Question: 1. A 12-bit Hamming code whose hexadecimal value is 0xE4F arrives at a receiver. What was the original value in hexadecimal? Assume that not more
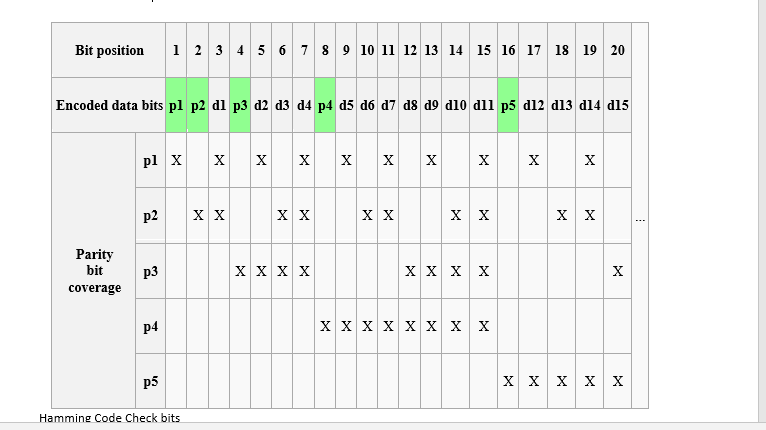
1. A 12-bit Hamming code whose hexadecimal value is 0xE4F arrives at a receiver. What was the original value in hexadecimal? Assume that not more than 1 bit is in error.
2. A bit stream 10011101 is transmitted using the standard CRC method described in the text. The generator polynomial is x3 + 1. Show the actual bit string transmitted. Suppose that the third bit from the left is inverted during transmission. Show that this error is detected at the receivers end. Give an example of bit errors in the bit string transmitted that will not be detected by the receiver.
3. The distance from earth to a distant planet is approximately 9 x 1010 m. What is the channel utilization if a stop-and-wait protocol is used for frame transmission on a 64 Mbps point-to-point link? Assume that the frame size is 32 KB and the speed of light is 3 x 108 m/s.
4. In the previous problem, suppose a sliding window protocol is used instead. For what send window size will the link utilization be 100%? You may ignore the protocol processing times at the sender and the receiver.
Bit position 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 9 10 1213 14 15 16 17 18 19 20 Encoded data bits pl p2 dl p3 d2 d3 d4 p4 d5 d6 d7 d8 do d10 dli p5 d12 d13 d14 d15 xix P2 XX Parity bit p3 coverage p4 Hamming Code Check bits
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


