Question
Using the formula on page 163, calculate the post-ARO, post -ALE, and CBA using the table found in exercise 5 at the end of Module
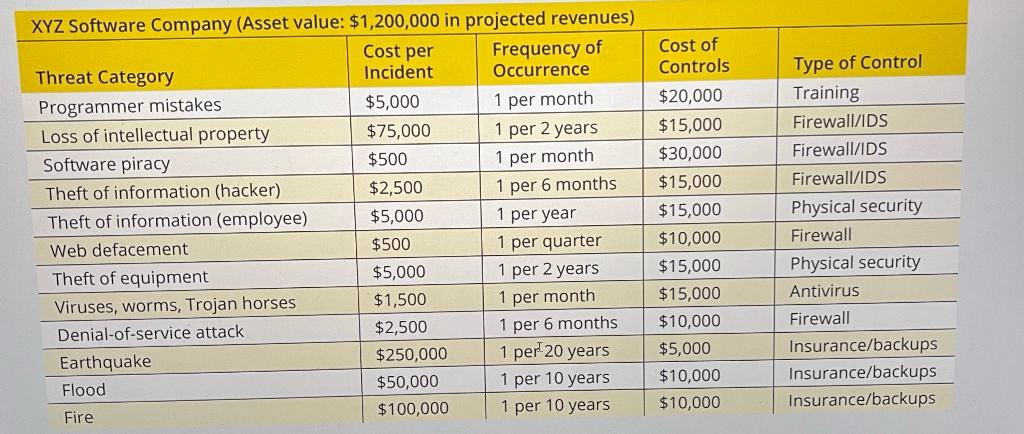
Using the formula on page 163, calculate the post-ARO, post -ALE, and CBA using the table found in exercise 5 at the end of Module 4. The pre-control numbers are from exercise 2 above. Assume the Cost per Incident is the SLE. I suggest you use an excel spreadsheet. Please note that Exercise 5 continues on page 174 where you are asked to determine if based on the CBA, the cost of the control was worth the expense.
Formula on page 163: CBA = ALE(pre-control) - ALE(post-control) - ACS
The table found in exercise 5 is attached below.
Pre-control numbers from exercise 2: Programmer mistakes: ARO: 52, ALE = 5,000*52 = 260,000 Loss of Intellectual Property: ARO = 1, ALE = 75,000 * 1 = 75,000 Software Piracy: ARO = 52, ALE = 500 * 52 = 26,000 Theft of information (hacker): ARO = 4, ALE = 2500 * 4 = 10,000 Theft of information (employee): ARO: 2, ALE = 5000* 2 = 10,000 Web defacement: ARO = 12, ALE = 500 * 12 = 6,000 Theft of equipment: ARO = 1, ALE = 5000 * 1 = 5,000 Viruses, worms, Trojan horses: ARO = 52, ALE = 1500 * 52 = 78,000 Denial-of-service attacks: ARO = 4, ALE = 2500 * 4 = 10,000 Earthquake: ARO = 0.05, ALE: 250,000 * 0.05 = 12,500 Flood: ARO = 0.1, ALE = 250,000 * 0.1 = 25,000 Fire: ARO = 0.1, ALE: 500,000 * 0.1 = 50,000
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


