Answered step by step
Verified Expert Solution
Question
1 Approved Answer
without multipltion and division Write a MIPS assembly program that reads the size (n) of the message from the user. Then, the program allocates (n+1)
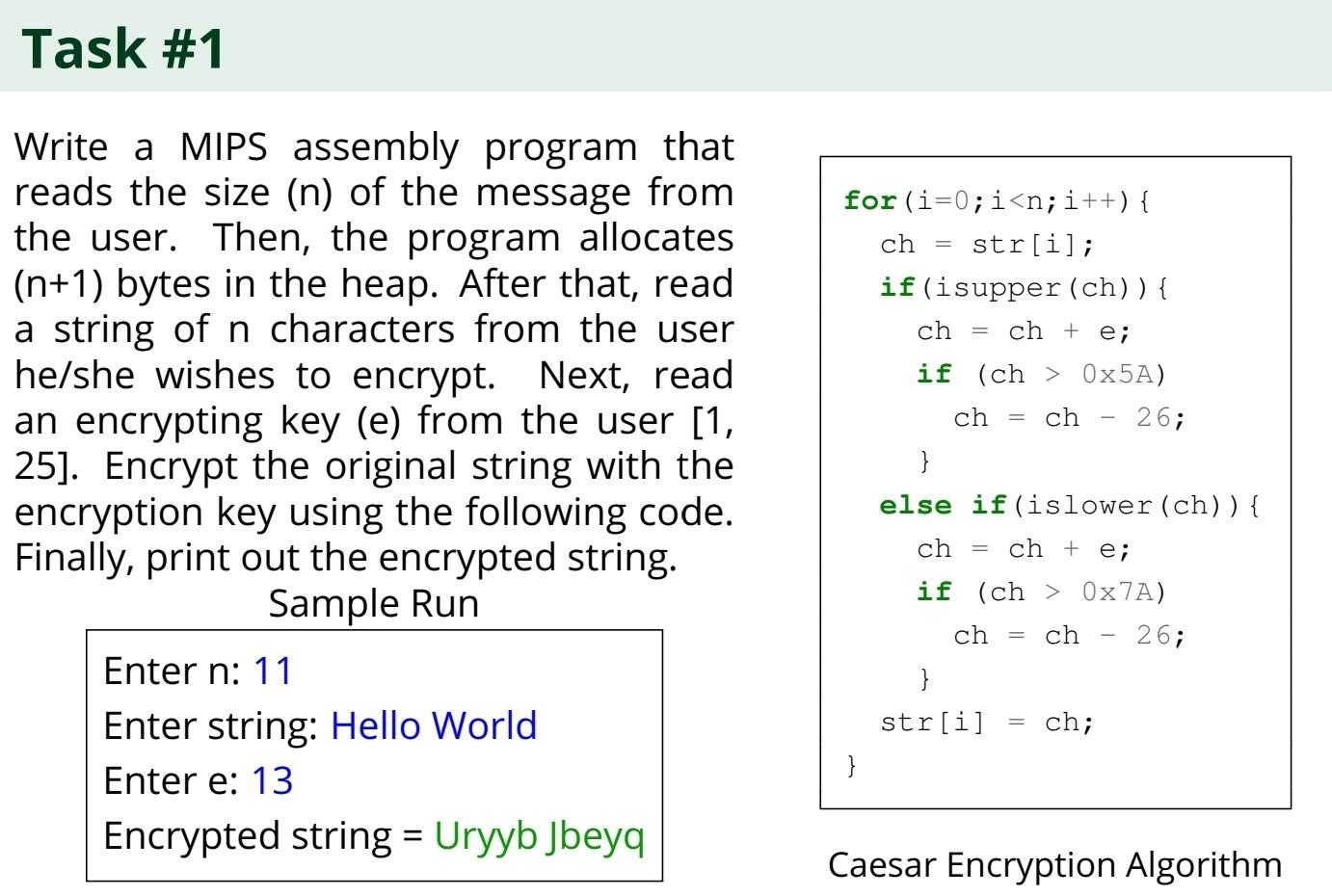
without multipltion and division
Write a MIPS assembly program that reads the size (n) of the message from the user. Then, the program allocates (n+1) bytes in the heap. After that, read a string of n characters from the user he/she wishes to encrypt. Next, read an encrypting key (e) from the user [1, 25]. Encrypt the original string with the encryption key using the following code. Finally, print out the encrypted string. Sample Run \begin{tabular}{|l|} \hline Enter n:11 \\ Enter string: Hello World \\ Enter e: 13 \\ Encrypted string = Uryyb Jbeyq \\ \hline \end{tabular} for (i=0;iStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


