Answered step by step
Verified Expert Solution
Question
1 Approved Answer
what are the correct options? Attack Description An attacker sends mutople SYN packets from multiple sources The attack establishes a connection, which allows remote commands
what are the correct options?
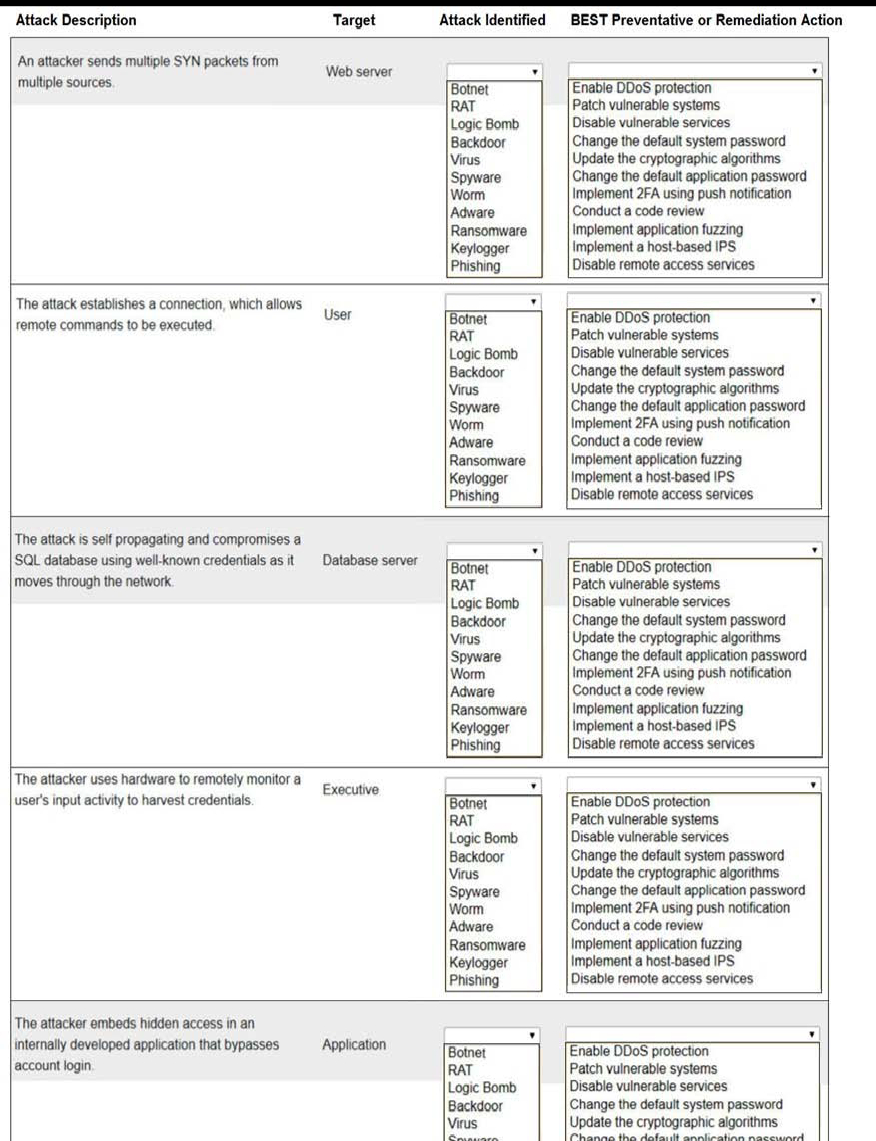
Attack Description An attacker sends mutople SYN packets from multiple sources The attack establishes a connection, which allows remote commands to be executed L The attack self propagating and compromses a SOL database well-known credentials as It moves throton the network The attacker uses hardware to remotely monitor a user's Input activity to harvest credentials. The attacker embeds hidden access in an internally developed applicabon trut bypasses account login Target Web server Database server Application Attack Identified RAT Logic Backdoor Ransomware Phishing RAT Logr Bomb Keylogger Phishing RAT lc Bomb Backdoor Spyware Ransomware Phishing RAT Logic Bomb Worm Adware Ransomware KylOf Ptusnng Botnet RAT Logit Bomb Backdoor BEST Preventative or Remediation Action nable protecton Patch vulnerable systems Disable vulnerable servces Change the default system password Update the algorithms Change the default application password Implement 2FA using push notJficat10n Conduct a code review Implement applcatlon Implement a host-based IPS Disable remote access semces Enable DDOS protection Patch vulnerable systems Disable vulnerable semces Change the default system password Update the cryptographic algorithms Change the delault application password Implement 2FA using push notification Conduct a code review Implement application fuzmg Implement a host-based IPS Disable remote access services nable DDoS protection Patch vulnerable systems Disable vulnerable services Change the default system password Update the cryptographic algorithms Change the default application password Implement 2FA using push Conduct a code review Implement appltcatlon fuzzing implement a host-based IPS Disable remote access services Enable DDOS protection Patch vulnerable systems Disable vulnerable semceS Change the default System password Update the cryptographic algorithms Change the default application password Implernent 2FA usng push notification Conduct a code rewew Implement application fuznng Implement a host-based IPS Disable remote access services Enable DDoS protection Patch vulnerable systems Disable vulnerable services Change the default system password Update the algonthms
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


