Question: Draw a matrix similar to Table 1.4 that shows the relationship between security mechanisms and attacks. Table 1.4 Relationship Between Security Services and Mechanisms Service
Draw a matrix similar to Table 1.4 that shows the relationship between security mechanisms and attacks.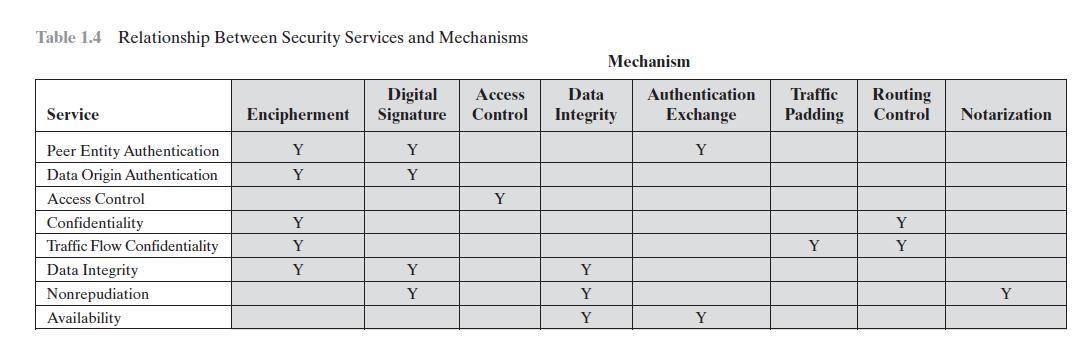
Table 1.4 Relationship Between Security Services and Mechanisms Service Peer Entity Authentication Data Origin Authentication Access Control Confidentiality Traffic Flow Confidentiality Data Integrity Nonrepudiation Availability Digital Encipherment Signature Y Y Y Y Y Y Y Y Y Access Data Control Integrity Y Mechanism Y Y Y Authentication Traffic Routing Exchange Padding Control Notarization Y Y Y Y Y
Step by Step Solution
3.40 Rating (159 Votes )
There are 3 Steps involved in it
Encipherment Digital signature Access control Data integ... View full answer

Get step-by-step solutions from verified subject matter experts


