Question: Research the Koch Snowflake online then, using the techniques you learned in Section 18.9, implement an application that draws the Koch Snowflake. 18.9.1 Koch Curve
Research the Koch Snowflake online then, using the techniques you learned in Section 18.9, implement an application that draws the Koch Snowflake.
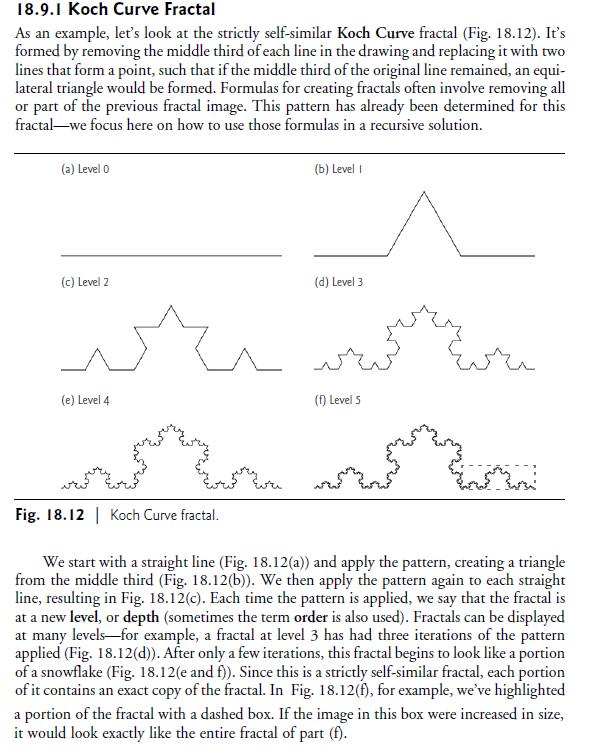
18.9.1 Koch Curve Fractal As an example, let's look at the strictly self-similar Koch Curve fractal (Fig. 18.12). It's formed by removing the middle third of each line in the drawing and replacing it with two lines that form a point, such that if the middle third of the original line remained, an equi- lateral triangle would be formed. Formulas for creating fractals often involve removing all or part of the previous fractal image. This pattern has already been determined for this fractal we focus here on how to use those formulas in a recursive solution. (a) Level 0 (c) Level 2 (e) Level 4 Fig. 18.12 | Koch Curve fractal. (b) Level I (d) Level 3 (f) Level S or w We start with a straight line (Fig. 18.12(a)) and apply the pattern, creating a triangle from the middle third (Fig. 18.12(b)). We then apply the pattern again to each straight line, resulting in Fig. 18.12(c). Each time the pattern is applied, we say that the fractal is at a new level, or depth (sometimes the term order is also used). Fractals can be displayed at many levels for example, a fractal at level 3 has had three iterations of the pattern applied (Fig. 18.12(d)). After only a few iterations, this fractal begins to look like a portion of a snowflake (Fig. 18.12(e and f)). Since this is a strictly self-similar fractal, each portion of it contains an exact copy of the fractal. In Fig. 18.12(f), for example, we've highlighted a portion of the fractal with a dashed box. If the image in this box were increased in size, it would look exactly like the entire fractal of part (f).
Step by Step Solution
3.47 Rating (150 Votes )
There are 3 Steps involved in it
The Koch Snowflake is a mathematical curve and one of the earliest fractal curves to have been described It is built by starting with an equilateral t... View full answer

Get step-by-step solutions from verified subject matter experts


