Answered step by step
Verified Expert Solution
Question
1 Approved Answer
2.Consider the CBC-MAC from the following figure, and suppose that the encryption on key k1 (i.e., the last encryption block) is omitted. Show that such
2.Consider the CBC-MAC from the following figure, and suppose that the encryption on key k1 (i.e., the last encryption block) is omitted. Show that such the MAC system is not secure.
Hint: Choose an arbitrary one-block message m X, query the challenger for m and obtain its tag t = F(k,m). Now, find a two-block message m, such that t is a valid tag for m as well.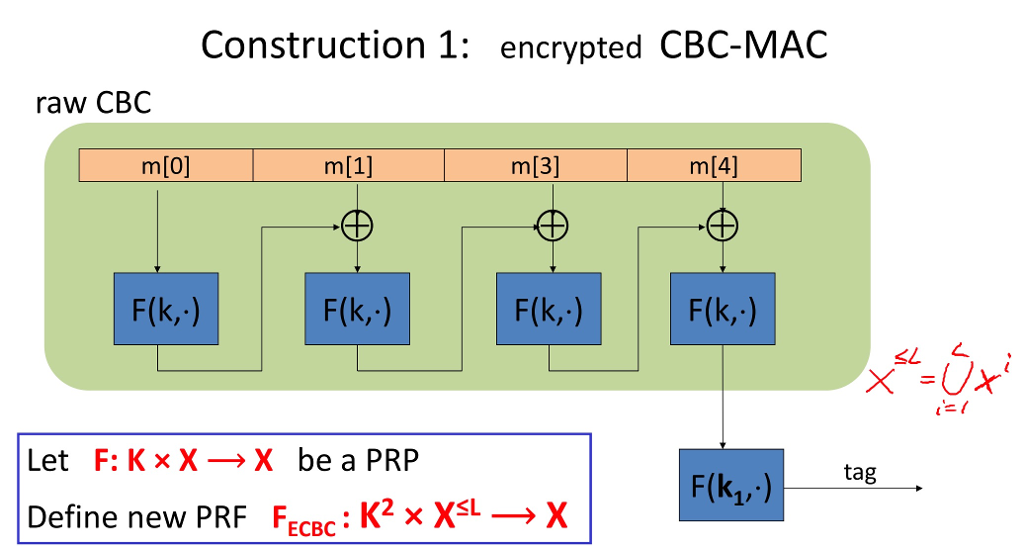
Construction 1 encrypted CBC-MAC raw CBC mo) m[0] m(3] m[4] F(k,) ( Let F: KXX be a PRP Define new PRF FECBC . K2x XsL X F(k,)tag 1/ Construction 1 encrypted CBC-MAC raw CBC mo) m[0] m(3] m[4] F(k,) ( Let F: KXX be a PRP Define new PRF FECBC . K2x XsL X F(k,)tag 1/
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


