This Phase 5 of the Binary Bomb lab (x86 assembly).
I have gotten through the first 4 phases.
Basically, the objective is to find a secret answer that defuses the bomb (aka is able to go through the phase without calling explode_bomb). Can someone please explain and translate the assembly?
I am struggling to know where to look and what to do
What I ALREADY know:
- Lines 24, 29, 32 check if the length of the inputted string is 6 characters. If it is not, then explode. Thus, I KNOW that the input string must be 6 characters long.
What I am struggling with is how I can go from there to figure out the answer that would defuse the bomb.
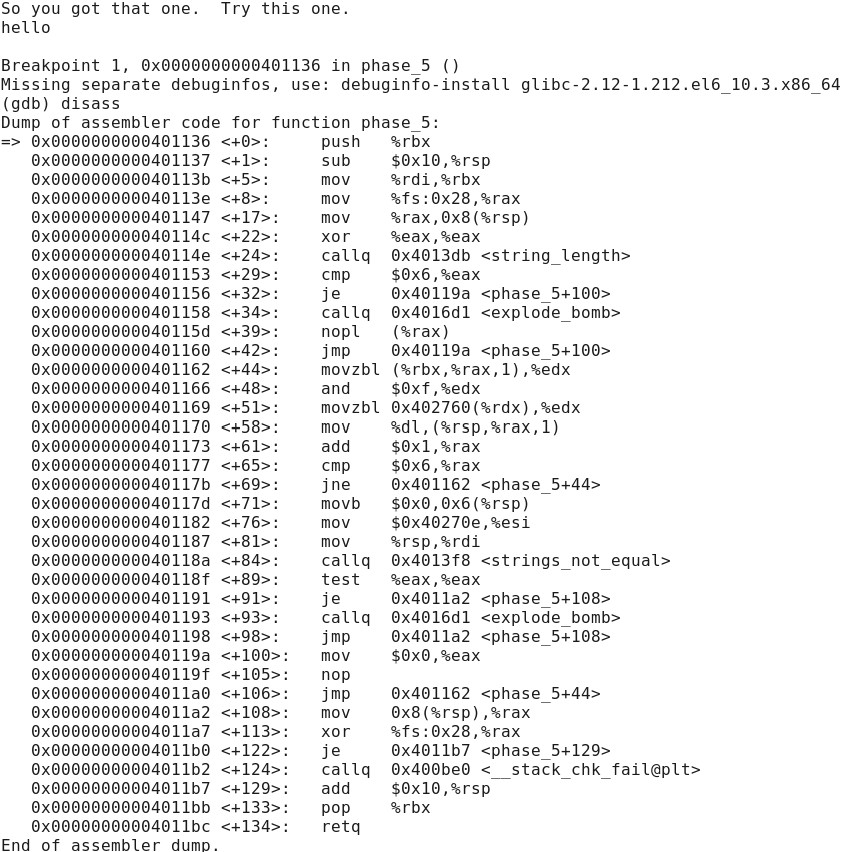
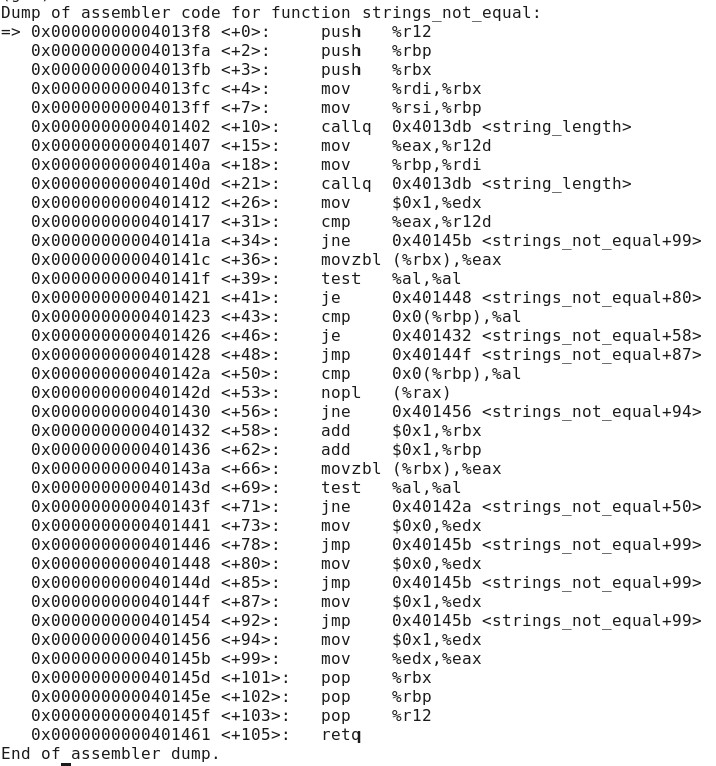
so you got that one. Try this one. hello je mov Breakpoint 1, 0x0000000000401136 in phase 5 () Missing separate debuginfos, use: debuginfo-install glibc-2.12-1.212.el6 10.3.x86 64 (gdb) disass Dump of assembler code for function phase 5: => 0x0000000000401136 : push %rbx OX0000000000401137 : sub $0x10,%rsp Ox000000000040113b : mov %rdi,%rbx Ox000000000040113e : mov %fs: 0x28,%rax Ox0000000000401147 : mov %rax, 0x8(%rsp) Ox0000000000401140 : xor %eax , %eax Ox000000000040114e : callqOX4013db
Ox0000000000401153 : cmp $ Ox6, %eax Ox0000000000401156 : 0x40119a Ox0000000000401158 : calla Ox4016dl Ox000000000040115d : nopl (%rax) OX0000000000401160 : jmp 0x40119a OX0000000000401162 : movzbl (%rbx, frax,1),%edx Ox0000000000401166 : and $Oxf, %edx Ox0000000000401169 : movzbl Ox402760(%rdx), %edx Ox0000000000401170 : %dl, (%rsp,%rax, 1) OX0000000000401173 : add $0x1,%rax OX0000000000401177 : cmp $0x6,%rax Ox000000000040117b : jne Ox401162 Ox000000000040117d : movb $0x0, 0x6(%rsp) Ox0000000000401182 : mov $0x40270e, Sesi OX0000000000401187 : mov %rsp,%rdi OX000000000040118a : calla 0x4013f8 Ox000000000040118f : test %eax, Seax OX0000000000401191 : je 0x4011a2 Ox0000000000401193 : calla Ox4016dl Ox0000000000401198 : jmp Ox4011a2 Ox000000000040119a : mov $0x0,%eax OX000000000040119f : nop OX00000000004011a : jmp Ox401162 Ox00000000004011a2 : mov 0x8(%rsp), %rax Ox00000000004011a7 : xor %fs: 0x28,%rax OX0000000000401160 : je 0x4011b7 Ox00000000004011b2 : callqOX400be0 Ox00000000004011b7 add $0x10,%rsp Ox00000000004011bb : pop rbx OX00000000004011bc : reta End of assembler dump Dump of assembler code for function strings not equal: => 0x00000000004013f8 : push %r12 Ox00000000004013fa : push frbp Ox00000000004013fb : push rbx Ox00000000004013fc : mov %rdi, Srbx Ox00000000004013ff : mov %rsi, Srbp OX0000000000401402 : 0x4013db OX0000000000401407 : mov Seax, %r12d Ox000000000040140a : mov %rbp,%rdi Ox000000000040140d : calla Ox4013db Ox0000000000401412 : mov $0x1, %edx OX0000000000401417 : cmp %eax,%r12d OX000000000040141a : jne 0x40145b Ox000000000040141c : movzbl (%rbx), %eax Ox000000000040141f : test %al, %al Ox0000000000401421 : je 0x401448 Ox0000000000401423 : cmp OxO (%rbp), %al Ox0000000000401426 : je OX401432 OX0000000000401428 : jmp OX40144f OX000000000040142a : cmp Ox0(%rbp), sal Ox000000000040142d : nopl (%rax) Ox0000000000401430 : jne Ox401456 Ox0000000000401432 : add $0x1,%rbx OX0000000000401436 : add $0x1,%rbp Ox000000000040143a : movzbl (%rbx), %eax Ox000000000040143d : test al, sal OX000000000040143f : jne 0x40142a OX0000000000401441 : mov $ 0x0, %edx OX0000000000401446 : imp OX40145b Ox0000000000401448 : mov $ 0x0,%edx Ox000000000040144d : 0x40145b OX000000000040144f : mov $0x1, %edx Ox0000000000401454 : jmp 0x40145b Ox0000000000401456 ; mov $0x1, %edx OX000000000040145b : mov %edx , %eax OX000000000040145d : pop OX000000000040145e : pop %rbp Ox000000000040145f : pop %r12 Ox0000000000401461 : reta End of assembler dump. jmp %rbx so you got that one. Try this one. hello je mov Breakpoint 1, 0x0000000000401136 in phase 5 () Missing separate debuginfos, use: debuginfo-install glibc-2.12-1.212.el6 10.3.x86 64 (gdb) disass Dump of assembler code for function phase 5: => 0x0000000000401136 : push %rbx OX0000000000401137 : sub $0x10,%rsp Ox000000000040113b : mov %rdi,%rbx Ox000000000040113e : mov %fs: 0x28,%rax Ox0000000000401147 : mov %rax, 0x8(%rsp) Ox0000000000401140 : xor %eax , %eax Ox000000000040114e : callqOX4013db Ox0000000000401153 : cmp $ Ox6, %eax Ox0000000000401156 : 0x40119a Ox0000000000401158 : calla Ox4016dl Ox000000000040115d : nopl (%rax) OX0000000000401160 : jmp 0x40119a OX0000000000401162 : movzbl (%rbx, frax,1),%edx Ox0000000000401166 : and $Oxf, %edx Ox0000000000401169 : movzbl Ox402760(%rdx), %edx Ox0000000000401170 : %dl, (%rsp,%rax, 1) OX0000000000401173 : add $0x1,%rax OX0000000000401177 : cmp $0x6,%rax Ox000000000040117b : jne Ox401162 Ox000000000040117d : movb $0x0, 0x6(%rsp) Ox0000000000401182 : mov $0x40270e, Sesi OX0000000000401187 : mov %rsp,%rdi OX000000000040118a : calla 0x4013f8 Ox000000000040118f : test %eax, Seax OX0000000000401191 : je 0x4011a2 Ox0000000000401193 : calla Ox4016dl Ox0000000000401198 : jmp Ox4011a2 Ox000000000040119a : mov $0x0,%eax OX000000000040119f : nop OX00000000004011a : jmp Ox401162 Ox00000000004011a2 : mov 0x8(%rsp), %rax Ox00000000004011a7 : xor %fs: 0x28,%rax OX0000000000401160 : je 0x4011b7 Ox00000000004011b2 : callqOX400be0 Ox00000000004011b7 add $0x10,%rsp Ox00000000004011bb : pop rbx OX00000000004011bc : reta End of assembler dump Dump of assembler code for function strings not equal: => 0x00000000004013f8 : push %r12 Ox00000000004013fa : push frbp Ox00000000004013fb : push rbx Ox00000000004013fc : mov %rdi, Srbx Ox00000000004013ff : mov %rsi, Srbp OX0000000000401402 : 0x4013db OX0000000000401407 : mov Seax, %r12d Ox000000000040140a : mov %rbp,%rdi Ox000000000040140d : calla Ox4013db Ox0000000000401412 : mov $0x1, %edx OX0000000000401417 : cmp %eax,%r12d OX000000000040141a : jne 0x40145b Ox000000000040141c : movzbl (%rbx), %eax Ox000000000040141f : test %al, %al Ox0000000000401421 : je 0x401448 Ox0000000000401423 : cmp OxO (%rbp), %al Ox0000000000401426 : je OX401432 OX0000000000401428 : jmp OX40144f OX000000000040142a : cmp Ox0(%rbp), sal Ox000000000040142d : nopl (%rax) Ox0000000000401430 : jne Ox401456 Ox0000000000401432 : add $0x1,%rbx OX0000000000401436 : add $0x1,%rbp Ox000000000040143a : movzbl (%rbx), %eax Ox000000000040143d : test al, sal OX000000000040143f : jne 0x40142a OX0000000000401441 : mov $ 0x0, %edx OX0000000000401446 : imp OX40145b Ox0000000000401448 : mov $ 0x0,%edx Ox000000000040144d : 0x40145b OX000000000040144f : mov $0x1, %edx Ox0000000000401454 : jmp 0x40145b Ox0000000000401456 ; mov $0x1, %edx OX000000000040145b : mov %edx , %eax OX000000000040145d : pop OX000000000040145e : pop %rbp Ox000000000040145f : pop %r12 Ox0000000000401461 : reta End of assembler dump. jmp %rbx








