What is the output of this program if code corresponding to this pseudocode is run? Main Declare
Question:
What is the output of this program if code corresponding to this pseudocode is run?
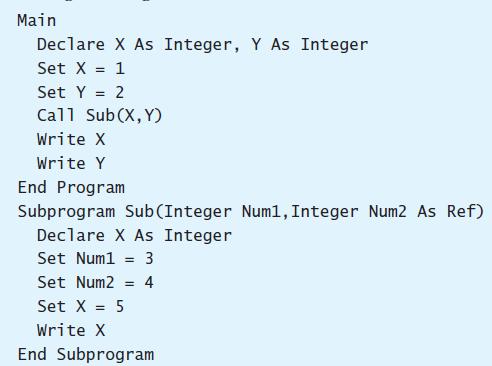
Transcribed Image Text:
Main Declare X As Integer, Y As Integer Set X = 1 Set Y = 2 Call Sub(X, Y) Write X Write Y End Program Subprogram Sub(Integer Numl, Integer Num2 As Ref) Declare X As Integer Set Numl = 3 %3! Set Num2 = 4 %3! Set X = 5 Write X End Subprogram
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 71% (7 reviews)

Answered By

Bhartendu Goyal
Professional, Experienced, and Expert tutor who will provide speedy and to-the-point solutions. I have been teaching students for 5 years now in different subjects and it's truly been one of the most rewarding experiences of my life. I have also done one-to-one tutoring with 100+ students and help them achieve great subject knowledge. I have expertise in computer subjects like C++, C, Java, and Python programming and other computer Science related fields. Many of my student's parents message me that your lessons improved their children's grades and this is the best only thing you want as a tea...
3.00+
2+ Reviews
10+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
If code corresponding to this pseudocode is run but X is initially set to 4, what is the output of this program? Main Declare X As Integer Set X = 1 Call Display(2*X,X,5) End Program Subprogram...
-
What is the output of this program if K = 1? Main Declare K As Integer Input K Set Result = F(K) Write Result End Program Function F(N) As Integer If N == 1 Then Set F = 1 Else Set F = N * F(N-1) Set...
-
What is the output of this program if K = 3? Main Declare K As Integer Input K Set Result = F(K) Write Result End Program Function F(N) As Integer If N == 1 Then Set F = 1 Else Set F = N * F(N-1) Set...
-
Define a passive portfolio construction strategy and briefly discuss how reasonable it might be for an investor to pursue a passive strategy. Explain the role of risk aversion in the construction of...
-
Explain topic, key number, and head note.
-
Alfred, owner of Hi-Tech Fiberglass Fabricators, Inc., is interested in using the reciprocal allocation method. The following data from operations were collected for analysis: Budgeted manufacturing...
-
What are the main elements of a marketing plan?
-
Explain the term business without boundaries. How is this changing the nature of organizations and who accomplishes various business processes?
-
P26-31A (book/static) Homers and the fiche town tomation Read the Cecoslow www the new Other Requirement Contact Art, and these Ceny XX) -X PA come 2. W When Congo 4. How to P26-31A (book/static)...
-
1. Discuss why financial statement users find environmental disclosures informative. 2. Obtain the G3 sustainability reporting guidelines of the Global Reporting Initiative (GRI,...
-
Suppose the subprogram header is changed to the following: Subprogram Sub(Integer Num1 As Ref,Integer Num2) If code corresponding to the new pseudocode is run, what is the output now? Main Declare X...
-
List the value and reference parameters in the subprogram Sub. Main Declare X As Integer, Y As Integer Set X = 1 Set Y = 2 Call Sub(X, Y) Write X Write Y End Program Subprogram Sub(Integer Numl,...
-
Suppose Saskatoon Honda had the following data for the years operations. The president of the dealership has long regarded the markup on material and labour for the parts and service activity as the...
-
A farmer has an acre of specialty vegetables and is preparing for the summer harvest. Historically, this acre has yielded an average of 2,100 lbs of product with a standard deviation of 950 lbs. A...
-
Solve 3x 82+22 = (4).
-
(c) Compute EVPI and EVSI (in thousands of dollars). (Round your answers to one decimal place.) EVPI $ 3.6 EVSI $ 3.6 Xthousand x thousand Discuss whether the firm should consider a consulting expert...
-
Question 9 (1 point) If the common law requires employees of a bar establishment to monitor a potentially intoxicated patron and to possibly make an effort to intervene if there is an indication the...
-
B. A velocity potential is given by the equation: Q = x-y 3. (10 pts) Short answer, What special characteristics of the velocity potential make it very useful in identifying a type of flow and...
-
Write a research paper on the three classic geometry problems of Greek antiquity.
-
Why is a help desk and production support critical to system implementations? Discuss its interrelationship with the problem management and reporting system.
-
Can the value of the header length field in an IPv4 packet be less than 5? When is it exactly 5?
-
In an IPv4 datagram, the value of total-length field is (00A0)16 and the value of the header-length (HLEN) is (5) 16 . How many bytes of payload are being carried by the datagram? What is the...
-
A host is sending 100 datagrams to another host. If the identification number of the first datagram is 1024, what is the identification number of the last?
-
Diplomatic Security Service provides Airport Transportation and Surveillance Service to Foreign Diplomats in Guyana. The company has two support departments - Information Systems and Equipment...
-
Q1: A disparity of bargaining power between the parties to a contract may result in unfair terms but a court is not likely to consider the contract unconscionable. Group of answer choices a. True b....
-
Life Tool Manufacturing has a system in place to recall products that prove to be dangerous at some time after manufacture and distribution. This represents which element of the due care theory?...

Study smarter with the SolutionInn App


