Question: 2.1 Task 1: Frequency Analysis Against Monoalphabetic Substitution Cipher It is well-known that monoalphabetic substitution cipher (also known as monoalphabetic cipher) is not secure, because
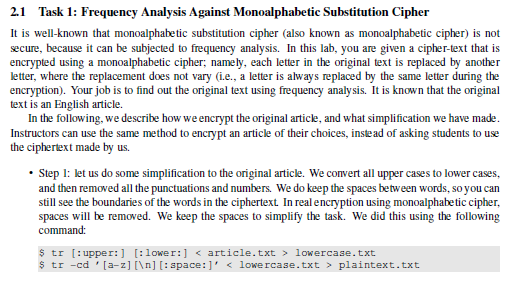

2.1 Task 1: Frequency Analysis Against Monoalphabetic Substitution Cipher It is well-known that monoalphabetic substitution cipher (also known as monoalphabetic cipher) is not secure, because it can be subjected to frequency analysis. In this lab, you are given a cipher-text that is encrypted using a monoalphabetic cipher, name ly, each letter in the original text is replaced by another letter, where the replacement does not vary (i.e., a letter is always replaced by the same letter during the encryption). Your job is to find out the original text using frequency analy sis. I is known that the original text is an English article. In the following, we describe how we encrypt the original article, and what simplification we have made. Instructors can use the same method to encrypt an article of their choices, inste ad of asking students to use the ciphertext made by us. Step I: let us do some simplification to the original article. We convert all upper cases to lower cases, and then removed all the punctuations and numbers. We do keep the spaces between words, so you can still see the boundaries of the words in the ciphertext. In real encryption using monoalphabetic cipher, spaces will be removed. We keep the spaces to simplify the task. We did this using the following command: $ tr [upper: lower:article.txt lowercase.txt $ tr -cd , [a-z] [ ] [: space: ], plaintext.txt 2.1 Task 1: Frequency Analysis Against Monoalphabetic Substitution Cipher It is well-known that monoalphabetic substitution cipher (also known as monoalphabetic cipher) is not secure, because it can be subjected to frequency analysis. In this lab, you are given a cipher-text that is encrypted using a monoalphabetic cipher, name ly, each letter in the original text is replaced by another letter, where the replacement does not vary (i.e., a letter is always replaced by the same letter during the encryption). Your job is to find out the original text using frequency analy sis. I is known that the original text is an English article. In the following, we describe how we encrypt the original article, and what simplification we have made. Instructors can use the same method to encrypt an article of their choices, inste ad of asking students to use the ciphertext made by us. Step I: let us do some simplification to the original article. We convert all upper cases to lower cases, and then removed all the punctuations and numbers. We do keep the spaces between words, so you can still see the boundaries of the words in the ciphertext. In real encryption using monoalphabetic cipher, spaces will be removed. We keep the spaces to simplify the task. We did this using the following command: $ tr [upper: lower:article.txt lowercase.txt $ tr -cd , [a-z] [ ] [: space: ], plaintext.txt
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


