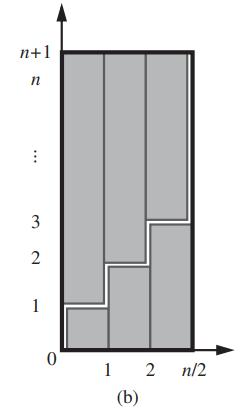
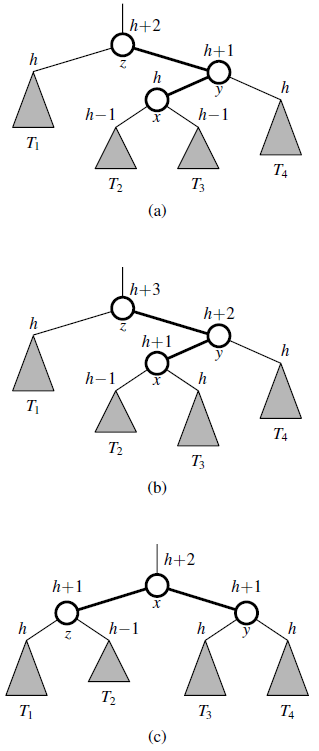
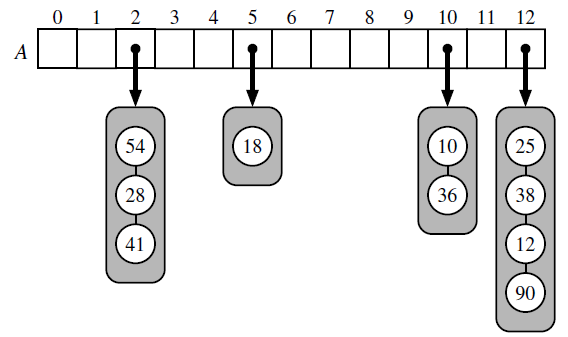
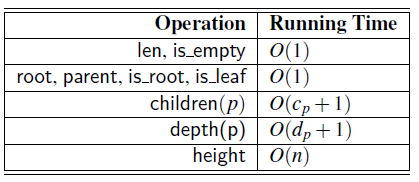
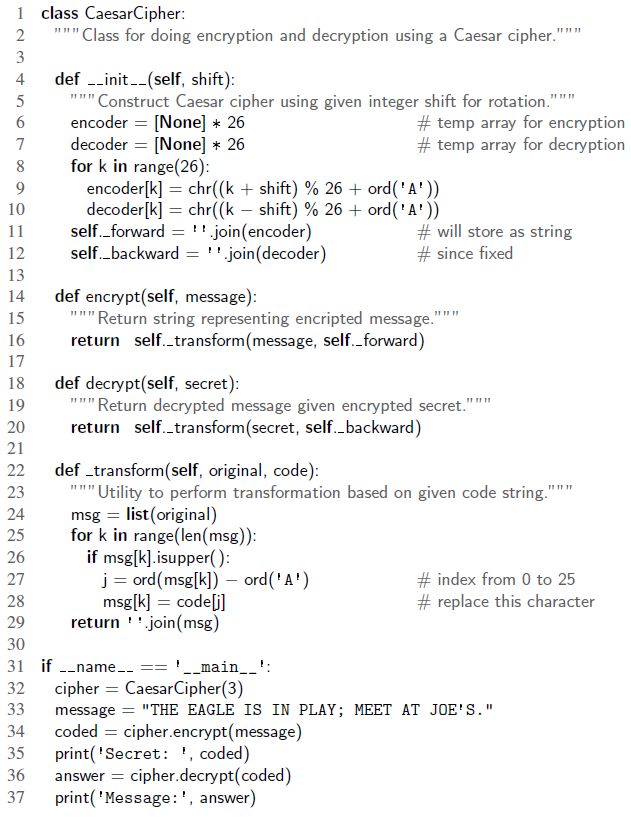
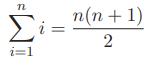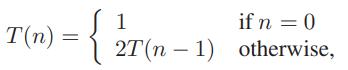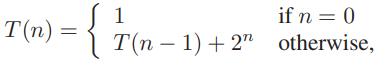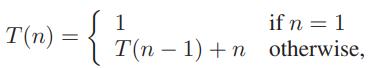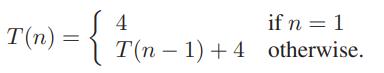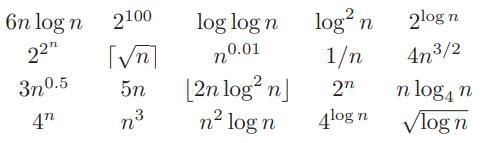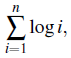Data Structures and Algorithms in Python 1st edition Michael T. Goodrich, Roberto Tamassia, Michael H. Goldwasser - Solutions
Unlock the comprehensive solutions to "Data Structures and Algorithms in Python 1st Edition" by Michael T. Goodrich, Roberto Tamassia, and Michael H. Goldwasser. Access an extensive online answers key and solution manual, featuring solutions in PDF format. Explore solved problems with detailed step-by-step answers, perfect for students and instructors alike. Our test bank and chapter solutions provide invaluable insights into textbook concepts. Enjoy the convenience of free downloads for the instructor manual, offering a seamless learning experience. Enhance your understanding with our questions and answers, tailored for academic success.
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()