Answered step by step
Verified Expert Solution
Question
1 Approved Answer
, 2 . . . . - upts ) - Concordia CSSE Drone Cipher Program Note: You are not allowed to use array ( s
upts Concordia CSSE Drone Cipher Program
Note: You are not allowed to use arrays for this first question.
Gina Cody School of Engineering and Computer Science drones surveying equipment and software research lab heard that you are taking OOP course and wants to hire you as a research intern; one of your key responsibilities includes sending and receiving text instructionsmessages that should not be comprehend if the drone is intercepted. Your supervisor wants to charge you with the sole responsibility of designing the drone algorithm and developing this same algorithm using Java Programming Language.
Fundamentally, this algorithm computes the encoded informationtext by pruning and preprocessing any given stringtext to ensure that the first and last characters of the stringtext is a nonspace character; thereafter, it counts the number of characters in the stringtext If the preprocessed stringtext is comprised of an even number of characters; then, the new encoded string will consist of the reverse of second half of the text, and the first half of the original text. If the preprocessed stringtext is comprised of an odd number of characters; then, the new encoded string will be composed of i the reverse of second half of the string after the middle character, ii the middle character of original string, iii the reverse of the first half of the original string before the middle character. Please see Table below for pictorial explanation.
Table Procedure for Concordia CSSE Drone Cipher algorithm.
Page of
@Dr Nora Houari
Therefore, write a Java classprogram such that your source code will accomplish the following:
Name of the classprogram: AQ
Display a welcomesalutation message to the user of the program.
Display a prompt message for the user to enter a stringtext for the cipher algorithm.
Preprocess the input stringtext as described above; and compute the corresponding ciphertext based on your proposed encoded algorithm.
Additionally, note that: if an output ciphertext of an odd length ONLY is passed through our proposed algorithm and program, then the ciphertext shall be decoded to reveal the originalplain text.
Finally, display a complimentaryclose message as follows: Thank you for your contribution to Concordia CSSE Drone Cipher Project.
The following are sample screenshots to illustrate the expected behavior of your program. Your program must display the same information, using the same format, depicted in the screenshots below.
Welcome to Concordia CSSE Drone Cipher Program:
Please enter your plain message below:
Keep right
Kindly find below your cipher message output:
thgirKeep
Thank you for your contribution to Concordia CSSE Drone Cipher Project.
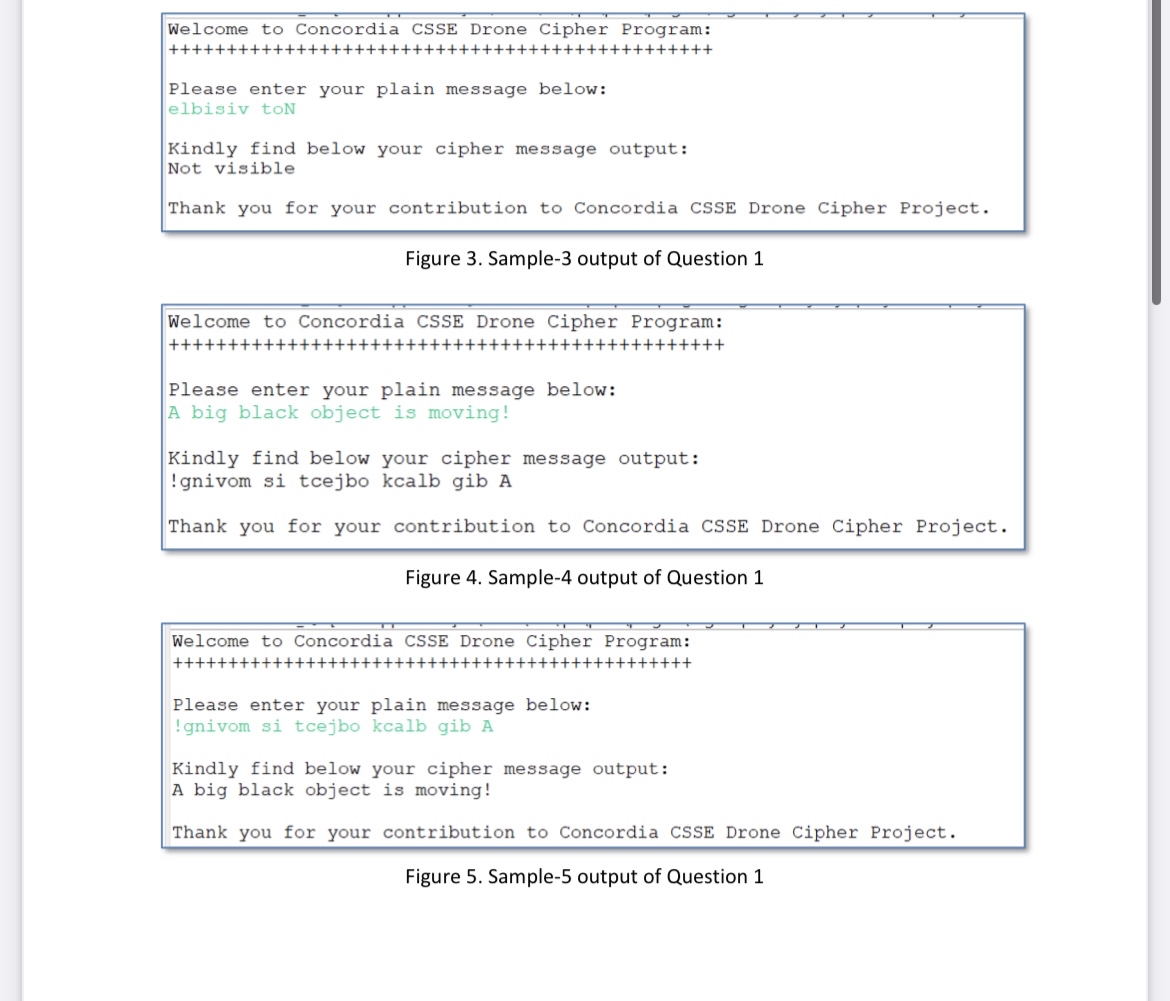
Welcome to Concordia CSSE Drone Cipher Program:
Please enter your plain message below:
elbisiv toN
Kindly find below your cipher message output:
Not visible
Thank you for your contribution to Concordia CSSE Drone Cipher Project.
Figure Sample output of Question
Welcome to Concordia CSSE Drone Cipher Program:
Please enter your plain message below:
A big black object is moving!
Kindly find below your cipher message output:
gnivom si tcejbo kcalb gib A
Thank you for your contribution to Concordia CSSE Drone Cipher Project.
Figure Sample output of Question
Welcome to Concordia CSSE Drone Cipher Program:
Please enter your plain message below:
gnivom si tcejbo kcalb gib A
Kindly find below your cipher message output:
A big black object is moving!
Thank you for your contribution to Concordia CSSE Drone Cipher Project.
Figure Sample output of Question
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


