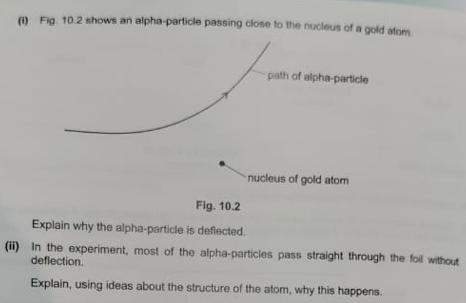
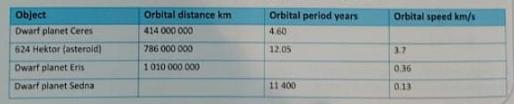
Cambridge Lower Secondary English Learners Book 8 2nd Edition Graham Elsdon - Solutions
Unlock a world of learning with our comprehensive solutions for the "Cambridge Lower Secondary English Learners Book 8, 2nd Edition" by Graham Elsdon. Access a wide array of online resources, including an answers key and solution manual, to enhance your understanding. Our solutions PDF offers detailed, step-by-step answers to solved problems, ensuring clarity and comprehension. Dive into chapter solutions and utilize the test bank for thorough preparation. This instructor manual is an invaluable companion to your textbook, available for free download. Empower your learning journey with our expertly crafted questions and answers, tailor-made for academic success.
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()