Question: Use Dijkstra's algorithm (Table 20.2) to find the shortest path tree and the forwarding table for node A in the Figure 20.35. Table 20.2 4.
Use Dijkstra's algorithm (Table 20.2) to find the shortest path tree and the forwarding table for node A in the Figure 20.35.
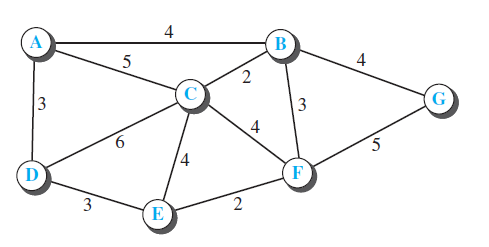
Table 20.2

4. 4. 3. 3.
Step by Step Solution
3.38 Rating (160 Votes )
There are 3 Steps involved in it
The following shows the shortestpath ... View full answer

Get step-by-step solutions from verified subject matter experts


