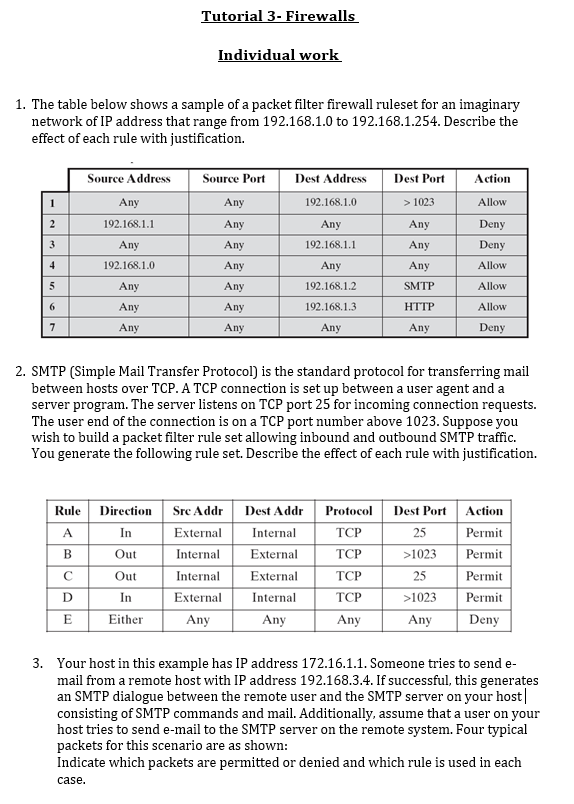
Tutorial 3- Firewalls Individual work 1. The table below shows a sample of a packet filter firewall ruleset for an imaginary network of IP address that range from 192.168.1.0 to 192.168.1.254. Describe the effect of each rule with justification. Action 1 Allow Source Address Any 192.168.1.1 Any 2 Deny Deny Source Port Any Any Any Any Any Any Any Dest Port > 1023 Any Any Any 3 Dest Address 192.168.1.0 Any 192.168.1.1 Any 192.168.1.2 192.168.1.3 Any 4 192.168.1.0 Allow 5 Any SMTP Allow 6 Any HTTP Allow 7 Any Any Deny 2. SMTP (Simple Mail Transfer Protocol) is the standard protocol for transferring mail between hosts over TCP. A TCP connection is set up between a user agent and a server program. The server listens on TCP port 25 for incoming connection requests. The user end of the connection is on a TCP port number above 1023. Suppose you wish to build a packet filter rule set allowing inbound and outbound SMTP traffic. You generate the following rule set. Describe the effect of each rule with justification. Rule Direction Sre Addr Dest Addr Protocol A In External Internal TCP B Out Internal External TCP Out Internal External TCP D In External Internal TCP E Either Any Any Any Dest Port Action 25 Permit >1023 Permit 25 Permit >1023 Permit Any Deny 3. Your host in this example has IP address 172.16.1.1. Someone tries to send e- mail from a remote host with IP address 192.168.3.4. If successful, this generates an SMTP dialogue between the remote user and the SMTP server on your host| consisting of SMTP commands and mail. Additionally, assume that a user on your host tries to send e-mail to the SMTP server on the remote system. Four typical packets for this scenario are as shown: Indicate which packets are permitted or denied and which rule is used in each case. Sre Addr Protocol Dest Port Action Packet Direction 1 In 2 Out TCP 25 ? Dest Addr 172.16.1.1 192.168.3.4 192.168.3.4 172.16.1.1 TCP 1234 192.168.3.4 172.16.1.1 172.16.1.1 192.168.3.4 ? 3 Out TCP 25 ? 4 In TCP 1357 ? 4. Someone from the outside world (10.1.2.3) attempts to open a connection from port 5150 on a remote host to the Web proxy server on port 8080 on one of your local hosts (172.16.3.4), in order to carry out an attack. Typical packets are as follows: Will the attack succeed? Give details with justification. Action Packet Direction Sre Addr 5 In 10.1.23 Out 172.16.3.4 Dest Addr Protocol Dest Port 172.16.3.4 TCP 8080 10.1.2.3 TCP 5150 ? 6








