Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Trudy Security Handshake Pitfalls Mutual Authentication Password Guessing Another weakness: Trudy can mount an offline password-guessing without needing to eavesdrop To fix it, make
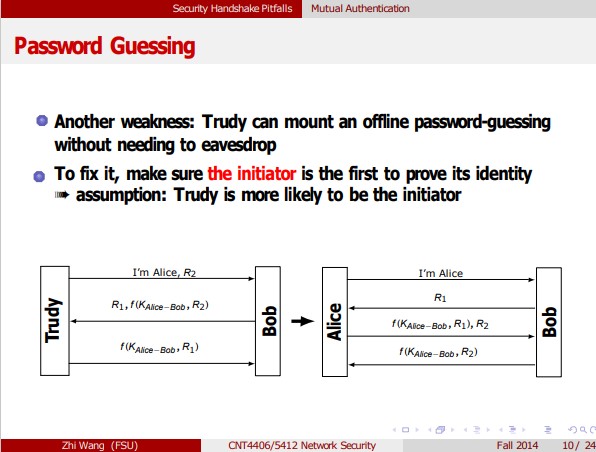
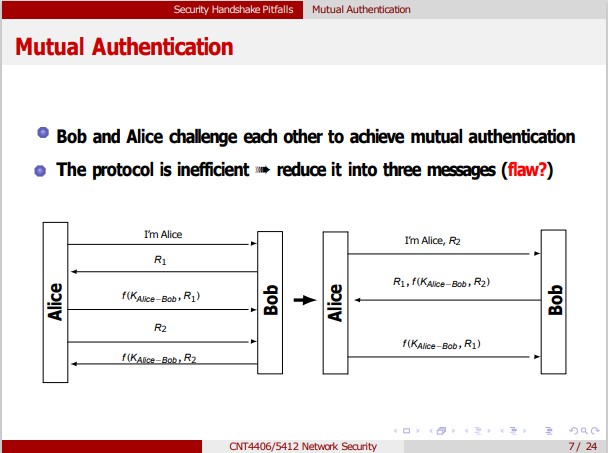
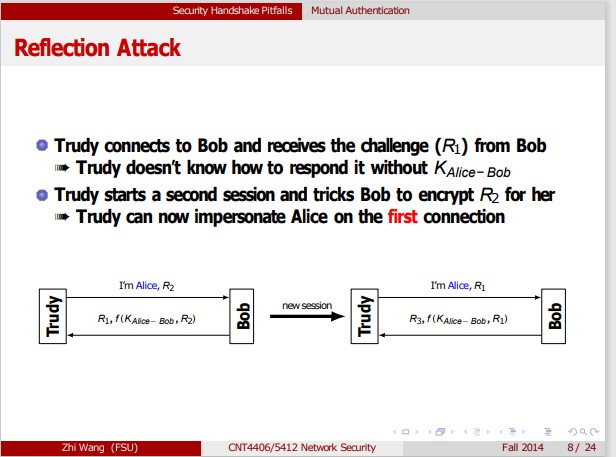
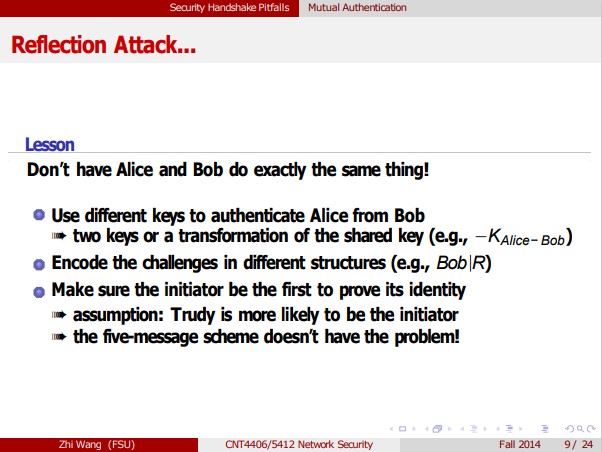
Trudy Security Handshake Pitfalls Mutual Authentication Password Guessing Another weakness: Trudy can mount an offline password-guessing without needing to eavesdrop To fix it, make sure the initiator is the first to prove its identity assumption: Trudy is more likely to be the initiator I'm Alice, R2 R1, f(KAlice-Bob, R2) f(K Alice-Bob, R1) Bob Alice I'm Alice R1 f(KAlice-Bob, R1), R2 f(KAlice-Bob, R2) Zhi Wang (FSU) CNT4406/5412 Network Security Fall 2014 10/24 Bob nac Alice Security Handshake Pitfalls Mutual Authentication Mutual Authentication Bob and Alice challenge each other to achieve mutual authentication The protocol is inefficient reduce it into three messages (flaw?) I'm Alice R1 f(KAlice-Bob R1) R2 f(KAlice-Bob,R2 Bob + Alice CNT4406/5412 Network Security I'm Alice, R2 R1, f(KAlice-Bob, R2) f(KAlice-Bob, R1) Bob 592 7/24 Trudy Security Handshake Pitfalls Mutual Authentication Reflection Attack Trudy connects to Bob and receives the challenge (R1) from Bob Trudy doesn't know how to respond it without KAlice-Bob Trudy starts a second session and tricks Bob to encrypt R for her Trudy can now impersonate Alice on the first connection I'm Alice, R R1, f(KAlice-Bob, R) Bob new session Trudy I'm Alice, R1 R3, f(KAlice-Bob, R) = 590 Zhi Wang (FSU) CNT4406/5412 Network Security Fall 2014 8/24 Bob Security Handshake Pitfalls Mutual Authentication Reflection Attack... Lesson Don't have Alice and Bob do exactly the same thing! Use different keys to authenticate Alice from Bob two keys or a transformation of the shared key (e.g., -KAlice-Bob) Encode the challenges in different structures (e.g., Bob |R) Make sure the initiator be the first to prove its identity assumption: Trudy is more likely to be the initiator the five-message scheme doesn't have the problem! Ja Zhi Wang (FSU) CNT4406/5412 Network Security Fall 2014 9/24
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


