Review the results of a recent Computer Crime Survey such as the CSI/FBI or AusCERT surveys.What changes
Question:
Review the results of a recent Computer Crime Survey such as the CSI/FBI or AusCERT surveys.What changes do they note in the types of crime reported? What differences are there between their results and those shown in Table 23.2?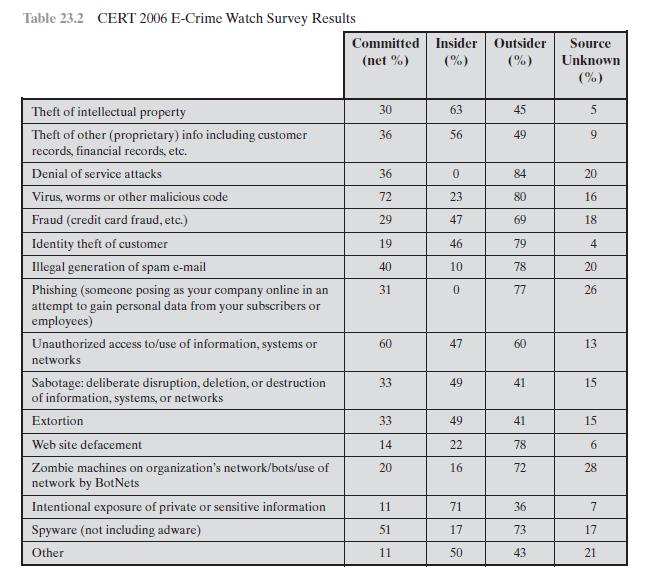
Transcribed Image Text:
Table 23.2 CERT 2006 E-Crime Watch Survey Results Theft of intellectual property Theft of other (proprietary) info including customer records, financial records, etc. Denial of service attacks Virus, worms or other malicious code Fraud (credit card fraud, etc.) Identity theft of customer Illegal generation of spam e-mail Phishing (someone posing as your company online in an attempt to gain personal data from your subscribers or employees) Unauthorized access to/use of information, systems or networks Sabotage: deliberate disruption, deletion, or destruction of information, systems, or networks Extortion Web site defacement Zombie machines on organization's network/bots/use of network by BotNets Intentional exposure of private or sensitive information Spyware (not including adware) Other Committed (net %) 30 36 36 72 29 19 40 31 60 33 33 14 20 11 51 11 Insider Outsider Source (%) (%) Unknown (%) 63 56 0 23 47 46 10 0 47 49 49 22 16 71 17 50 45 49 84 80 69 79 78 77 60 41 41 78 72 36 73. 43 5 9 20 16 18 4 20 26 13. 15 15 6 28 7 17 21
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 60% (5 reviews)
There is no simple answer to this problem as it depends on w...View the full answer

Answered By

Saranya Ganga
Initially I can't even think about me as a teacher. Beacause I was thinking that I can not become a good teacher and I can not make people understand deeply the subject. Bt when one of my senior teacher told me to try teaching in a famous tution centre in my home town I was not that much confident to teach. Bt after I have started the job I under stood the pleasure that a teacher is getting when students says that "We understood". Now in my ambition is to become a good teacher. The pleasure that we are getting from this job is most valuable in my opinion.
0.00
0 Reviews
10+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
Use the runs test to determine whether the sample is random. Let alpha be.05. 2 2 2 2 2 1 2 2 2 1 1 2 2 2
-
Evaluate the limit and justify each step by indicating the appropriate Limit Law(s). t* 2 lim --2 2t2 3t + 2
-
"I'm not sure we should lay out $300,000 for that automated welding machine," said Jim Alder, president of the Superior Equipment Company. "That's a lot of money, and it would cost us $84,000 for...
-
Suppose that General Motors Acceptance Corporation issued a bond with 10 years until maturity, a face value of $1000, and a coupon rate of 7% (annual payments). The yield to maturity on this bond...
-
Many coals from the western United States have a high moisture content. Consider the following sample of Wyoming coal, for which the ultimate analysis on an as-received basis is, by mass: Component...
-
If sales tend to fluctuate widely, then cash flows and the ability to service fixed charges will also vary. Such a firm is said to have high business risk. Consequently, there is a relatively large...
-
Why do we need evaluation measures for cluster algorithms?
-
The following defined pension data of Doreen Corp. apply to the year 2014. Defined benefit obligation, 1/1/14 (before amendment) .... $560,000 Plan assets, 1/1/14 ................... 546,200 Pension...
-
Using the information provided in the exhibits, calculate the breakeven numbers for Scissors in units and dollars (rounded to the next unit and nearest dollar, respectively), as well as the maximum...
-
An early controversial use of the DCMA was its use in a case in the United States brought by the Motion Picture Association of America (MPAA) in 2000 to attempt to suppress distribution of the DeCSS...
-
Repeat Problem 23.1 for Table 23.2. Table 23.2 CERT 2006 E-Crime Watch Survey Results Theft of intellectual property Theft of other (proprietary) info including customer records, financial records,...
-
Intermediate: Preparation of process accounts with all output fully complete. No Friction is an industrial lubricant, which is formed by subjecting certain crude chemicals to two successive...
-
Write a function that takes as input a non-negative integer in the range 0 to 99 and returns the English word(s) for the number as a string. Multiple words should be separated by a space. If the...
-
The Event Manager sighed as the festival approached and she had only five crafts vendors who had committed to taking part in the marketplace. She and her assistant were frantic. They had been...
-
the systematic recording, analysis, and interpretation of costs incurred by a business. Its significance extends beyond mere financial tracking; it plays a pivotal role in aiding management...
-
1.What is your process for ensuring that all your work is correct? 2.What do you mean by Batch Costing ? 3.Explain the accounting procedure for Batch Costing 4.State the applicability of Job Costing...
-
The increasing occurrence of freak weather incidents will have both local and global effects. Even in cases where production has been re-localized, freak weather can still greatly impact local...
-
Day 2, when 8 calls arrive in 1 h while only 3.5 were expected. Consider the data in Section 8.4, Exercises 23 and 24. Find the difference in support of the null and alternative hypotheses.
-
Keating & Partners is a law firm specializing in labour relations and employee-related work. It employs 25 professionals (5 partners and 20 managers) who work directly with its clients. The average...
-
List three design goals for a firewall.
-
List four techniques used by firewalls to control access and enforce a security policy.
-
What information is used by a typical packet-filtering router?
-
Indicate whether the following managerial policy increases the risk of a death spiral:Use of low operating leverage for productionGroup of answer choicesTrueFalse
-
It is typically inappropriate to include the costs of excess capacity in product prices; instead, it should be written off directly to an expense account.Group of answer choicesTrueFalse
-
Firms can avoid the death spiral by excluding excess capacity from their activity bases. Group of answer choicesTrueFalse

Study smarter with the SolutionInn App


