Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Use your cursor to match each example of a typical risk with the control that may be used to mitigate the risk in an
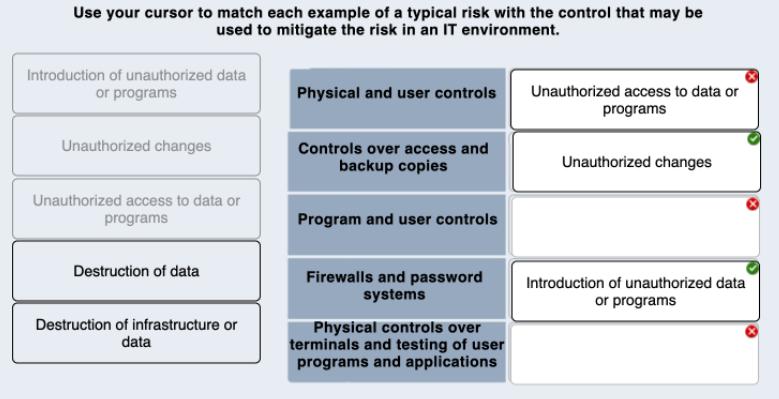
Use your cursor to match each example of a typical risk with the control that may be used to mitigate the risk in an IT environment. Introduction of unauthorized data or programs Physical and user controls Unauthorized access to data or programs Unauthorized changes Controls over access and backup copies Unauthorized changes Unauthorized access to data or programs Program and user controls Destruction of data Firewalls and password systems Introduction of unauthorized data or programs Destruction of infrastructure or Physical controls over terminals and testing of user programs and applications data
Step by Step Solution
★★★★★
3.50 Rating (160 Votes )
There are 3 Steps involved in it
Step: 1
Physical and user controls Unauthorized access to data or programs Destruction of infrastruct...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


