Answered step by step
Verified Expert Solution
Question
1 Approved Answer
1. Below is a portion of a Wireshark capture of the beginning of the nmap scan. What technique does nmap use to identify open ports
1. Below is a portion of a Wireshark capture of the beginning of the nmap scan. What technique does nmap use to identify open ports on the host?
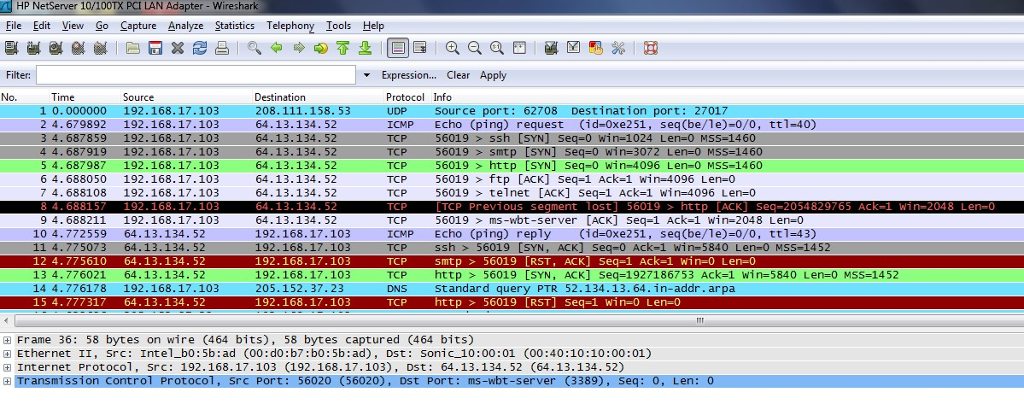
2. Nmap says it is using a syn stealth scan refer to the documentation available at http://insecure.orgmap/man/man-port-scanning-techniques.html
Why is this scan considered to be stealthy?
HP NetServer 10/100T X PCI LAN Ada Wiresha File Edit View Go Capture Analyze Statitics Telephony Iools Help @ke( | 1 [E] aaa %|@ Filter: Expression... Clear Apply Time Protocol UDP ICMP Info source port: 62708 Echo (ping) request No. Destination 208.111.158. 53 64.13. 134. 52 Source 168.17.103 Destination port: 27017 1 0.000000 192. 2 4.679892 192.168.17.103 (id-Oxe2 51, seq(be/1e)-0/0, 6019Ssh [SYN] Seq-0 win-1024 Len-0 MSS-1460 tt 1-40) 3 4.687859 192.168.17.103 64.13.134. 52 4 4. 687919 192.168.17.103 5 4.687987 192.168.17.103 6 4.688050 192.168.17.103 7 4.688108 192.168.17.103 84.688157 192.168.17.103 9 4.688211 192.168.17.103 64.13.134.52 64.13. 134. 52 64.13.134. 52 64.13. 134. 52 64.13.134.52 64.13.134. 52 192.168.17.103 TCP56019> smtp [SYN] seq-0 win-3072 Len-o MSS-1460 TCP 56019 > http [SYN] Seq-0 win-4096 Len-0 MSS-1460 TCP 56019 ftp [ACK] Seq-1 Ack-1 win-4096 Len-0 TCP 56019 > telnet [ACK] Seq=1 Ack=1 win=4096 Len=0 rcp TCP Previous segment lost] 56019 > http [ACK] seq-2054829765 Ack-1 win-2048 Len+0 TCP 56019ms-wbt-server [ACK] Seq-1 Ack-1 Win-2048 Len-0 ICMP Echo (ping) reply id-0xe251, seq(be/1e)-0/0, tt1-43) 10 4.772559 64.13.134. 52 11 4.775073 64.13.134.52192.168.17.103 12 4.775610 64.13.134. 52 13 4.776021 64.13.134.52 14 4.776178 192.168.17.103 15 4.777317 64.13.134. 52 192.168.17.103 192.168.17.103 205.152. 37.23 192.168.17.103 P ssh 56019 [SYN, ACK] Seq-0 Ack-1 win-5840 Len-0 MSS-1452 TCP TCP http 56019 [SYN, ACK] Seq 1927186753 Ack-1 Win-5840 Len-0 MSS-1452 DNS Standard query PTR 52.134 TCP http > 56019 [RST] Seq-1 Win-0 Len-0 smtp56019 [RST, ACK] Seq-1 Ack-1 Win-0 Len-0 .13.64. in-addr.arpa a Frame 36: 58 bytes on wire (464 bits), 58 bytes captured (464 bits) Ethernet 11, Src: Intel-b0: 5b : ad (00: do : b7 : bo : 5b: ad), Dst : Soni c-10 : 00: 01 (00:40: 10: 10 :00: 01) F] Internet Protocol, src: 192.168.17.103 (192.168.17.103), Dst: 4 . 13.134.52 (64.13.134.52) aTransmission control Protocol, Src
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


