What are the differences among the firewalls of Figure 22.1? program V := {goto main; 1234567; subroutine
Question:
What are the differences among the firewalls of Figure 22.1?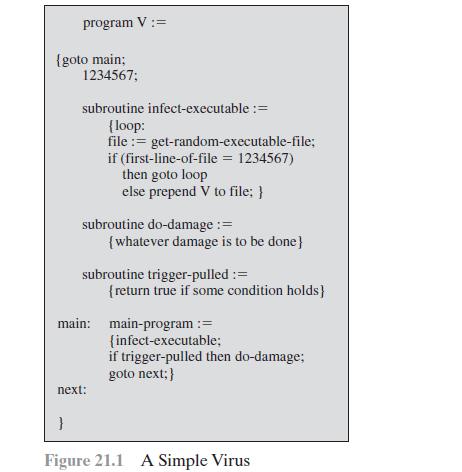
Transcribed Image Text:
program V := {goto main; 1234567; subroutine infect-executable := {loop: file := get-random-executable-file; if (first-line-of-file = 1234567) then goto loop else prepend V to file; } } subroutine do-damage := {whatever damage is to be done} subroutine trigger-pulled := next: main: main-program := {infect-executable; if trigger-pulled then do-damage; goto next; } {return true if some condition holds] Figure 21.1 A Simple Virus
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 50% (2 reviews)
Packet filtering firewall Applies a set of rules to each incoming and outgoing IP packet and then forwards or discards the packet Stateful inspection ...View the full answer

Answered By

Susan Juma
I'm available and reachable 24/7. I have high experience in helping students with their assignments, proposals, and dissertations. Most importantly, I'm a professional accountant and I can handle all kinds of accounting and finance problems.
4.40+
15+ Reviews
45+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
Cherokee Incorporated is a merchandiser that provided the following information: Amount Number of units sold 13,000 Selling price per unit $ 16 Variable selling expense per unit $ 2 Variable...
-
What are the differences among debentures, serial bonds, and callable bonds?
-
What are the differences among loading fees, exit fees, and 12b-1 fees?
-
Multiple Choice 1. Which of the following concepts are pervasive in the application of generally accepted auditing standards, particularly the standards of field work and reporting? a. Internal...
-
A piston/cylinder contains 10 lbm of butane gas at 900 R, 750 lbf/in 2. The butane expands in a reversible polytropic process with polytropic exponent, n 1.05, until the final...
-
In May 2001, unable to get credit from enough of its lenders, housewares retailer Lechters, Inc., filed for Chapter 11 bankruptcy. It then secured new bank financing in the amount of $86 million....
-
Develop a good classification model for predicting loan approval, based solely on cluster membership. Apply data-driven misclassification costs as shown in Chapter 16. Compare your results for the k...
-
Foy Company has a welding activity and wants to develop a flexible budget formula for the activity. The following resources are used by the activity: Four welding units, with a lease cost of $12,000...
-
P/L part of the SCI contains the following minimum compulsory lines: revenues . share of the after-tax profits and losses of equity method on disposal of assets/liabilities of discontinuing...
-
What are the common characteristics of a bastion host?
-
What is a circuit-level gateway?
-
Graham owns a building having a fair market value of $120,000. She takes out a fire insurance policy from the Bentley Insurance Company for $72,000; the policy contains an 80 percent co-insurance...
-
PART 1: DIGITAL TECHNOLOGY: Describe the key digital technology groups studied in this course and include a discussion of two examples for each group. PART 2: SOCIAL MEDIA: As studied in this course,...
-
Doing a strategic analysis of GraceKennedy Limited, What is the current level of its economic performance, an indication of the factors responsible for the current performance and recommendations for...
-
Dynamic capability is the ability for change and manage corporate learning. It allows an enterprise to adapt, develop and respond to future opportunities and discontinuous technologies. Innovation...
-
What potential solutions can organizations try to help support the adoption of a CDSS? In other words, what are some ways an organization can address the factors of implementation obstruction that...
-
Identify and briefly describe and discuss the three most important factors in building and maintaining trust among virtual global team members. Include in your discussion how you can leverage these...
-
Consider the following data on the behavior of 100 wild type and 125 mutant worms. Use the x2 test to check whether the control and treatment differ in the above contingency table. Crawl Normally...
-
Archangel Corporation prepared the following variance report. Instructions Fill in the appropriate amounts or letters for the question marks in the report. ARCHANGEL CORPORATION Variance...
-
a. Consider an L1 cache with an access time of 1 ns and a hit ratio of H = 0.95. Suppose that we can change the cache design (size of cache, cache organization) such that we increase H to 0.97, but...
-
Consider a single-level cache with an access time of 2.5 ns, a line size of 64 bytes, and a hit ratio of H = 0.95. Main memory uses a block transfer capability that has a first-word (4 bytes) access...
-
A computer has a cache, main memory, and a disk used for virtual memory. If a referenced word is in the cache, 20 ns are required to access it. If it is in main memory but not in the cache, 60 ns are...
-
Management makes many judgements and estimates in preparing accounts, some of which will have a significant effect on the reported results and financial position. Give examples of ZAIN estimates and...
-
What is the NPV of a project with an initial investment of $350,000 and annual cash inflows of $150,000 for the next 10 years? Cost of capital is 13% A $436,721.21 B $442,901.59 C $452,932.43 D...
-
Journal DATE DESCRIPTION POST. REF. DEBIT CREDIT 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 Joumalize the entries for the following transactions. Refer to the Chart of Accounts for exact wording of...

Study smarter with the SolutionInn App


