Question
1. Tell two major differences between a VPN router and a VPN server (e.g., Cisco VPN concentrator). (8 points) Consider the remote access VPN scenario
1. Tell two major differences between a VPN router and a VPN server (e.g., Cisco VPN concentrator). (8 points)
Consider the remote access VPN scenario shown in the Figure. In this scenario, the remote users PC is in a hotel room in LA, while the Corporate Office is in NYC. We assume that a program X executed by employee Alice in the LA hotel wants to send message "80 cents per share" to a server program Y executed on the Application Server (see Figure) in the Corporate Office.
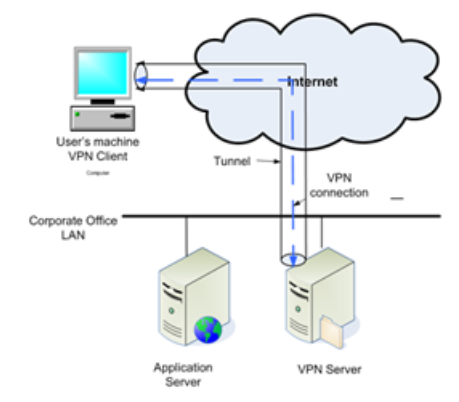
2. When the message leaves program X in the form of a packet, what is contained in the Destination IP field of the packets header?
3. When the message leaves program X in the form of a packet, what is contained in the Destination Port field of the packets header?
4. When the message leaves program X in the form of a packet, is the payload of the packet encrypted or not?
5. When the message leaves program X in the form of a packet, it will NOT instantly leave Alices PC. Instead, it will be forwarded to another program Z. What is program Z?
6. After program Z gets the packet, what will program Z do against the packet?
7. Before program Z sends out the revised packet, Z needs to let the VPN server (see Figure) authenticate Alice. For this purpose, program Z will send information W to the VPN server. What is info W?
8. After the VPN server receives info W, the VPN server will forward W to another server T. What is the name of server T?
9. After the VPN server receives a positive reply from server T, the VPN server will tell program Z that Alice is a legitimate employee. Then program Z will send out the message to the VPN server. When the message leaves program Z, what is contained in the Destination IP field of the packets header?
10. When the message leaves program Z, what is contained in the payload of the packet?
11. After a while, the message will arrive at the VPN server. When the message arrives at the VPN server, how will the packet be handled by the VPN server? Please give a step-by-step description.
12. After a while, the VPN server will want to forward the message to the Application Server (see Figure). Why does the VPN server not want to forward the message to server T?
13. When the message leaves the VPN server, what is contained in the Source IP field of the packet?
14. During the whole process, how many times has the message been encrypted?
15. During the whole process, how many times has the message been decrypted?
ternet User's machine VPN Client Tunnel VPN Corporate Office LAN HI Application Server VPN Server ternet User's machine VPN Client Tunnel VPN Corporate Office LAN HI Application Server VPN ServerStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


