passwords. One major difference between an organization's intranet and the Internet is the intranet may be totally unavailable to outsiders O the Internet may be totally unavailable to outsiders. an intranet user almost never can access the Internet. the Internet operates over a local area network docs.google.com A message which contains a digital signature O must be encrypted along with the signature must be it once as plaintext and once as ciphertext if no message digest exits. does not have to be encrypted when a O message digest is used as a digital signature O Answers B and C are correct. Which of the following contain subsets of the data contained in the operational database and data warehouse?* Data marts Data mining warehouse O OLAP O All of these answers are correct. If Company A wants to send Company B a secure message, Company A will use Company B's public key to encrypt the message. Company B must then docs.google.com If Company A wants to send Company B a secure message, Company A will use Company B's public key to encrypt the message. Company B must then * use Company A's public key to decrypt the message: O use its private key to decrypt the message. use Company A's private key to decrypt the message. O use its public key to decrypt the message. Privacy is a major issue in electronic transactions. Therefore, the Internet should not be used if O a bank uses a different digital signature for each denomination of currency. O digital signatures need to be issued for coins used in electronic transactions. the IP address of one of the parties to a O transaction needs to remain fully confidential All of these answers are correct. The protocol that specifies the format of all documents on the World Wide Web is O HTML O hyperlinks O URL ciphertext The technique that permits a bank to issue digital cash so that it is unable to link the payer to the payee is called O laundering money. O using a blinded digital signature. O using a generic digital signature. O digitized recycling