Question
Using the Security models listed below place each model into the appropriate lock box. Each Lock represents data in transit, and you have to
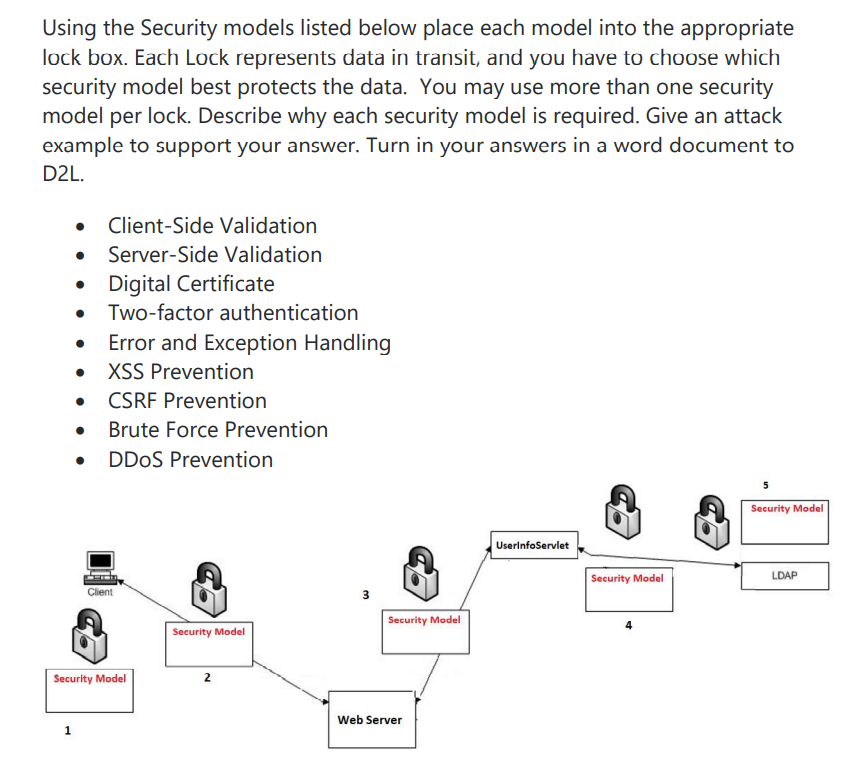
Using the Security models listed below place each model into the appropriate lock box. Each Lock represents data in transit, and you have to choose which security model best protects the data. You may use more than one security model per lock. Describe why each security model is required. Give an attack example to support your answer. Turn in your answers in a word document to D2L. . Client-Side Validation Server-Side Validation Digital Certificate Two-factor authentication Error and Exception Handling XSS Prevention CSRF Prevention Brute Force Prevention DDoS Prevention Client Security Model Security Model 2 1 3 Security Model Web Server 5 Security Model UserInfoServlet Security Model LDAP
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get StartedRecommended Textbook for
Income Tax Fundamentals 2013
Authors: Gerald E. Whittenburg, Martha Altus Buller, Steven L Gill
31st Edition
1111972516, 978-1285586618, 1285586611, 978-1285613109, 978-1111972516
Students also viewed these Computer Network questions
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
Question
Answered: 1 week ago
View Answer in SolutionInn App



