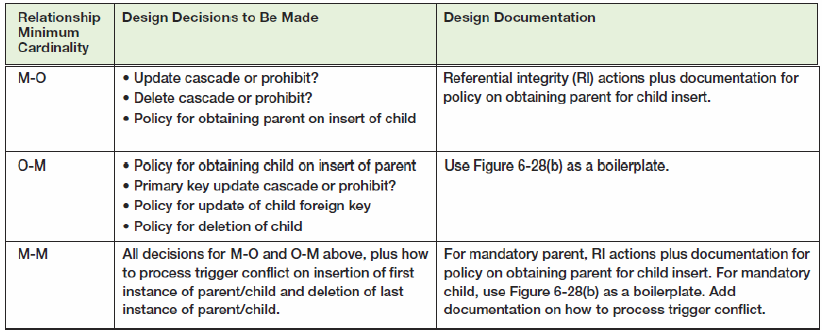
Explain the need for each of the design decisions in Figure 6-34. Design Decisions to Be Made
Question:
Transcribed Image Text:
Design Decisions to Be Made Design Documentation Relationship Minimum Cardinality • Update cascade or prohibit? • Delete cascade or prohibit? • Policy for obtaining paront on insort of child M-O Referential integrity (RI) actions plus documentation for policy on obtaining parent for child insert. • Policy for obtaining child on insert of parent • Primary key update cascade or prohibit? • Policy for update of child foreign key • Policy for deletion of child All decisions for M-O and O-M above, plus how For mandatory parent, RI actions plus documentation for to process trigger conflict on insertion of first instance of parent/child and deletion of last instanco of paront/child. Use Figure 6-28(b) as a boilerplate. O-M М-м policy on obtaining parent for child insert. For mandatory child, use Figure 6-28(b) as a boilerplate. Add documontation on how to procoss triggor conflict.
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 80% (10 reviews)
1 MO design decisions The MO design decisions are based on a mandatory parent If the primary key is ...View the full answer

Answered By

Amar Kumar Behera
I am an expert in science and technology. I provide dedicated guidance and help in understanding key concepts in various fields such as mechanical engineering, industrial engineering, electronics, computer science, physics and maths. I will help you clarify your doubts and explain ideas and concepts that are otherwise difficult to follow. I also provide proof reading services. I hold a number of degrees in engineering from top 10 universities of the US and Europe.
My experience spans 20 years in academia and industry. I have worked for top blue chip companies.
5.00+
1+ Reviews
10+ Question Solved
Related Book For 

Database Processing Fundamentals, Design, and Implementation
ISBN: 978-0133876703
14th edition
Authors: David M. Kroenke, David J. Auer
Question Posted:
Students also viewed these Computer science questions
-
Briefly answer the following questions: 1. Explain the intuition behind the two rules in the Bell-LaPadula model for mandatory access control. 2. Give an example of how covert channels can be used to...
-
Explain the need for each of the actions in Figure 6-29(b). Actions When Child Is Required Child Required Action on Parent Get a child. Prohibit. Update the foreign key of (at least one) child....
-
Explain the need for each of the actions in Figure 6-29(a). Parent Required Action on Parent Action on Child Insert None. Get a parent. Prohibit. Change children's foreign Modify key or foreign key...
-
Benny sells an apartment building. His adjusted basis for regular income tax purposes is $450,000, and it is $475,000 for AMT purposes. He receives $700,000 from the sale. a. Calculate Bennys gain...
-
Richardson Services Ltd. was formed on May 1, 2017. The following transactions took place during the first month. Transactions on May 1: 1. Shareholders invested 50,000 cash in exchange for ordinary...
-
A ball rolls horizontally with a speed of 7.6 m/s off the edge of a tall platform. If the ball lands 8.7 m from the point on the ground directly below the edge of the plat-form, what is the height of...
-
P2-5 Prepare an allocation schedule; compute income and the investment balance Pop Corporation paid $1,680,000 for a 30 percent interest in Son Corporations outstanding voting stock on January 1,...
-
The manager of a $20 million portfolio of domestic stocks with a beta of 1.10 would like to begin diversifying internationally. He would like to sell $5 million of domestic stock and purchase $5...
-
n October 2019, Brund Ltd, a manufacturer of wood home heaters, was taken to court by one of its competitors, Costa Air P/L on the ground that Brund had sought to enter into agreements with...
-
In this mini-case you will perform some procedures required as a part of audit planning. For ease your audit manager has already organized the workpapers and completed several of the required...
-
Explain the implications of each of the minimum cardinality specifications in Figure 6-40. Cardinality MAX MIN Relationship Parent Child Type Nonidentifying 1:N Nonidentifying 1:N Nonidentifying 1:N...
-
Explain why the enforcement of M-M relationships is particularly difficult.
-
A football team scores these numbers of goals in its matches. 1 3 2 4 4 2 2 5 2 3 Calculate the mean number of goals scored per match. The mean number of goals scored per match is: mean= mean = sum...
-
Q10: Region ( experienced compressive stresses and has a than the rest of the bracket. Region ( ) experienced tension stresses and has a of the bracket. Deep Drawing and Stretch Forming width (into...
-
A sample of 1500 computer chips revealed that 32% of the chips do not fail in the first 1000 hours of their use. The company\'s promotional literature claimed that above 29% do not fail in the first...
-
The 75 lb block is released from rest 5 ft above the plate. Determine the compression of each spring when the block momentarily comes to rest after striking the plate. Neglect the mass of the plate....
-
Indiana Soy Products (OSP) buys soybeans and processes them into other soy products. Each ton of soybeans that OSP purchases for $250 can be converted for an additional $180 into 675 lbs of soy meal...
-
The 2025 Annual Report of Splish International contains the following informatio (in millions) June 29, 2025 June 27, 2024 Total assets $1,545 $1,502 Total liabilities 989 1,060 Net sales 2,800 2.971...
-
Verify the divergence theorem for the function A = r 2 a r + r sin cos a over the surface of a quarter of a hemisphere defined by 0 < r < 3, 0 < < /2, 0, , /2.
-
Imagine you are the HR manager at a company, and a female employee came to you upset because she felt a male coworker was creating a hostile work environment by repeatedly asking her out on dates...
-
Compare and contrast byte-stuffing and bit-stuffing.
-
Assume we change the Stop-and-Wait Protocol to include a NAK (negative feedback), which is used only when a corrupted frame arrives and is discarded. Redraw Figure 11.9 to show this change. Figure...
-
In a byte-oriented protocol, should we first unstuff the extra bytes and then remove the flags or reverse the process?
-
Question 3 (24 marks) Wonderful Technology Company Limited sells computers and accessories. Data of the store's operations are as follow: Sales are budgeted at $400,000 for December 2019, $420,000...
-
Kratz Manufacturing Company uses an activity-based costing system. It has the following manufacturing activity areas, related cost drivers and cost allocation rates: Activity Cost Driver Cost...
-
You are a Partner with Fix-It Consultants and have been engaged in an advisory capacity with a software company, called MoveFast. The company is seeing a sharp decline in revenue, with the primary...

Study smarter with the SolutionInn App


