Question
You are a security researcher for your organization and it is your job to test software that other have authored. You have received a function
You are a security researcher for your organization and it is your job to test software that other have authored. You have received a function that verifies entered passwords as a packaged program verify pass (along with its source code). This program takes two strings (passwords) and returns if those passwords are the same. The function will be later used to verify the passwords that users enter when they setup a password. This application has several bugs. For the purpose of this assignment, you are required to exploit the buffer overflow vulnerability so that the program says that the entered passwords are the same when they are not the same. You are required to submit a shell script, verify pass.sh, that invokes verify passs with appropriate arguments to exploit this vulnerability. For testing purposes, you can assume that the verify pass program resides in the same folder as the shell script.
Question2:
Privilege Escalation create code and submit a is log file.sh file that takes no arguments and writes a malicious log file. This malicious log file will be provided as an argument to is log file program (This program has suid bit set) and it should exploit a buffer overflow to provide root access. The program should do so without crashing or unclean exit. Your script should do so without crashing or unclean exit. For testing purposes, you can assume that the is log file program resides in the same folder as the script.
Setup the Environment Working Environment: For the purpose of this assignment, you will be working on a Ubuntu 14 VM image for VMware, which has been provided. You can download those from https://uoguelphca-my.sharepoint.com/:u:/g/personal/hkhan15_uoguelph_ca/EaGfuaohquNJtrc5tIIE5aoB1605WLUH3wpmDyTMAgn8Qw? e=akgpXR The username and password are 'uog-sec' and 'uogsec', respectively. It is recommended that you use the executables and source code provided under the folder "/home/uogsec/buffer overflow". Your exploit will be tested against those. In case you need to recompile with gdb flag on, please remember that the executable has suid bit set, and two parameters have been provided to gcc -fno-stack-protector and -z execstack and kernel.randomize va space is set to 0. If you feel that something is off and your code is not working, please confirm that ASLR is disabled and the programs have been compiled with right parameters and permissions. Note that the image is 32-bit.
I will upload the professor's nots in below :
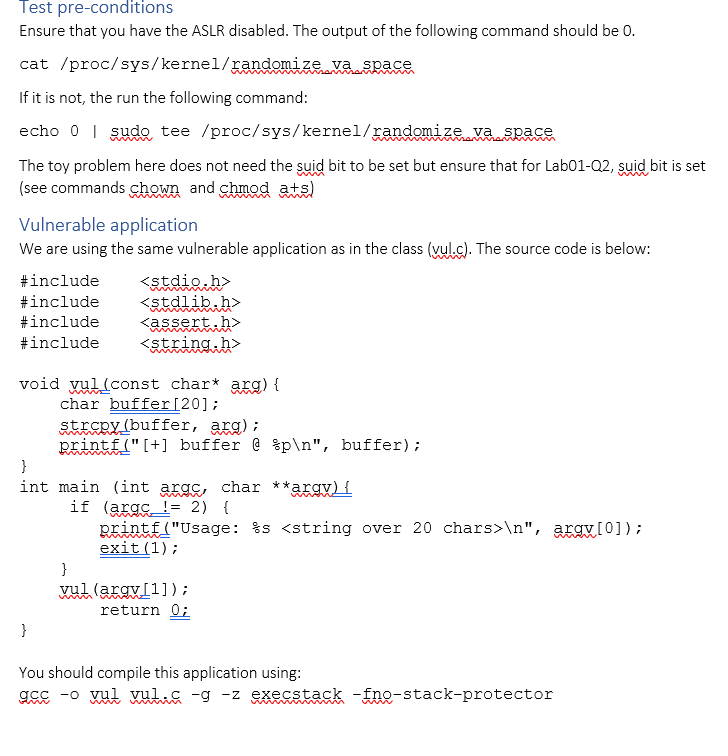
Test pre-conditions Ensure that you have the ASLR disabled. The output of the following command should be 0. cat /proc/sys/kernel/randomize va space If it is not, the run the following command: echo 0 1 sudo, tee /proc//sys/kernel/randomize va space The toy problem here does not need the suid bit to be set but ensure that for Lab01-Q2, suid bit is set (see commands chown and chmod ats) Vulnerable application We are using the same vulnerable application as in the class (vul.c). The source code is below: #include #include #include #include void vul(const char* arg) { char buffer [20]; strcpy (buffer, arg); printf("[+] buffer @p ", buffer); } int main (int argc, char **argv) { if (argc != 2) { printf("Usage: %s ", argv[0]); exit (1); } } vul (argv[1]); return 0; You should compile this application using: gcc -o vul vul.c -g -z execstack -fno-stack-protector
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


