
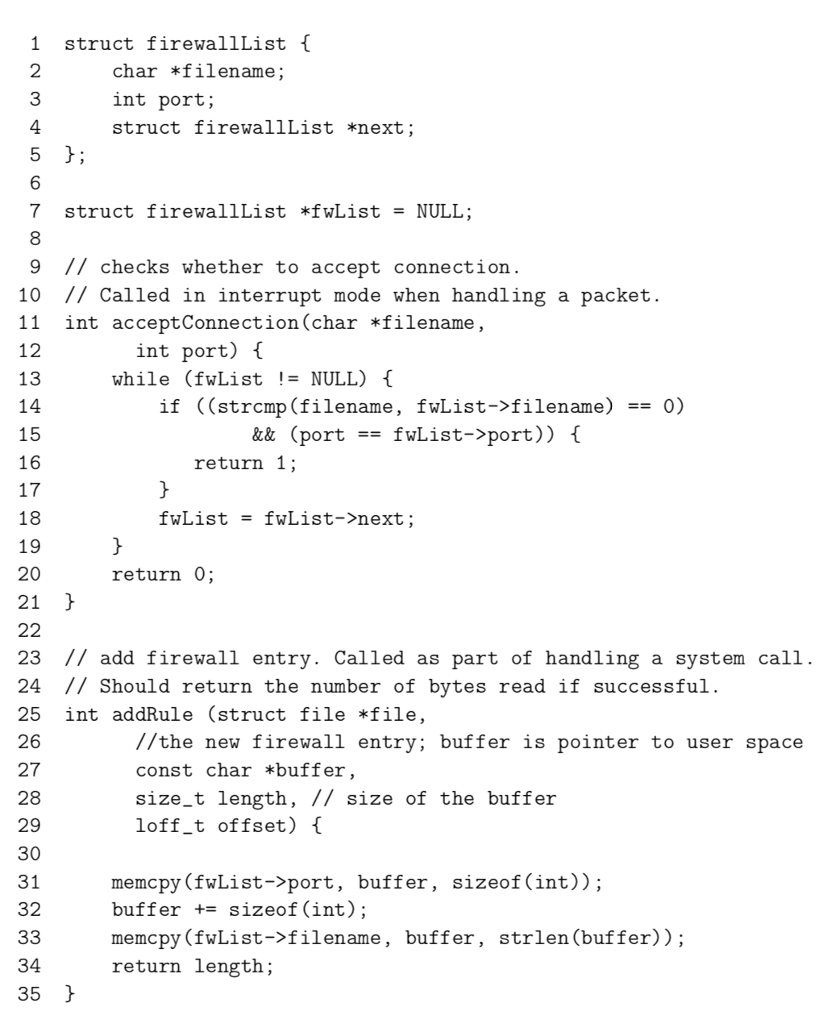
3. (a) What is the effect of a memory leak in the kernel? [4 marks] (b) Why is it important that critical sections in kernel code are as short as possible? [4 marks] (c) You are asked to write a device driver for a new USB device. It is important that errors in the device driver cause as few system crashes as possible. Would you prefer a microkernel architecture or a monolithic architecture for this device [4 marks] (d) Consider the kernel code fragment on the next page. This code is part of the firewall extension of the linux kernel. The intention is that the procedure addRule is called as part of a system call whenever the user writes to a file in the proc-directory to add a new firewall rule. The procedure acceptConnection is driver? Justify your answer called in interrupt mode and checks whether the connection should accepted This code does not work as intended. It contains errors not necessarily limited to memory management and concurrency. Identify the errors and suggest a remedy. Your solution should maximise the degree of concurrency. For critical sections, it is enough to indicate the beginning and end of a critical section, and [8 marks] whether you would use semaphores or spinlocks. 1 struct firewallList f 2 3 4 char *filename; int port; struct firewallList *next; 6 7 struct firewall1st *fwList= NULL ; 8 9 // checks whether to accept connection 10 // Called in interrupt mode when handling a packet. 11 int acceptConnection(char *filename, 12 13 14 15 16 17 18 19 20 21 int port) while (fwlist != NULL) { if ((strcmp(filename, fwList->filename) 0) && (portfwList->port)) return 1; fwlist = fwlist->next; return 0; 23 // add firewall entry. Called as part of handling a system call. 24 //Should return the number of bytes read if successful. 25 int addRule (struct file file 26 27 28 29 30 31 32 //the new firewall entry; buffer is pointer to user space const char *buffer, size_t length, // size of the buffer loff_t offset) memcpy(fwList->port, buffer, sizeof (int)); buffer+- sizeof (int) memcpy(fwList->filename, buffer, strlen(buffer)); return length; 34 35








