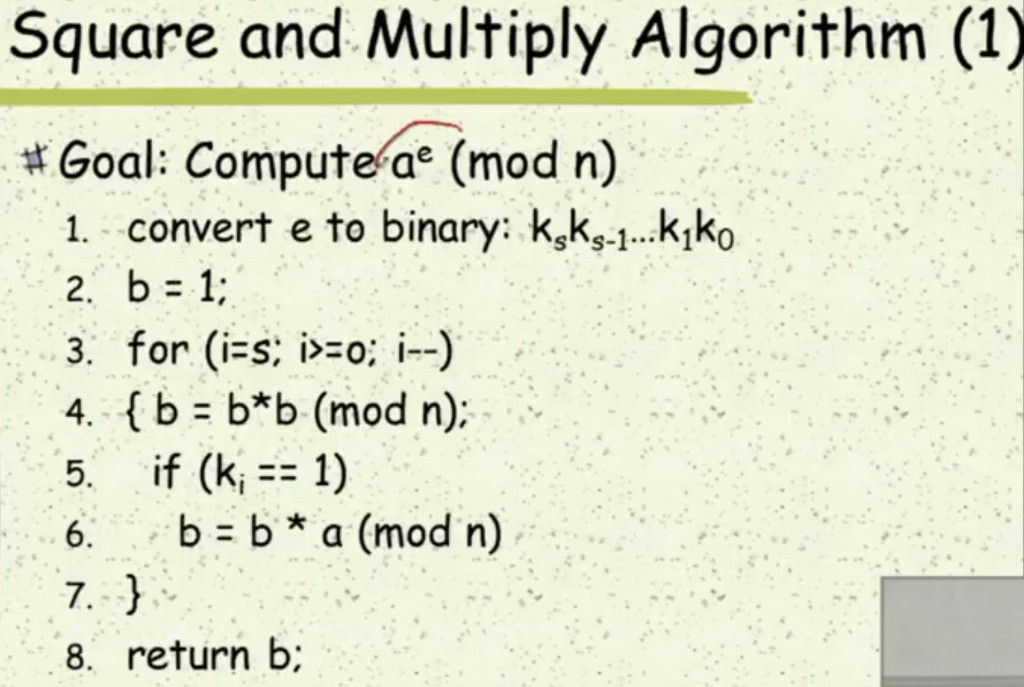
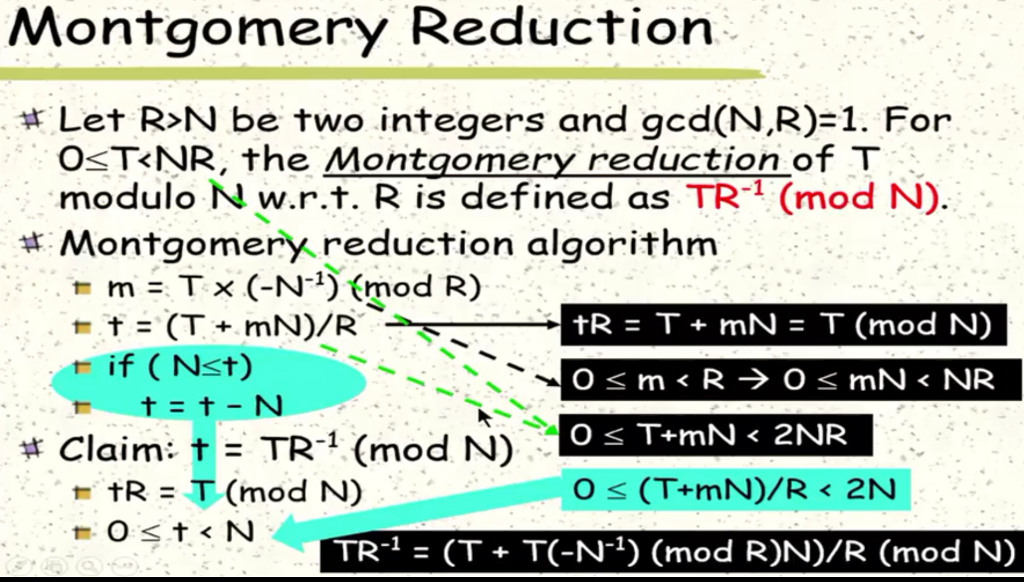
1. Which of the followings about physical attacks is incorrect? All physical attacks will make damage to the system All physical attacks will need the help from some tools and/or equipment Some physical attacks will not leave any tamper trace after attack Some physical attacks do not need physical access to the system point 2. Which of the following physical attacks is invasive? Software attacks Microprobing Fault generation Side channel attacks point 3 Which of the following non-invasive attacks is passive? Data remanence Fault injection Side channel attack Brute force 4 Which of the following about invasive attacks is true? With sensor mesh at the top metal layer, we still cannot catch all the invasive attacks. When the bus lines are scrambled, the attackers cannot find the bus lines to probe Because invasive attacks need to depackage the chip, all invasive attacks will be very expensive t is possible to probe into a single bus line and inject data to control bus activity. point 5 Which of the following statements is true for data remanence on SRAM? When SRAM is powered off, it will lose its stored data, so no information will leak It is possible to freeze data and read it at temperature higherhan-20 degree. When power up, SRAM's initial value will be random, so no data will leak. Data can be extracted from SRAM after multiple write/erase cycles. point 6. When we use the "iterative exponentiation and modular" method to compute 2 (mod 5) starting from 21, we will have 2 2(mod 5): 2 x 2-4(mod 5): 4 x 2 3(mod 5): 3 x 2 1(mod 5). The results we will see are 2, 4, 3, 1. If we use the same method to compute 37(mod 5), starting from 31, the results we will see are O 3,4,2,1,3,4,2 3, 9, 27, 81, 243, 729. 2187 o 3, 4, 1,2,0, 2, 1 1,2,3,4, 0, 1,2 7. Which of the following decimal to binary conversion is incorrect? 37-101011 207 11110011 25 11001 19-10011 point 8. For e-1001010110, when we compute a (mod n) with the left to right "square and multiple algorithm ()", the total number of multiplication (both b*b and b*a) we will do is Enter answer here point 9. In the slide of "Montgomery Reduction", which one of the following conditions is necessary? gcd (T,N)1 gcd (R,N)1 T>N N is a prime 10. The Montgomery reduction of 25 modulo 109 w.r.t. 128 is (just enter your answer, for example, 6) Enter answer here Square and Multiply Algorithm (1) # Goal: Compute ar (mod n) 1. convert e to binary: ksks 1..kiko 2. b 1; 3. for (i-s o ) 4. (b b*b (mod n); 5. if (ki 1) 8. return b; Montgomery Reduction Let R:N be two integers and gcd(N,R):1. For OsT












