This is related to my Operating System Security course. Please include Linux demonstrations where possible so I can better understand. I'm not that familiar with linux yet and this practice lab is a good start to learn what's going on.
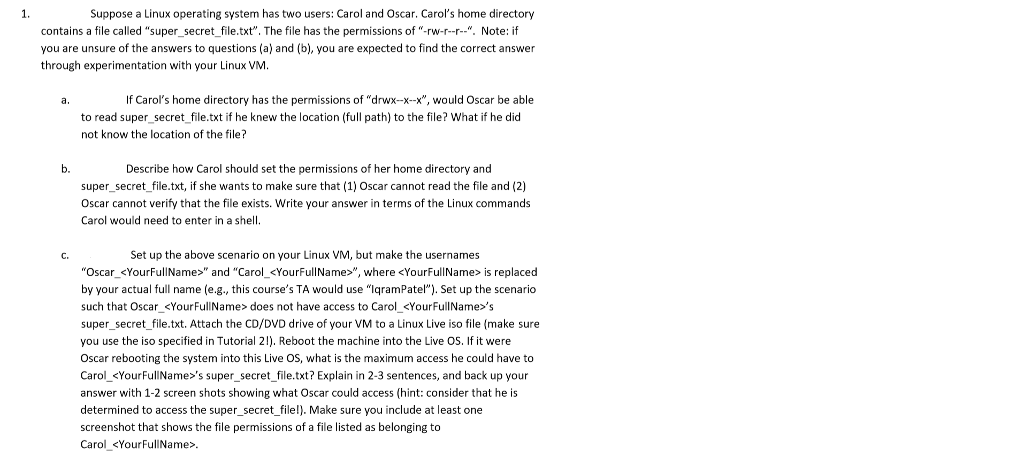
Suppose a Linux operating system has two users: Carol and Oscar. Carol's home directory contains a file called "super_secret file.txt". The file has the permissions of "-rw-r-r-". Note: if you are unsure of the answers to questions (a) and (b), you are expected to find the correct answer through experimentation with your Linux VM If Carol's home directory has the permissions of "drwx-x--x", would Oscar be able a. to read super_secret_file.txt if he knew the location (full path) to the file? What if he did not know the location of the file? b. Describe how Carol should set the permissions of her home directory and super_secret file.txt, if she wants to make sure that (1) Oscar cannot read the file and (2) Oscar cannot verify that the file exists. Write your answer in terms of the Linux commands Carol would need to enter in a shell C. Set up the above scenario on your Linux VM, but make the usernames "Oscar.
" and "Carol-", where is replaced by your actual full name (e.g., this course's TA would use "IqramPatel"). Set up the scenario such that Oscar does not have access to Carol 's super secret file.txt. Attach the CD/DVD drive of your VM to a Linux Live iso file (make sure you use the iso specified in Tutorial 21). Reboot the machine into the Live OS. If it were Oscar rebooting the system into this Live OS, what is the maximum access he could have to Carol 's super_secret file.txt? Explain in 2-3 sentences, and back up your answer with 1-2 screen shots showing what Oscar could access (hint: consider that he is determined to access the super_secret file!). Make sure you include at least one screenshot that shows the file permissions of a file listed as belonging to Carol Suppose a Linux operating system has two users: Carol and Oscar. Carol's home directory contains a file called "super_secret file.txt". The file has the permissions of "-rw-r-r-". Note: if you are unsure of the answers to questions (a) and (b), you are expected to find the correct answer through experimentation with your Linux VM If Carol's home directory has the permissions of "drwx-x--x", would Oscar be able a. to read super_secret_file.txt if he knew the location (full path) to the file? What if he did not know the location of the file? b. Describe how Carol should set the permissions of her home directory and super_secret file.txt, if she wants to make sure that (1) Oscar cannot read the file and (2) Oscar cannot verify that the file exists. Write your answer in terms of the Linux commands Carol would need to enter in a shell C. Set up the above scenario on your Linux VM, but make the usernames "Oscar." and "Carol-", where is replaced by your actual full name (e.g., this course's TA would use "IqramPatel"). Set up the scenario such that Oscar does not have access to Carol 's super secret file.txt. Attach the CD/DVD drive of your VM to a Linux Live iso file (make sure you use the iso specified in Tutorial 21). Reboot the machine into the Live OS. If it were Oscar rebooting the system into this Live OS, what is the maximum access he could have to Carol 's super_secret file.txt? Explain in 2-3 sentences, and back up your answer with 1-2 screen shots showing what Oscar could access (hint: consider that he is determined to access the super_secret file!). Make sure you include at least one screenshot that shows the file permissions of a file listed as belonging to Carol







