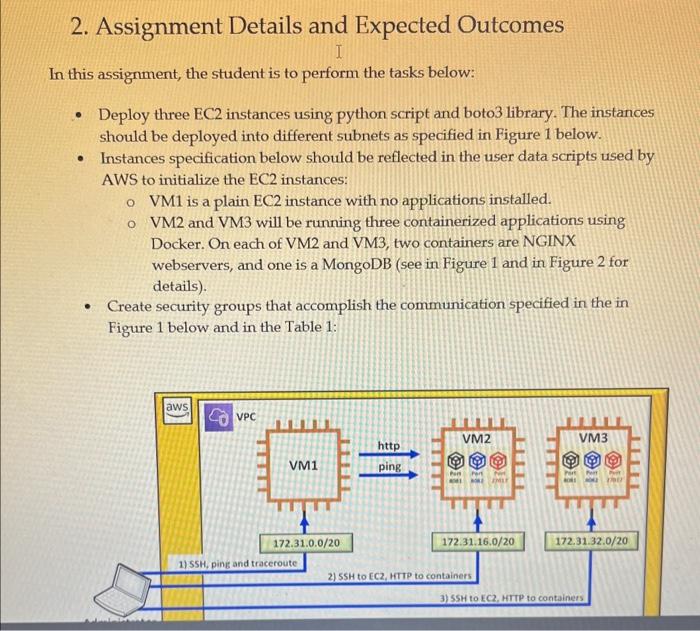
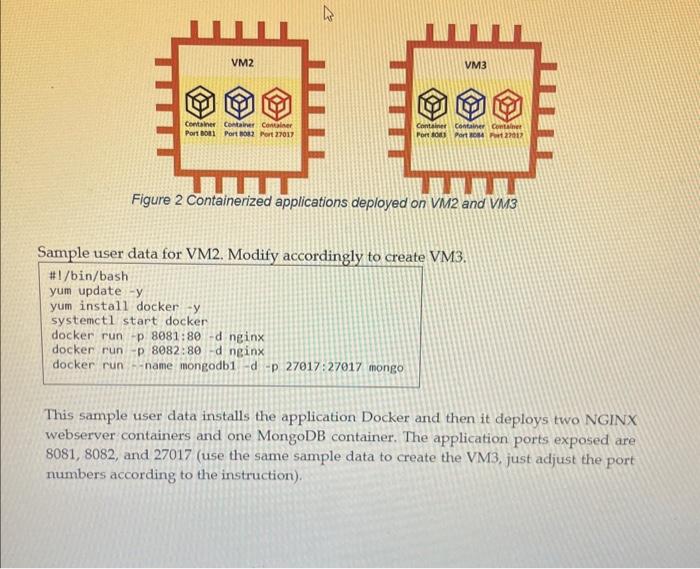
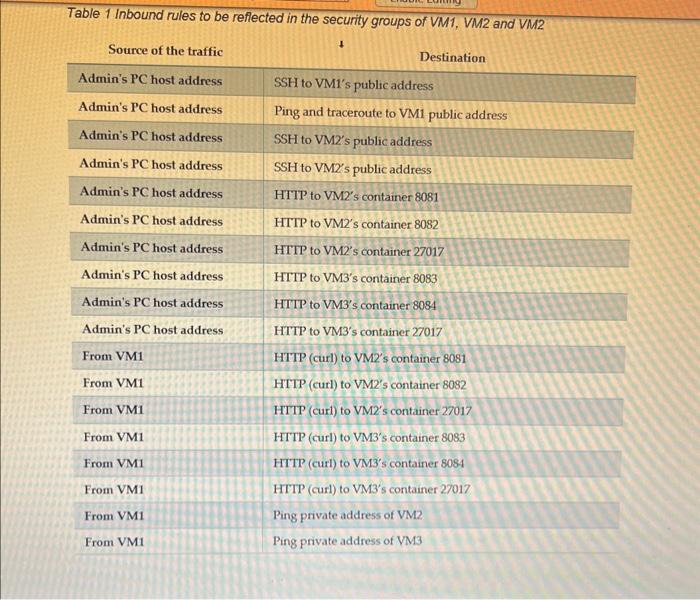
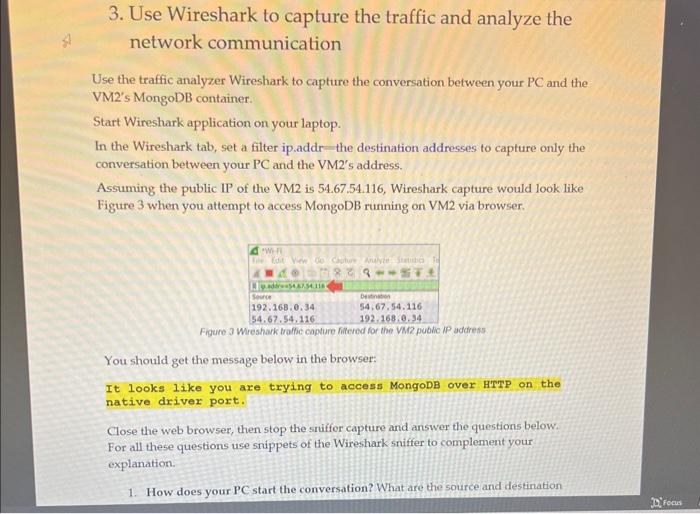
2. Assignment Details and Expected Outcomes In this assignment, the student is to perform the tasks below: - Deploy three EC2 instances using python script and boto3 library. The instances should be deployed into different subnets as specified in Figure 1 below. - Instances specification below should be reflected in the user data scripts used by AWS to initialize the EC2 instances: VM1 is a plain EC2 instance with no applications installed. VM2 and VM3 will be running three containerized applications using Docker. On each of VM2 and VM3, two containers are NGINX webservers, and one is a MongoDB (see in Figure 1 and in Figure 2 for details). - Create security groups that accomplish the communication specified in the in Figure 1 below and in the Table 1: Figure 2 Containerized applications deployed on VM2 and VM3 Sample user data for VM2. Modify accordingly to create VM3. This sample user data installs the application Docker and then it deploys two NGINX webserver containers and one MongoDB container. The application ports exposed are 8081,8082 , and 27017 (use the same sample data to create the VM3, just adjust the port numbers according to the instruction). Table 1 Inbound rules to be reflected in the security groups of VM1, VM2 and VM2 3. Use Wireshark to capture the traffic and analyze the network communication Use the traffic analyzer Wireshark to capture the conversation between your PC and the VM2's MongoDB container. Start Wireshark application on your laptop. In the Wireshark tab, set a filter ip.addr-the destination addresses to capture only the conversation between your PC and the VM2's address. Assuming the public IP of the VM2 is 54.67.54.116, Wireshark capture would look like Figure 3 when you attempt to access MongoDB running on VM2 via browser. You should get the message below in the browser: It looks like you are trying to access MongoDB over HTTP on the native driver port. Close the web browser, then stop the sniffor capture and answer the questions below. For all these questions use snippets of the Wireshark sniffer to complement your explanation. 1. How does your PC start the conversation? What are the source and destination 1. How does your PC start the conversation? What are the source and destination IPv4 addresses? What are the source and destination TCP ports? What are the TCP messages involved? 2. When does the HITP protocol appear in the conversation? What is the HTTP message sent by the PC and what is the reply? Is the conversation clear text? 3. How does the conversation end? What are the messages exchanged to close the session? 4. Submission Requirements Your submission should include 2 separate files: 1. Python script named create vms.py 2. Word document with the a. Screenshot of python code output