Answered step by step
Verified Expert Solution
Question
1 Approved Answer
3. Alice and Bob are employees residing in two dispersed branches, D1 and D2, of the same company. They want to secure all the
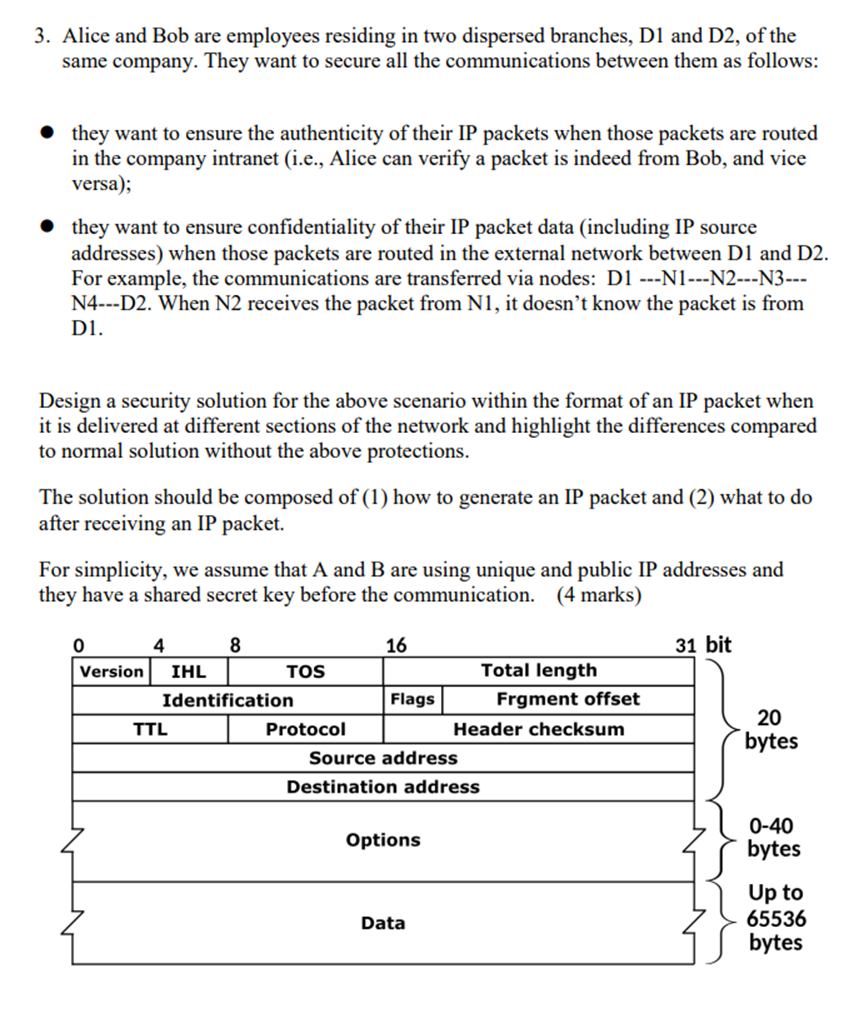
3. Alice and Bob are employees residing in two dispersed branches, D1 and D2, of the same company. They want to secure all the communications between them as follows: they want to ensure the authenticity of their IP packets when those packets are routed in the company intranet (i.e., Alice can verify a packet is indeed from Bob, and vice versa); they want to ensure confidentiality of their IP packet data (including IP source addresses) when those packets are routed in the external network between D1 and D2. For example, the communications are transferred via nodes: D1 ---N1---N2---3--- N4---D2. When N2 receives the packet from N1, it doesn't know the packet is from D1. Design a security solution for the above scenario within the format of an IP packet when it is delivered at different sections of the network and highlight the differences compared to normal solution without the above protections. The solution should be composed of (1) how to generate an IP packet and (2) what to do after receiving an IP packet. For simplicity, we assume that A and B are using unique and public IP addresses and they have a shared secret key before the communication. (4 marks) 0 4 8 16 31 bit Version IHL TOS Total length Identification Flags Frgment offset TTL Protocol Header checksum Source address Destination address Options Data 20 bytes 0-40 bytes Up to 65536 bytes
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


