Answered step by step
Verified Expert Solution
Question
1 Approved Answer
(1 point) Consider two discrete random variables X and Y, where X is drawn from the Bernoulli(1/2) distribution and Y is drawn from the
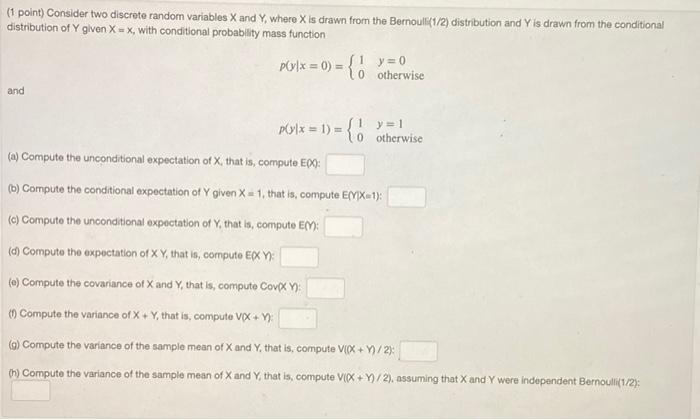

(1 point) Consider two discrete random variables X and Y, where X is drawn from the Bernoulli(1/2) distribution and Y is drawn from the conditional distribution of Y given X=x, with conditional probability mass function and P(ylx = 0) = ={1=0 10 otherwise Plylx=1)= = {0 otherwise y=1 (a) Compute the unconditional expectation of X, that is, compute EXX): (b) Compute the conditional expectation of Y given X=1, that is, compute E(Y)X=1): (c) Compute the unconditional expectation of Y, that is, compute E(Y): (d) Compute the expectation of X Y, that is, compute EXXY): (e) Compute the covariance of X and Y, that is, compute Cov(XY): (1) Compute the variance of X + Y, that is, compute VIX + Y): (g) Compute the variance of the sample mean of X and Y, that is, compute V(X + Y)/2): (h) Compute the variance of the sample mean of X and Y, that is, compute VIX + Y)/2), assuming that X and Y were independent Bernoulli(1/2): 3. (21 points) Definitely Integrals For the following, show sufficient work to communicate your process. (a) Compute / (3+5e) dr. (b) Compute S ( + 1 + 2) dr. 2 (c) Compute dx.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


