Refer to Exercise 6.3. Are X and Y independent? Data from Exercise 6.3 Refer to the IEEE
Question:
Refer to Exercise 6.3. Are X and Y independent?
Data from Exercise 6.3
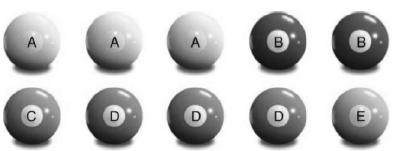
Refer to the IEEE Transactions on Information Forensics and Security (March 2013) study of wireless identify theft using cloned credit or debit cards. A cloning detection method was illustrated using a simple ball drawing game. Consider the group of 10 balls shown below. Of these, 5 represent genuine credit/debit cards and 5 represent clones of one or more of these cards. The 5 letters—A, B, C, D, and E—were used to distinguish among the different genuine cards. (Balls with the same letter represent either the genuine card or a clone of the card.) For this illustration, let X represent the number of genuine balls selected and Y represent the number of B-lettered balls selected when 2 balls are randomly drawn (without replacement) from the 10 balls.
Step by Step Answer:

Statistics For Engineering And The Sciences
ISBN: 9781498728850
6th Edition
Authors: William M. Mendenhall, Terry L. Sincich





