Answered step by step
Verified Expert Solution
Question
1 Approved Answer
2.5 Task 3: Exploiting the buffer-overflow vulnerability We are ready to create the content of badfile. Since the content involves some binary data (e.g., the

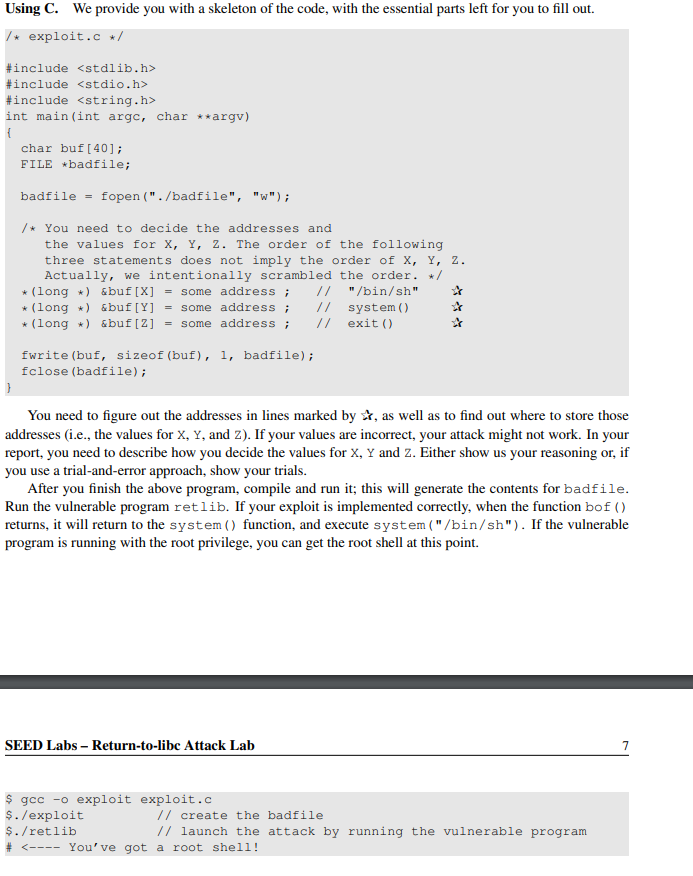

2.5 Task 3: Exploiting the buffer-overflow vulnerability We are ready to create the content of badfile. Since the content involves some binary data (e.g., the address of the libc functions), we can use C or Python to do the construction. Using Python. We provide you with a skeleton of the code, with the essential parts left for you to fill out. #!/usr/bin/python3 import sys # Fill content with non-zero values content = bytearray (Oxaa for i in range (300)) SEED Labs - Return-to-libc Attack Lab sh_addr = 0x00000000 # The address of "/bin/sh" content [X:X+4] = (sh_addr).to_bytes (4, byteorder='little') system_addr = 0x00000000 # The address of system) content [Y:Y+4] = (system_addr).to_bytes (4, byteorder='little') exit_addr = 0x00000000 # The address of exit() content [2:2+4] = (exit_addr).to_bytes (4, byteorder='little') # Save content to a file with open ("badfile", "wb") as f: f.write (content) You need to figure out the three addresses and the values of X, Y, and Z. If your values are incorrect, your attack might not work. In your report, you need to describe how you decide the values for X, Y and Z. Either show us your reasoning or, if you use a trial-and-error approach, show your trials. Using C. We provide you with a skeleton of the code, with the essential parts left for you to fill out. /* exploit.c */ #include
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


