A user keys a URL into their browser and hits the key. a) Re-order the following stages,
Question:
A user keys a URL into their browser and hits the key.
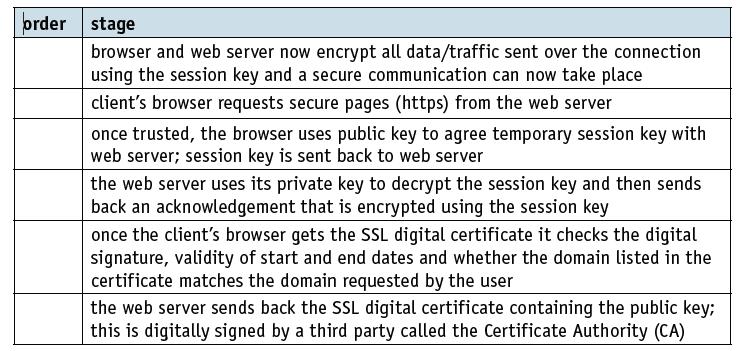
a) Re-order the following stages, 1-6, to show how an SSL digital certificate is used to set up a secure connection between client (user) and website.
b) List four items found on a digital certificate.
c) Explain how a digital signature can be formed from a digital certificate.
Transcribed Image Text:
order stage browser and web server now encrypt all data/traffic sent over the connection using the session key and a secure communication can now take place client's browser requests secure pages (https) from the web server once trusted, the browser uses public key to agree temporary session key with web server; session key is sent back to web server the web server uses its private key to decrypt the session key and then sends back an acknowledgement that is encrypted using the session key once the client's browser gets the SSL digital certificate it checks the digital signature, validity of start and end dates and whether the domain listed in the certificate matches the domain requested by the user the web server sends back the SSL digital certificate containing the public key3; this is digitally signed by a third party called the Certificate Authority (CA)
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 42% (7 reviews)
a Reorder the following stages 16 to show how an SSL digital certificate is used to set up a secure ...View the full answer

Answered By

Churchil Mino
I have been a tutor for 2 years and have experience working with students of all ages and abilities. I am comfortable working with students one-on-one or in small groups, and am able to adapt my teaching style to meet the needs of each individual. I am patient and supportive, and my goal is to help my students succeed.
I have a strong background in math and science, and have tutored students in these subjects at all levels, from elementary school to college. I have also helped students prepare for standardized tests such as the SAT and ACT. In addition to academic tutoring, I have also worked as a swim coach and a camp counselor, and have experience working with children with special needs.
0.00
0 Reviews
10+ Question Solved
Related Book For 

Cambridge International AS & A Level Computer Science
ISBN: 9781510457591
1st Edition
Authors: David Watson, Helen Williams
Question Posted:
Students also viewed these Computer science questions
-
How many strings of length 8 can be formed from the letters A, B, C, D, and E ? How many of the strings have at least one E?
-
How many distinguishable code symbols can be formed from the letters of the word BUSINESS? BIOLOGY? MATHEMATICS?
-
How many 2-letter code words can be formed from the first 3 letters of the alphabet if no letter can be used more than once? Solve Problem two ways: (A) Using a tree diagram, and (B) Using the...
-
An astronaut must journey to a distant planet, which is 200 light-years from Earth. What speed will be necessary if the astronaut wishes to age only 10 years during the round trip?
-
Given that x is a normal variable with mean = 47 and standard deviation = 6.2, find: (a) P(x 60) (b) P(x 50) (c) P(50 x 60)
-
Determine a hypothesis that the following data may address and perform a x2 test on the survey data. a. American Idol should be broadcast before 9 p.m. Agree 40 Neutral 35 Disagree 25 100 b....
-
2. Hen Corporations revenues for the year ended December 31, 2016, are as follows (in thousands): Consolidated revenue per income statement $1,200 Intersegment sales 180 Intersegment transfers 60...
-
Relating profitability to financial leverage a. Compute the rule of return on common shareholders' equity in each of the following independent cases. b. In which cases is financial 1everai'e working...
-
Required information [The following information applies to the questions displayed below) Tunstall, Inc., a small service company, keeps its records without the help of an accountant. After much...
-
Scully Corporations comparative balance sheets are presented below. Additional information: 1. Net income was $22,630. Dividends declared and paid were $19,500. 2. All other changes in noncurrent...
-
a) Explain the terms SSL and TLS. b) Explain the following terms used in TLS. i) Record protocol ii) Handshake protocol iii) Session caching c) Give two differences between SSL and TLS.
-
a) Answer these multiple choice questions. i) Identify the statement that best describes artificial intelligence. A. Putting human intelligence into a computer system B. Programming a computer using...
-
You have been asked to advise the 2012 London Olympics team on running the games. Firstly, is this a project or a programme and why?
-
Once the largest professional services firm in the world and arguably the most respected, Arthur Andersen LLP (AA) has disappeared. The Big 5 accounting firms are now the Big 4. Why did this happen?...
-
Fill in the Blank. Piezoelectric transducers generate electrical ______________ when subjected to mechanical stress.
-
A clockwise variable torque is applied to a flywheel at time \(t=0\) causing its clockwise angular acceleration to decrease linearly with angular displacement \(\theta\) during 20 revolutions of the...
-
With neat block diagram, explain open-loop and closed-loop control systems.
-
Market-Tech, a market research firm, had the following transactions in June, its first month of operations. 1 \( \mathrm{~J}\). Witson invested \(\$ 28,000\) of personal funds in the firm in exchange...
-
At the beginning of 2021, Quentin and Kopps (Q&K) adopted the dollar-value LIFO (DVL) inventory method. On that date the value of its one inventory pool was $84,000. The company uses an internally...
-
Determine by direct integration the values of x for the two volumes obtained by passing a vertical cutting plane through the given shape of Fig. 5.21. The cutting plane is parallel to the base of the...
-
Describe an implementation of the positional list methods addLast and addBefore realized by using only methods in the set {isEmpty, first, last, before, after, addAfter, addFirst}.
-
The add method for a dynamic array, as described in Code Fragment 7.5, has the following inefficiency. In the case when a resize occurs, the resize operation takes time to copy all the elements from...
-
Suppose we are maintaining a collection C of elements such that, each time we add a new element to the collection, we copy the contents of C into a new array list of just the right size. What is the...
-
Marie Forleo, a marketing trainer and host of MarieTV, presents the eight tips for genuine networking. Do you agree or disagree with her suggestions? Discuss how this information is useful to you and...
-
Identify all relevant costs or revenue that are applicable to production- constrained decisions 1. Contributions margin of product 2. Interference with other production 3. Contribution margin per...
-
Gammaro Compary manufactures wallets from fabric. In 2 0 1 9 , Gammaro made 2 , 1 5 0 , 0 0 0 wallets using 1 , 2 5 0 , 0 0 0 yards of fabric. In 2 0 1 9 , Gammaro has capacity to make 2 , 8 0 0 , 0...

Study smarter with the SolutionInn App


