Answered step by step
Verified Expert Solution
Question
1 Approved Answer
were to make a code specifically in python, although im used fo java im still a little lost with python. i also dont quite understand
were to make a code specifically in python, although im used fo java im still a little lost with python. i also dont quite understand fully how to set up the code, where to start, and what its supposed to look like. any help would be appreciated 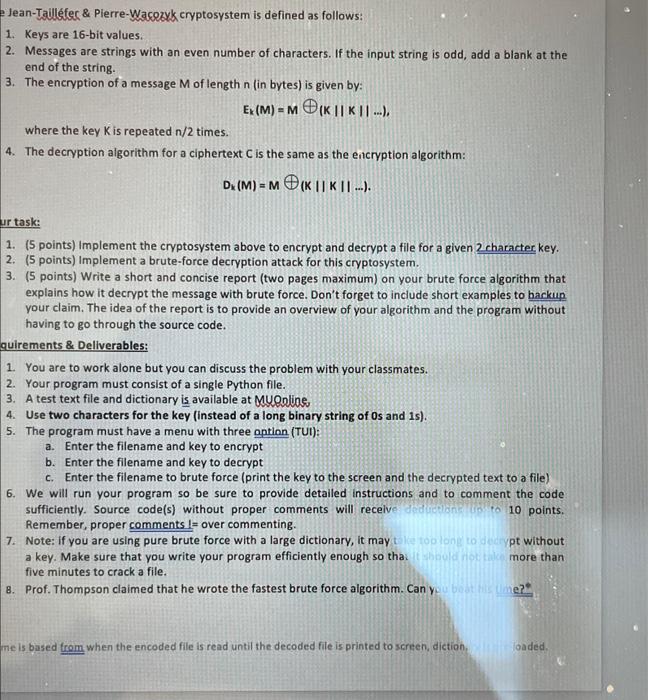
Jean-Tailfec \& Pierre-Wacoryk cryptosystem is defined as follows: 1. Keys are 16-bit values. 2. Messages are strings with an even number of characters. If the input string is odd, add a blank at the end of the string. 3. The encryption of a message M of length n (in bytes) is given by: EK(M)=M(KK. where the key K is repeated n/2 times. 4. The decryption algorithm for a ciphertext C is the same as the encryption algorithm: Dk(M)=M(KK) 1. (5 points) Implement the cryptosystem above to encrypt and decrypt a file for a given 2 character key. 2. (5 points) Implement a brute-force decryption attack for this cryptosystem. 3. (5 points) Write a short and concise report (two pages maximum) on your brute force algorithm that explains how it decrypt the message with brute force. Don't forget to include short examples to backup your claim. The idea of the report is to provide an overview of your algorithm and the program without having to go through the source code. quirements \& Deliverables: 1. You are to work alone but you can discuss the problem with your classmates. 2. Your program must consist of a single Python file. 3. A test text file and dictionary is available at MuQoline, 4. Use two characters for the key (instead of a long binary string of Os and 1s). 5. The program must have a menu with three ontion (TUI): a. Enter the filename and key to encrypt b. Enter the filename and key to decrypt c. Enter the filename to brute force (print the key to the screen and the decrypted text to a file) 6. We will run your program so be sure to provide detailed instructions and to comment the code sufficiently. Source code(s) without proper comments will recelve dedfcting is 10 points. Remember, proper comments I= over commenting. 7. Note: if you are using pure brute force with a large dictionary, it may pt without a key. Make sure that you write your program efficiently enough so thai inculdiof than five minutes to crack a file. 8. Prof. Thompson claimed that he wrote the fastest brute force algorithm. Can y. me is based from when the encoded file is read until the decoded file is printed to screen, diction. oaded 
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


