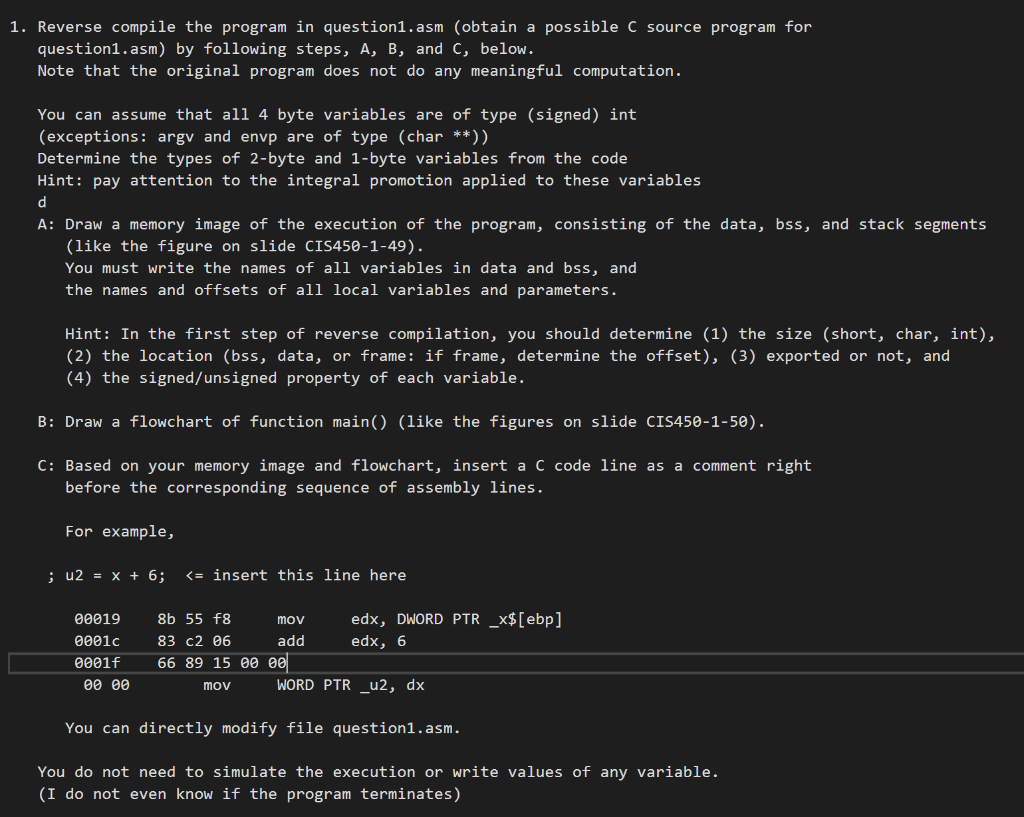
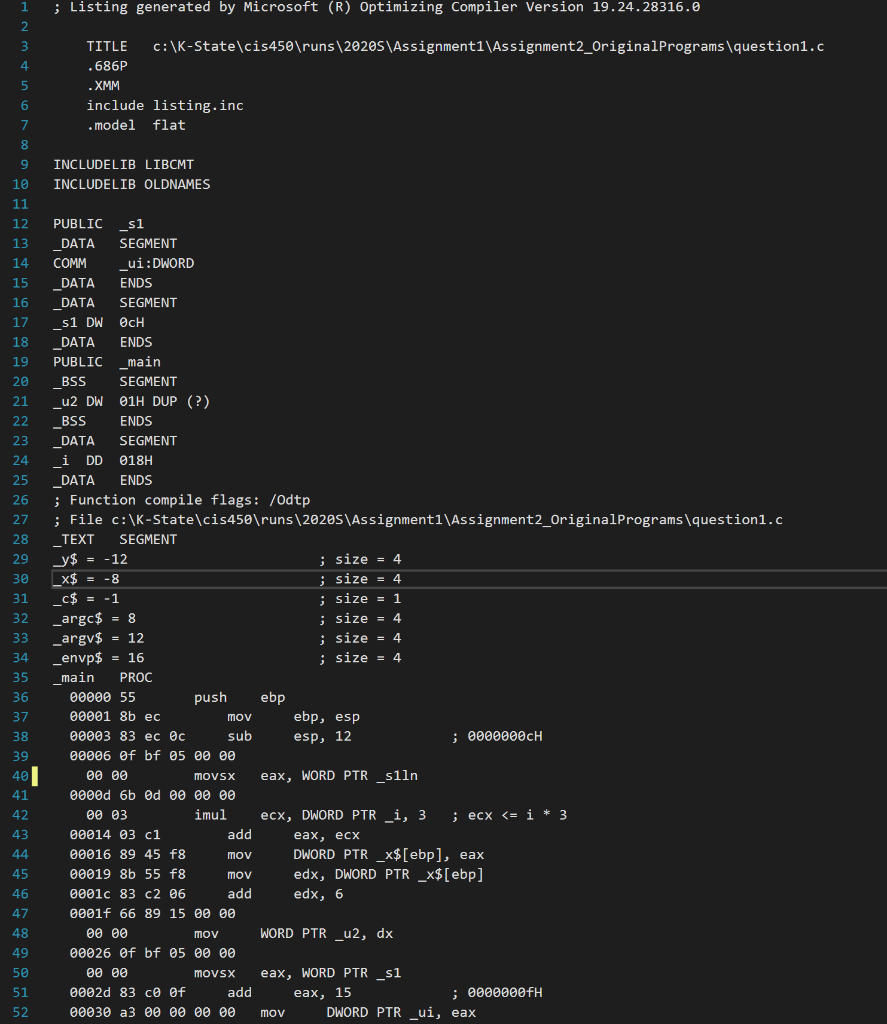
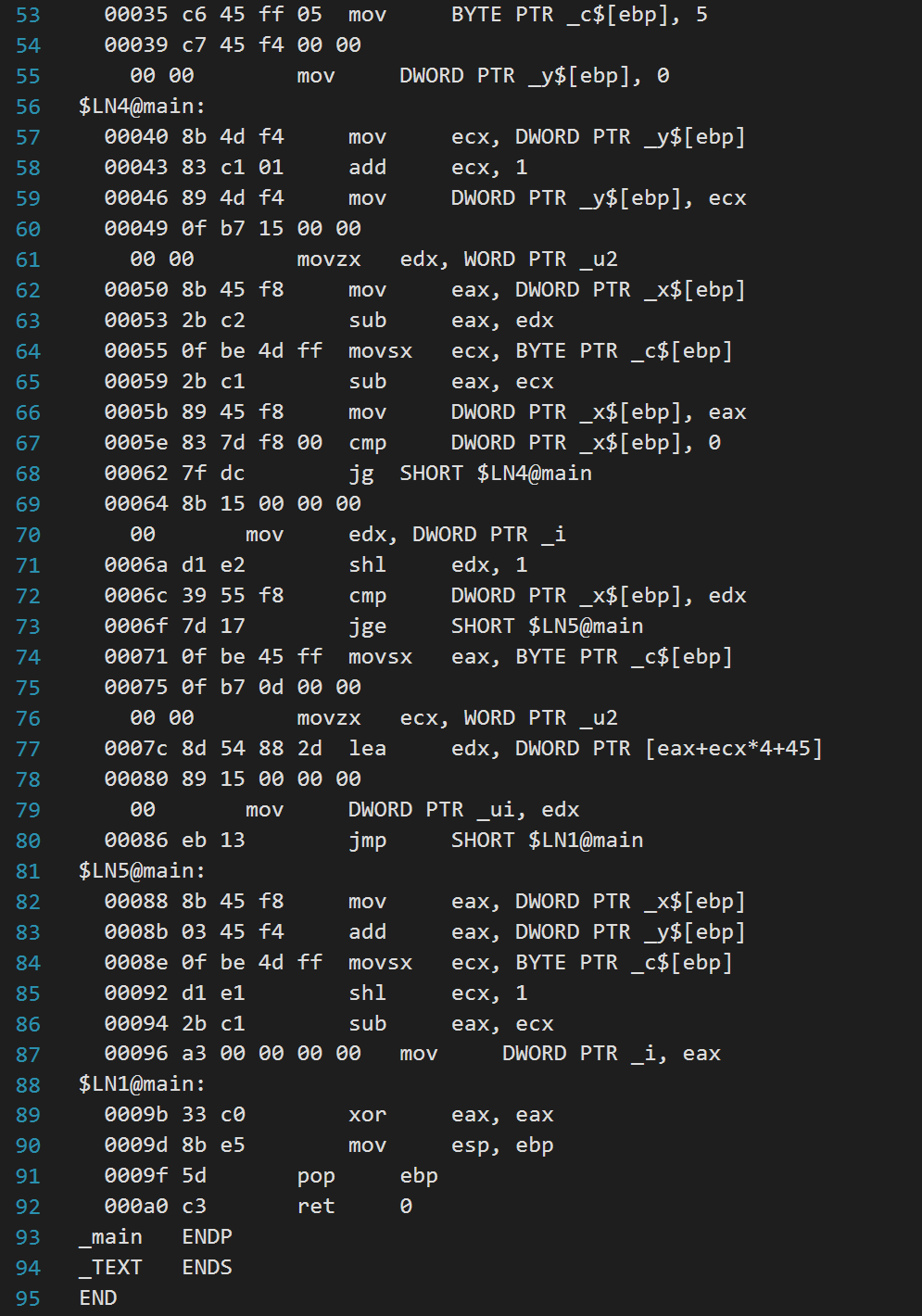
1. Reverse compile the program in question1.asm (obtain a possible C source program for question1.asm) by following steps, A, B, and C, below. Note that the original program does not do any meaningful computation. You can assume that all 4 byte variables are of type (signed) int (exceptions: argy and envp are of type (char **)) Determine the types of 2-byte and 1-byte variables from the code Hint: pay attention to the integral promotion applied to these variables A: Draw a memory image of the execution of the program, consisting of the data, bss, and stack segments (like the figure on slide CIS450-1-49). You must write the names of all variables in data and bss, and the names and offsets of all local variables and parameters. Hint: In the first step of reverse compilation, you should determine (1) the size (short, char, int), (2) the location (bss, data, or frame: if frame, determine the offset), (3) exported or not, and (4) the signed/unsigned property of each variable. B: Draw a flowchart of function main()_(like the figures on slide CIS450-1-50). C: Based on your memory image and flowchart, insert a C code line as a comment right, before the corresponding sequence of assembly lines. For example, ; u2 = x + 6; $[ebp] 00053 2bc2 eax, edx 00055 Of be 4d ff movsx ecx, BYTE PTR _c$[ebp] 00059 2b c1 sub eax, ecx 00056 89 45 f8 mov DWORD PTR__x$[ebp], eax 2005e 83 7d f8 00 cmp DWORD PTR_X$[ebp), o 00062_7f dc jg SHORT $LN4@main 100064 8b 15 00 00 001 eo mov e dx, DWORD PTR _i 0006a di e2 shl edx, 1 0006c 39 55 f8 cmp DWORD PTR__x$[ebp], edx 0006f 7d 17 SHORT $LN5@main 00071 Of be 45 ff movsx eax, BYTE PTR _c$[ebp] 00075 Of b7 od 00 00 00 00 movzx ecx, WORD PTR _u2 0007c 8d 54 88 2d lea edx, DWORD PTR [eax+ecx*4+45] 00080 89 15 00 00 00 oo m ov DWORD PTR _ui, edxi 00086 eb 13 jmp SHORT $LN1@main $LN5@main: 00088 8b 45 f8 mov eax, DWORD PTR X$ [ebp 00086 03 45 f4 add _ eax, DWORD PTR y$[ebp] 0008e Of be 4d ff movsx ecx, BYTE PTR _c$[ebp] 00092 d1 e1 shl ecx, 1 00094 2b c1 eax, ecx 00096 a3 00 00 00 00 mov DWORD PTR _i, eax $LN1@main: 2009b 33 co xor eax, eax 00090 8b e5 mov esp, ebp 0009f 5d pop ebp 0ae c3 ret _main ENDP TEXT ENDS END 80 81 82 83 84 85 sub 88 91 92 93 94 95 1. Reverse compile the program in question1.asm (obtain a possible C source program for question1.asm) by following steps, A, B, and C, below. Note that the original program does not do any meaningful computation. You can assume that all 4 byte variables are of type (signed) int (exceptions: argy and envp are of type (char **)) Determine the types of 2-byte and 1-byte variables from the code Hint: pay attention to the integral promotion applied to these variables A: Draw a memory image of the execution of the program, consisting of the data, bss, and stack segments (like the figure on slide CIS450-1-49). You must write the names of all variables in data and bss, and the names and offsets of all local variables and parameters. Hint: In the first step of reverse compilation, you should determine (1) the size (short, char, int), (2) the location (bss, data, or frame: if frame, determine the offset), (3) exported or not, and (4) the signed/unsigned property of each variable. B: Draw a flowchart of function main()_(like the figures on slide CIS450-1-50). C: Based on your memory image and flowchart, insert a C code line as a comment right, before the corresponding sequence of assembly lines. For example, ; u2 = x + 6; $[ebp] 00053 2bc2 eax, edx 00055 Of be 4d ff movsx ecx, BYTE PTR _c$[ebp] 00059 2b c1 sub eax, ecx 00056 89 45 f8 mov DWORD PTR__x$[ebp], eax 2005e 83 7d f8 00 cmp DWORD PTR_X$[ebp), o 00062_7f dc jg SHORT $LN4@main 100064 8b 15 00 00 001 eo mov e dx, DWORD PTR _i 0006a di e2 shl edx, 1 0006c 39 55 f8 cmp DWORD PTR__x$[ebp], edx 0006f 7d 17 SHORT $LN5@main 00071 Of be 45 ff movsx eax, BYTE PTR _c$[ebp] 00075 Of b7 od 00 00 00 00 movzx ecx, WORD PTR _u2 0007c 8d 54 88 2d lea edx, DWORD PTR [eax+ecx*4+45] 00080 89 15 00 00 00 oo m ov DWORD PTR _ui, edxi 00086 eb 13 jmp SHORT $LN1@main $LN5@main: 00088 8b 45 f8 mov eax, DWORD PTR X$ [ebp 00086 03 45 f4 add _ eax, DWORD PTR y$[ebp] 0008e Of be 4d ff movsx ecx, BYTE PTR _c$[ebp] 00092 d1 e1 shl ecx, 1 00094 2b c1 eax, ecx 00096 a3 00 00 00 00 mov DWORD PTR _i, eax $LN1@main: 2009b 33 co xor eax, eax 00090 8b e5 mov esp, ebp 0009f 5d pop ebp 0ae c3 ret _main ENDP TEXT ENDS END 80 81 82 83 84 85 sub 88 91 92 93 94 95









