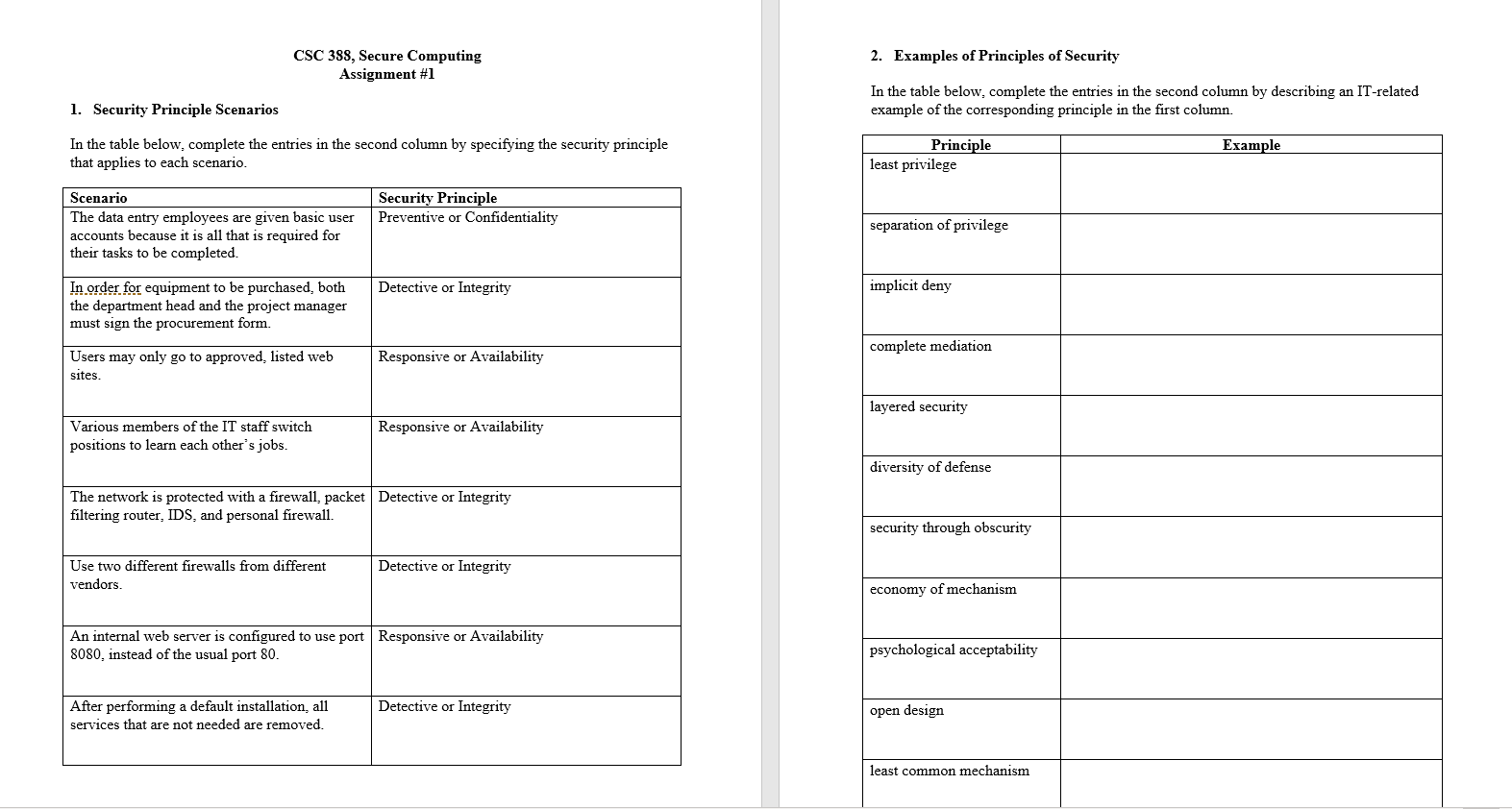
2. Examples of Principles of Security CSC 388, Secure Computing Assignment #1 In the table below, complete the entries in the second column by describing an IT-related example of the corresponding principle in the first column. 1. Security Principle Scenarios Example In the table below, complete the entries in the second column by specifying the security principle that applies to each scenario. Principle least privilege Security Principle | Preventive or Confidentiality Scenario The data entry employees are given basic user accounts because it is all that is required for their tasks to be completed. separation of privilege Detective or Integrity implicit deny In order for equipment to be purchased, both the department head and the project manager must sign the procurement form. complete mediation Responsive or Availability Users may only go to approved, listed web sites. layered security Responsive or Availability Various members of the IT staff switch positions to learn each other's jobs. diversity of defense The network is protected with a firewall, packet Detective or Integrity filtering router, IDS, and personal firewall security through obscurity Use two different firewalls from different vendors. Detective or Integrity economy of mechanism An internal web server is configured to use port Responsive or Availability 8080, instead of the usual port 80. psychological acceptability Detective or Integrity After performing a default installation, all services that are not needed are removed. open design least common mechanism 2. Examples of Principles of Security CSC 388, Secure Computing Assignment #1 In the table below, complete the entries in the second column by describing an IT-related example of the corresponding principle in the first column. 1. Security Principle Scenarios Example In the table below, complete the entries in the second column by specifying the security principle that applies to each scenario. Principle least privilege Security Principle | Preventive or Confidentiality Scenario The data entry employees are given basic user accounts because it is all that is required for their tasks to be completed. separation of privilege Detective or Integrity implicit deny In order for equipment to be purchased, both the department head and the project manager must sign the procurement form. complete mediation Responsive or Availability Users may only go to approved, listed web sites. layered security Responsive or Availability Various members of the IT staff switch positions to learn each other's jobs. diversity of defense The network is protected with a firewall, packet Detective or Integrity filtering router, IDS, and personal firewall security through obscurity Use two different firewalls from different vendors. Detective or Integrity economy of mechanism An internal web server is configured to use port Responsive or Availability 8080, instead of the usual port 80. psychological acceptability Detective or Integrity After performing a default installation, all services that are not needed are removed. open design least common mechanism







