Question: 1. Why was the attack on Maersk successful? 2. Identify and explain 5 different effects of how this cyberattack impacted transportation across the globe. Feel
1. Why was the attack on Maersk successful?
2. Identify and explain 5 different effects of how this cyberattack impacted transportation across the globe. Feel free to think broadly about implications that likely occurred due to this attack that wasn't directly addressed within the case.
a. Effect 1:
b. Effect 2:
c. Effect 3:
d. Effect 4:
e. Effect 5:
3. What should companies do to prevent cyberattacks?
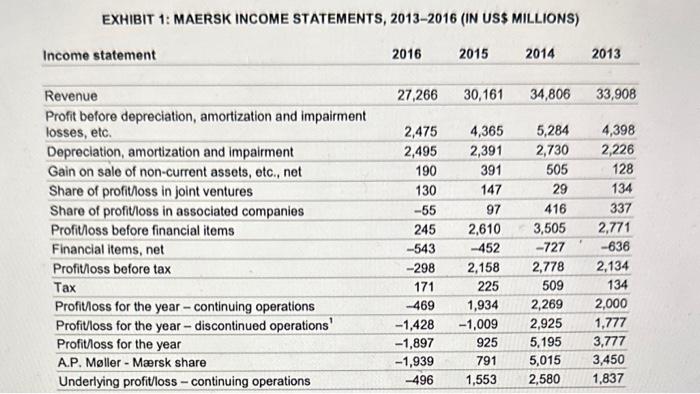
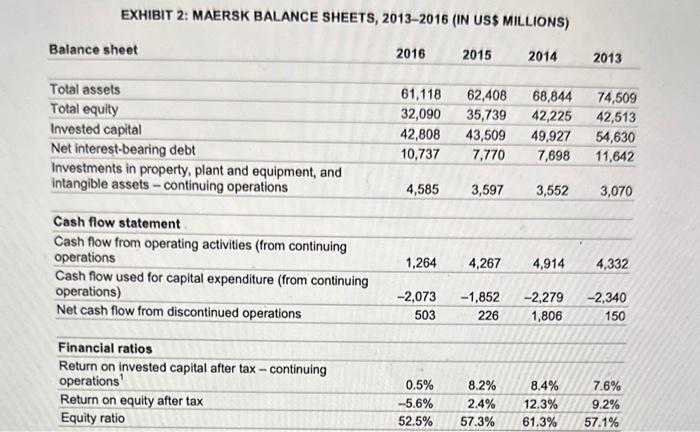
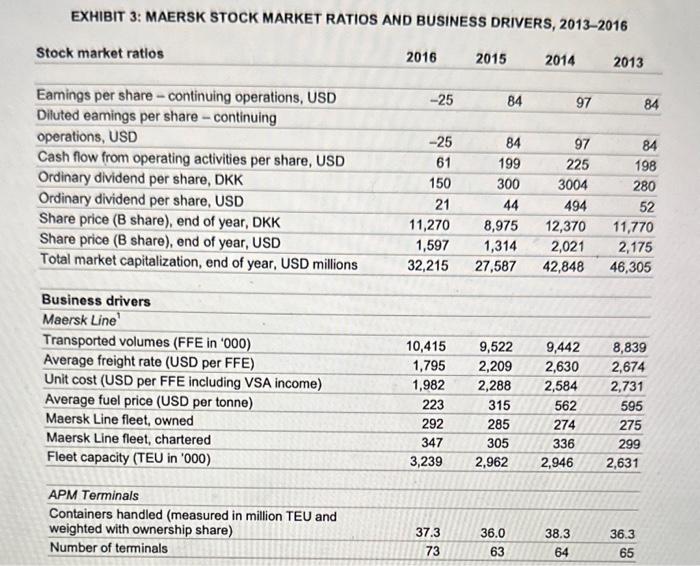
On June 26, 2017, Jim Hagemann Snabe had just arrived in California, where he was scheduled to speak the next morning on global risks and uncertainty at Stanford University's Directors' College. As he skimmed the participants' handout, he took note of the usual suspects: inflation, trade, energy price fluctuations, monetary policies, macroeconomic trends, and strained markets. Unbeknownst to Snabe, an event unfolding halfway across the globe was about to challenge those conventional notions of risk. That night, while fast asleep in his Palo Alto hotel room, Snabe was suddenly jolted from his slumber by an incoming call on his cellphone. The Maersk chairman glanced at the iPhone dock on his bedside, which read "4:00 a.m." in a dim blue digital font. Who could be calling at this hour, he wondered. 2 "We've suffered a major cyberattack!" exclaimed the caller. "The network is down for the entire company - every system, in every location around the globe." Not even the telephone lines were spared. Maersk, which accounted for 18 per cent of global container shipping, had gone dark. JIM HAGEMANN SNABE Jim Hagemann Snabe was born in the small Danish commune of Egedal, approximately 30 kilometres from the Swedish border but spent his early childhood in Nuuk, a remote outpost in Greenland where his father was a helicopter pilot. It was a lonely and isolated existence in a place where it took a week or longer to receive a message from the outside world. Returning to Denmark for his high-school education was not easy, but he found solace in the "cold logic" of computers, on which he programmed simple games." A self-described "nerd," Snabe attended Aarhus University in the late 1980s, where he studied mathematical proofs. However, his main love continued to be computers, and he secured part-time work in the business school's information technology department. "Mathematics is a lonely enterprise," explained Snabe. "My thesis was only read by three people, including my mother, and she did it out of courtesy." Upon receiving his master's degree in 1990, Snabe became a trainee at software giant SAP, Germany's second-largest company after Siemens. 5 In the mid-1990s, Snabe left SAP for IBM, but returned less than two years later after being offered a position as regional manager for SAP's Nordic region. "At that time, It thought I was smart and could solve problems on my own," he recalled. "But later I learned that putting the right team together with the best people is more important. .16 Over the next decade and a half, he continued to rise within SAP's ranks until 2010, when he was appointed chief executive officer (CEO). In May 2014, after leading a transformation that saw SAP's stock price more than double, Snabe resigned "to start a new professional life that allows me to spend more time with my family." Shortly after Snabe announced his retirement, Siemens invited him to join its supervisory board to improve the company's "technology and software competence." He was also clected vicc-chairman of Allianz, a German financial services firm that focused on insurance. Over the next couple of years, Snabe wrote a book on leadership, gave seminars at business and leadership conferences, and taught business courses as an adjunct professor at Copenhagen Business School. While promoting his new book, Snabe was asked how "leadership is changing in the digital world." He replied: Most companies try to avoid changes until they are in trouble. Many talk about a need for a "burning platform" to change everything. I believe that in the digital world, the ability to reinvent yourself comes from the ability to create a burning desire, not a burning platform." Finally, in January 2017; Siemens elected Snabe to be supervisory board chairman, promising to further accelerate the company's digital transformation. 10 As if taking the helm of Germany's largest conglomerate was not enough, a few months later Snabe also agreed to serve as chairman of A.P. MollerMacrsk, the world's largest shipping company. It was a move that prompted the Financial Times to declare him "Europe's top industrialist." "11 Shepherding Maersk through "the biggest transformation in its history" would not be easy after the company reported the largest loss of any Danish enterprise. Still, if Maersk could modernize, many believed that Snabe was the one to do so. Not only was he younger, at 51, than the chairmen who had preceded him, he also had "an exceptional gift for finding a clear path through a forest of opportunities, thretits, and complexity. 112 A. P. MLLER-MAERSK 13 A. P. Meller-Maersk, commonly known as the Maersk Line, was founded in 1904, when A. P. Moller and his father purchased a used steamship operating out of the Danish port of Svendborg. Ten years later, the company added more steamships to meet the demands of the "Great War" that had engulfed Europe. Shortly after the war, Maersk built its own shipyard and established an overseas office in New York City, where it operated a shipping route from the United States to Asia. Although during the Second World War, most of the company's ships were requisitioned by various Axis and Allied countries, and many were sunk during the war, Maersk was able to resume operations after the war along its original routes and added new routes to the Middle East and Africa. By the time of A. P. Moller's death in 1965, the company operated nearly half of Denmark's entire merchant fleet. In the 1970s, the company began operating container vessels, which became the defining symbol of the company's global shipping operations. The size of those ships continued to grow over the years, from fewer than 3,000 TEUs to more than 20,000 TEUs in 2018. 14 Macrsk also began manufacturing its own containers and developing internal logistics capabilities. In 2005, it acquired Damoo, a leading provider of supply-chain management and merged it with Maersk Logistics under the By 2017, Maersk operated out of 343 ports worldwide and managed approximately 18 per cent of the world's container shipping. That meant that "every 15 minutes on average a container ship will come to a port somewhere with between 10 [thousand] and 20 thousand containers," explained Snabe." "For each container shipped, there may be up to 30 different parties involved, communicating up to 200 times.,"16 Although the placement and management of orders was typically electronic, most of the "underlying processes" had not changed in decades. Much of it was managed on paper and there was no consistency between countries. Snabe's focus would be to modernize the supply chain partly by digitizing those underiying processes. We want to transform the industry by reducing the complexity. .... The opportunities from digitisation are significant. It has the potential to both simplify the customer experience and improve the productivity of assets, primarily ships and ports, effectively reducing costs across the value chain. It is my sincere belief that this company is best positioned to front the digitisation of the shipping industry.... 17 In 2016, Maersk lost nearly $2 billion 11 on $27 billion in revenue (see Exhibits 1-3). The losses were largely blamed on shipping industry overcapacity, leading to a nearly 20-per-cent drop in freight prices., 19 It was the second annual loss since the devastation of the Second World War. However, by early 2017, demand had increased to the point that it outstripped supply, prompting CEO Seren Skou to predict "reasonable ... supply-and-demand fundamentals" that would lead to an estimated $1 billion in profit by the end of 2017.20He added that, because the "price war" was over, "things are looking a lot better now than they did a year ago. We are starting [2017] from a strong position." At At the same time, Skou warned that a trade war between the United States and China could result in a 25-per-eent drop in Chinese exports, negatively impacting Macrsk. WAR IN UKRAINE For much of its history, Ukraine has been a battleground between east and west. At various points in the 20th century, it was occupied by Poland and Germany to the west and Russia to the east. In many of these conflicts, Ukrainians aligned with various occupation forces. During the Second World War, for instance, some Ukrainian nationalists supported Germany's invasion of the Soviet Union, which had annexed Ukraine in 1921. By the end of the war, 28,000 towns and villages had been razed, and as many as eight million Ukrainians -roughly 20 per cent of the country's population - had lost their lives. 22 The defeat of Germany by the Red Army left Ukraine entirely in Soviet hands. For the next four decades, Ukrajae led the Soviet Union in economic growth and output, even surpassing Western European courtries in the output of some key commodities. 23 It also became an important location for technology, hosting various Soviet weapons, aerospace, and energy centres. The fall of the Iron Curtain led to Ukrainian independence in 1991. However, unlike other former Soviet republics that experienced rapid economic growth in the 1990 s, Ukraine was plagued by hyperinflation and a severe recession that saw its gross domestic product fall by 60 per cent. At the same time, state failures pushed many Ukrainians toward the black market, and despite its independence, Ukraine continued to rely heavily on Russia, with which it conducted nearly 40 per cent of its trade. 24 Tensions over the role of Russia in Ukraine's economic and political affairs came to a head in 2013, when anti-government forces mobilized against pro-Russian president, Victor Yanukovych. Many Ukrainians wanted their country to strengthen ties with the West and perhaps eventually become part of the European Union, while Yanukovych sought to strengthen Ukraine's ties with Russia, which, for its part, saw the encroachment of the European Union and NATO (the North Atlantic Treaty Organization) as a threat to its security. In 2014, Russia annexed Crimea following an uprising by pro-Russian militias against Kiev. 25 Inspired by the events in the Crimea, other parts of eastern Ukraine attempted to secede, with pro-Russian separatists recciving material support from Moscow. Despite Russian efforts to destabilize the country, integration with the West continued, including a 2016 free-trade agreement with the European Union and a 2017 visa-free travel agreement. Ultimately, the Ukrainian government saw these agreements as steps toward European Union membership. 26 CYBERWAR We anticipate that cyberwar may be to the 21 st century what blitzkrieg was to the 20 th century. John Arquilla and David Ronfeld 27 The rise of fake news, attacks on the media, and interference in both the Brexit vote and the 2016 American election appeared to catch many off guard. Yet, in their seminal 1993 U.S. Department of Defense analysis on cyberwarfare, John Arquilla and David Ronfeld predicted that "widespread multiorganizational networks that have no particular national identity" would attempt to undermine civil society. "A netwar may focus on public or elite opinion, or both," they explained. It may involve public diplomacy measures, propaganda and psychological campaigns, political and cultural subversion, deception of or interference with local media, infiltration of computer networks and databases, and efforts to promote dissident or opposition movements across computer networks. 28 Despite these warnings, 25 years later, democratic nations around the world appeared ill-equipped to handle the deluge of cyberattacks directed at large and small organizations, nations, and individuals. Following the overthrow of Victor Yanukovych in 2014, Russia began sponsoring cyberattacks against key components of the Ukrainian economy and infrastructure, beginning with distributed denial of service (DDoS) attacks against pro-Western websites. A DDoS attack involved using compromised computers and devices to send massive amounts of garbage data over the Internet to targeted websites. In some situations, these attacks resulted in service slowdowns, but often they could knock a site off the Internet for days at a time. Meanwhile, Russia engaged in a social-media campaign, blocking pro-Westem accounts and disseminating Russian propaganda. 29 Phishing - whereby attackers sent emails with links and attachments that, when opened delivered a payload of malicious software (i.e., malware) - was frequently deployed against Ukrainian networks. The malware might manifest itself immediately, but often it worked to stealthily provide access to hackers who would steal information or attack assets at a later time. On December 23, 2015, compromised accounts delivered malware to the Ukrainian power grid, causing a widespread power blackout. The malware simultaneously erased computer drives to delay restoration, and a coordinated DDoS attack disabled the power company's phone lines. 30 Ransomware was a particularly destructive malware that encrypted victims' data so that it could not be read without a decryption key. Ransomware screens often displayed a payment page that required the victim to pay a fee in bitcoin or other cryptocurrency to receive the decryption key. To mitigato such attacks, network administrators were admonished to back up data on a regular basis, because even when ransoms were paid, the decryption keys did not always work. The best mitigation involved completely erasing the computer drive and restoring the system from an uninfected backup. NOTPETYA RANSOMWARE NotPetya was a particularly virulent strain of ransomware that targeted a Ukrainian financial program known as MeDoc. In the weeks leading up to the attack, MeDoc employees opened phishing emails that contained malware attachments or linked to malware servers. The attackers then used leaked U.S. National Security Agency exploits, such as EternalBlue and EternalRomance, which the U.S. government had developed for Internet surveillance. EternalBlue gave attackers remote access to infected systems through vulnerable Microsoft Windows' file and printer sharing protocols, while EternalRomance escalated privileges to control and modify systems without detection. Although Microsoft issued an emergency patch for the vulnerability in March 2017, many organizations had yet to update their systems. 32 Once computers were infected, attackers could install other software, monitor communications, and steal data and passwords. 33 With those passwords in hand, infecting patched systems became trivial, allowing the attackers to hide the NotPetya ransomware in a software update that was pushed out to MeDoc customers on June 22, 2017. In fact, a few weeks before NotPetya's devastating attack, Microsoft announced that it had "uncovered a well-planned, finely orchestrated cyberattack that targeted several high-profile technology and financial organizations." Microsoft cybersecurity researcher Elia Floria explained: An unknown attacker was taking advantage of a silent yet effective attack vector: the compromised update mechanism or software supply chain for a third-party editing tool. The software veldor that develops the editing tool was unaware of the issue. In fact, while their software supply chain served as a channel for attacking other organizations, they themselves were also under attack. 34 Floria further noted that the effectiveness of supply chain cyberattacks depended on "the common trust relationship" that exists between customers and suppliers. NotPetya was also not a true ransomware program, but one that mimicked ransomware by offering to restore infected computers after victims paid a ransom of $300 (see Exhibit 4). However, the attackers provided no means for victims to pay the ransom or receive decryption keys. Instead, NotPetya sought to permanently destroy and disable infected systems and networks. The sophistication of the tools employed and the fact that no ransom could be paid to recover infected systems suggested that NotPetya was not the work of cybercriminals intent on extorting companies for financial gain, but a state-sponsored group, most likely aligned with Russia. Moreover, NotPetya remained dormant for five days until the eve of Ukrainian Constitution Day, a celebration of independence from Russia and one of the republic's most important holidays. 13 When this ticking time bomb finally exploded on the morning of June 27 , it spread through infected networks at an unprecedented speed. A major Ukrainian bank saw its entire network destroyed in 45 seconds. It started with an unscheduled reboot of computers, followed by encoding of the master boot record that controlled how programs were loaded onto computers. A warning then appeared on the screen that the file system was being "repaired." "DO NOT TURN OFF YOUR PC"" it read. In fact, the only way to save the data from permanent destruction was to shut off power before the files could be encrypted. If one followed the attacker's instructions, the computer would reboot a second time and display fake ransomware payment "instructions." By this time, company files had been lost forever." More than 300 Ukrainian companies, banks, and hospitals were compromised, representing roughly 10 per cent of the country's computers." Although NotPetya had targeted Ukraine specifically, multinational corporations doing business in the region often used MeDoc for local tax filing. Once computers had been compromised, the malware also spread throughout their global networks. One of those firms was A. P. Maller-Maersk. MAERSK'S MESS Hardware is easy to protect: lock it in a room, chain it to a desk, or buy a spare. Information poses more of a problem. It can exist in more than one place; be transported halfway across the planet in seconds; and be stolen without your knowledge. Bruce Schneier, chief technology officer of IBM Resilient" 3! On June 27, Pawel Szczecki, CEO of Predica, a Polish analytics company that provided support to Maersk, was meeting with his Maersk counterparts in London, England, where the company's information technology (IT) support was headquartered. He recalled: It was ... a nice summer day. The morning started out like any other. The planned meeting began and discussions about the new Managed Service operations had just commenced, when a large commotion spread across the office. Suddenly, the monitoring sereens started to show all systems turning to reogand not long after all laptops started to reboot. Similar events were happening across the company's global network. As a systems engineer in Copenhagen prepared to deliver an update for the company's 80,000 personal computers (PCs), his computer spontaneously rebooted. When he rose from his desk, he noticed "a wave of screens turning black" as all the PCs began simultaneously rebooting. 4 Back in London, systems administrators took nearly 30 minutes to realize what was happening before they began shouting to everyone to unplug their machines. The entire nctwork took more than two bours to shut down, primarily because email, messaging, and phone systems were also down as employees resorted to WhatsApp and personal phones to communicate. By then the damage had been done. Maersk's senior system administrators had warned the company that its network was vulnerable to attack. In 2016, they had complained that the company's ancient Windows 2000 server software was overdue for a complete overhaul. Additionally, because Microsoft had long discontinued support for Windows 2000 and Windows XP, both of which were still used on many of the company's PC terminals, any PCs running those outdated operating systems did not receive security patches. The senior system administrators had wamed that, unless something was done, the entire infrastructure could flee a administrators - whose bonuses depended on current infrastructure uptime, not installing upgrades - had never implemented them. " Good computer hygiene involved not only keeping software up to date but also providing regular backups. In this area, Maersk followed best practice, making backups of its data every few days and keeping those backups off-line at various locations across its global network. However, a central piece was missing, the domain controllers that mapped the company's network and allowed access to authorized users. A domain controller was a Microsoft Windows server that authenticated users and provided access to computer resources. It was essentially the central nervous system of the computer network, consisting of an "active directory" of multiple master controllers. Maersk operated a network of 150 domain controllers, each of which could act as a backup for the entire network. If one failed, it could easily be restored from any one of the other 149 controllers. What the company hadn't accounted for was all 150 nodes being hit by the same malware simultaneously, wiping out the entire network in one foray. It meant that the company's entire network structure would be lost-forever-unless a controller somewhere in the company had been off-line during the attack. "The primary and key objective was to reestablish the Active Directory for identity management," recalled Szczecki. "This was necessary to reenable resource access which was the first step towards switching back to automated operations."42 Normally, conducting a search of company resources would have simply involved emails or phone calls to key IT staff at each of the company's 150 domain controller sites. However, with the email and phone lines knocked out by the same cyberattack, the emergency-response centre had resorted to communicating through personal emails and phone numbers, not all of which were readily accessible without the HR (human resources) personnel database. Maersk brought in consultants from Deloitte to manage the recovery effort, along with smaller IT firms such as Predica. The company booked all the hotels in the area to house the recovery team, but many were working such long hours that they chose to sleep in the office. 43 As status updates rolled in from the various sites, the team became increasingly disillusioned. Everyone had beten hit. It began to appear that the network directory was lost forever, when word arrived that one site may have survived-in Ghana. The West African country was in the midst of a longstanding energy crisis that had led to the demise of numerous businesses. The nation was often plunged into total darkness for up to 24 hours at a time, and generator prices in the country soared. The unreliable power situation also had cconomic consequence, and "Morgan Stanley ... cut its 2015 growth forecast for Ghana from 5 per cent to 3 per cent due to the power cuts." 4 For most Ghanaians, the power outage on June 27 was yet another reason to curse the government. For Maersk however, it seemed like divine intervention, as "joyous whoops" filled the London command centre, "The ecstasy was short-lived, however, because the company needed to find a way to recover the data. The domain controller could not be connected to the Internet, as Ghana's network bandwidth was so slow it would have taken days to transmit. Moreover, connecting it to the internet risked infecting the last known controller and the company's last hope of restoring its network. Instead, the company instructed its administrator in Ghana to deliver the hard drive to London for examination. But there was one problem. No one in the Ghana office had a travel visa for the United Kingdom and Burope, and it would take weeks to get one. Instead, an employee from Ghana would need to travel to Nigeria and band the hard drive to an employee in that country, who would then transport the hard drive to London. For a time, it became the most valuable hard drive in the world. MANAGING A GLOBAL SHIPPING COMPANY WITH PEN AND PAPER As the London Emergency Response Centre worked furiously to restore Macrsk's IT infrastructure, shipping terminals around the world were becoming hopelessly backlogged. Macrik operated the largest terminal in the Port of Los Angeles, commonly known as America's port because of its importance to U.S. trade. Not only was the Port of Los Angeles the largest container port in the United States, but, as a part of the San Pedro Bay Port Complex, and together with the neighbouring Port of Long Beach, it supported one in nine jobs in the five-county Southern California region. is As Maersk shut down its global computer network, it was left with no choice but to close the terminal. 4 ? A similar story was unfolding at Maersk's terminal in Port Elizabeth, New Jersey, the largest port on the cast coast. Three thousand trucks arrived daily at the port to load and unload hulking containers loaded with furniture, electronics, bananas, and almost every other imaginable product. On the moming of June 27 , more than 800 trucks lined the road for more than a mile to the port, unable to move. Some sat for as long as six hours before police told them to turn around and leave the area. "One trucker explained how he received an incomprehensible email about the attack from a Gmail account. It offered no explanation and no information about when the port would reopen. His only recourse was to find somewhere to store his cargo and await word. 49 Normally, 90 per cent of Maersk's shipping orders were placed through the company's online system. The company had no choice but to manage shipments manually. Many companies with tight supply chains could not wait for orders to be processed manually. Instead, they sought out alternative shippers, in many cases resorting to costly air freight. Maersk offered to compensate customers for the added expenses, which amounted to millions of dollars per customer. Overall, Maersk saw its shipping volume decline by 20 per cent. Customers that remained with Maersk during the cyberattack and its aftermath were often forced to resort to pen and paper, pasting sticky notes onto packages and then tracking them in Excel. Coordination was done on WhatsApp, which at the time became, in effect, Maersk's instant messenger outside of the United States. Maersk's ships were mostly disconnected from the network during the attack and therefore had not been infected. Moreover, ships were required to have procedures in place to handle adverse conditions, such as natural disasters, and were able to function independently. For ships that were already loaded, the impact was minimal. Seren Meyer of Maersk Tankers explained that although his division was also hit by the attack, it was able to funcon without the IT system. "It comes back to the craftsmanship of our people and the hard work of our people being able to do things with a pen and paper," he explained." Once the network restoration began, online ordering and tracking was prioritized to allow shipping services to return to normal. On July 25,2017 , Macrsk announced that its online quoting system was back online and that it was working toward clearing the backlog of delayed shipments (see Exhibit 5). COUNTING THE COST "We had to install 4,000 new servers, 45,000 new PCs, 2,500 applications," Snabe noted. "And that was done in a heroic effort over ten days. Normally - I come from the IT industry-I would say it's going to take six months. It took ten days and was a heroic effort." .51 Nevertheless, those 10 days cost the company some $300 million in expenses and lost earnings. And it would take weeks to re-image and upgrade every computer in the company. Any locally stored information on infected PCs that had not been backed up prior to the attack was forever lost, including contacts, orders, and any personal files, such as family photos. Moreover, because hackers had gained access to compromised networks for weeks or months prior to the attack, they may have siphoned valuable business and personal data from victim PCs. Given that the drives were destroyed by NotPetya, it would be impossible to determine what, if any, information had been stolen. For Snabe it was a wake-up call. "It is time to stop being nave when it comes to cybersecurity," he said, vowing to transform Maersk into a world leader in network and supply-chain security. "Many companies will be caught if they are naive. I think that it is important that we are not just reactive but proactive." EXHIBIT 1: MAERSK INCOME STATEMENTS, 20132016 (IN US\$ MILLIONS) EXHIBIT 2: MAERSK BALANCE SHEETS, 2013-2016 (IN USS MILLIONS) EXHIBIT 3: MAERSK STOCK MARKET RATIOS AND RIISINECE EXHIBIT 4: RANSOMWARE EXAMPLE If yor see this text, then your files are mo longer accessible, Decause they have been encrypted. Perhaps you are lasy looking for a way to recover your files, bat don't maste your tine. Hololy can recover your filles withont onr lecryption service. He guarantee that you can recover all your files safely and easily. All you aced to to is sabnit the raynent and parchase the decryption iney. Please follow the instractions: 1. Seal $369 worth of Ditceis to followish elfress: ine?1534h who 2. Send your Bitcoin unliet ID aud periosal imtallation liey to e-mail EXHIBIT 5: MAERSK GLOBAL UPDATE, JULY 25, 2017 Dear customer, We hope your workweek is of to a great start. As we continue our last sprint toward full recovery, we would like to share the final global update on some of the items that are of interest to you; going forward, these updates will be handled by your local Maersk Line team because, while all global applications are up and running. there are some local variances. This ensures you get frequent regional information that is relevant to your business. When we reflect on the activities of the last four weeks, we have conducted extensive work on our IT infrastructure. Concurrently, we have worked hard to dear the backlog and make sure the impact on your business has been as minimal as possible. During this process, our local teams have been required to handle lots of manual work, and everyone is looking forward to returning to servicing your business in a seamless and efficient manner. We thank you once again for your patience and support. With that, let us get to today's updates: Online Quote We are pleased to announce that the quote request form for short-term rates is now back online-avaliable globally. This means we will once again be able to give you quick and relevant shipping rates online. You can submit your quote request here: httpsi/my.maerskline.com/onlinequotel. We strive to provide you with a rate within just a few hours, but also anticipate that the increased number of requests this week might result in slightly longer response times. We know that some of you have asked for spot quotes over the last few weeks. We want to make sure that you got the most relevant and latest rate offering at hand, which means we have opted to focus on your new requests coming in through the online form. We hope you will resubmit your quote request and look forward to supporting your business. Our short-term rate sheets and long term contracting are running normally as previously advised. Submission of Advanced Manifest We can confirm that we are in full compliance with both U.S. and EU regulations related to Advanced Manifest process. It is of great importance that Shipping Instructions are submitted in due time in order to comply with Advanced Manifest deadlines. Submission deadlines will be listed on your Booking Confirmation as usual. General global status The majority of our global applications is back up and running which enables us to execute the processes to move your cargo. We are open for all your quotations. Our website is working with all functionalities; we are handing bookings through the various normal channels and processing shipping instructions, including advanced manifest submissions to relevant authorities. Our import releases and inland deliveries are also flowing, although we acknowledge we still have some challenges in certain locations due to manual processing and capacity restrictions. Lastly, we are issuing invoices online but stiil have a few remaining items to progress on local invoicing applications which we continue to work on over the next period. As we clear the last parts of the backlog and serve your new business, we acknowledge that you may stil encounter some data quality inconsistencies and delays in response times in some locations. We assure you that we are fully committed to returning to our normal standards as soon as possible. We understand that this joumey has been inconvenient and sometimes frustrating for you and we would like to thank you once again for your patience and trust in us. The kind gestures that many of you have offered our local teamsranging from offering office space and laptops, to sending cakes and encouraging words - are truly humbling and we sincerely appreclate all the support. Thank you The Maersk team