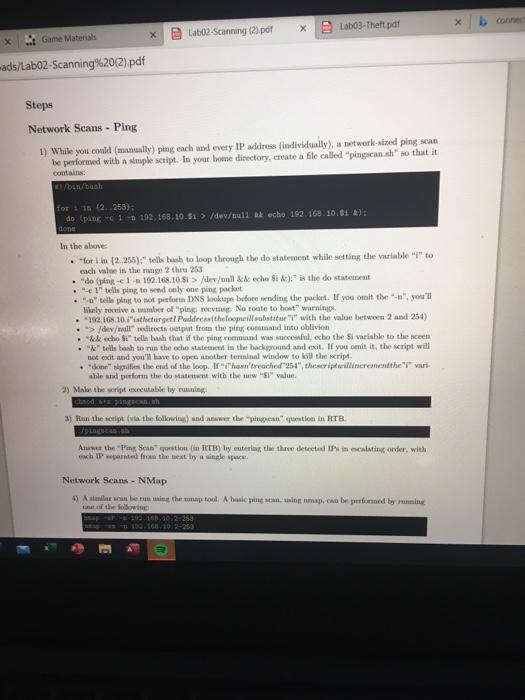
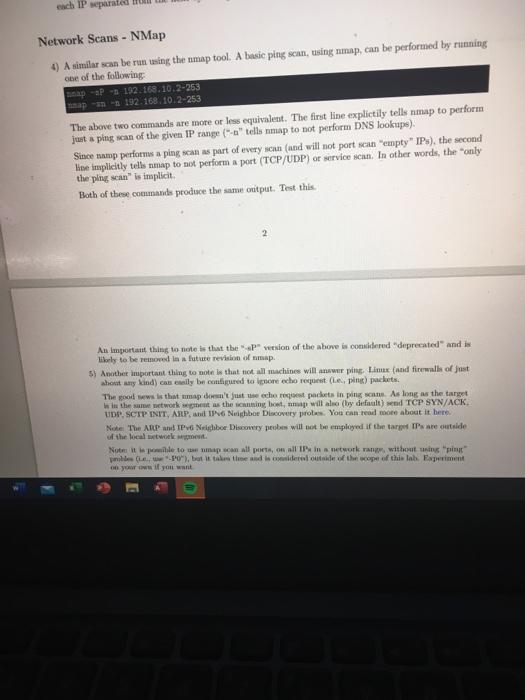
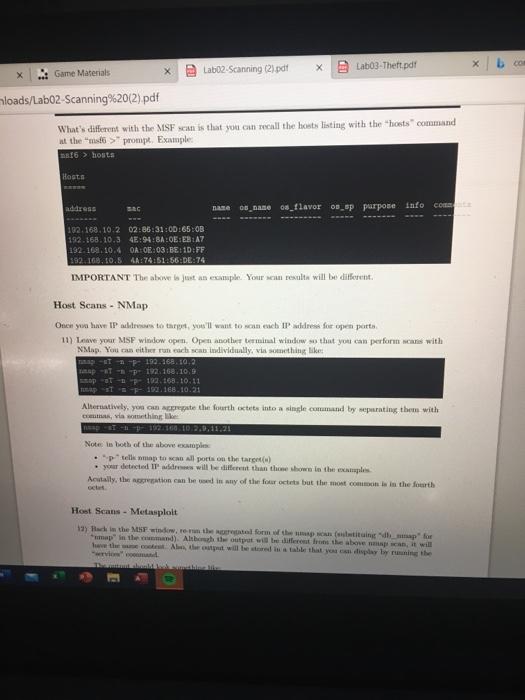
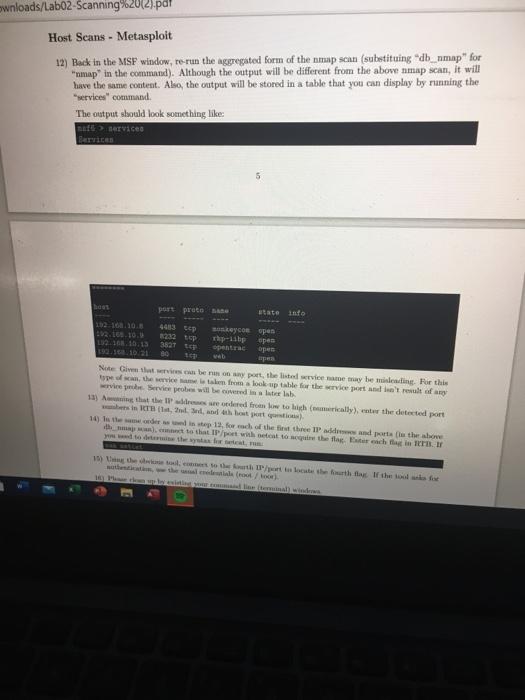
(31 Lab03-Thelt.pdf Labo2-Scanning (2) pdf Game Materials als/Labo2-Scanning%20(2).pdf ITN-261 - Lab 02 - Scanning Task: There are a number of machines in the 192.168.10.X network. In this lab, you'll employ ping, nmap, and Metasploit to detect them Set Up For this lab, you'll need to install NMap and the Metasploit Framework (aka MSF). If you hadn't already figured it out, your desktop machine is Kall-based. NMap and MSF can be accomplished by running the following apt-get update apt-get upgrade y apt-get install -y map netasploit framework netcat-traditional In the above, the first line tells apt-get to update its database of available packages. The second line tells apt-get to install packages for any out-of-date but already installed packages (they tells apt-get to not ask questions. The third line tells apt-get to install the not yet installed packages for nmap and the metaploit framework. Because Kull (and its Debian bose) are constantly updated, the second line will undoubtedly take a few minutes to complete. The third line will also install a large number of packages. Please be patient if ether appears to have alle. IMPORTANT: There are a ton of tools available for installation on your Kall desktops. Please refrain from installing anything other than what's needed for the Intes as this is a shared environment with somewhat limited resource. In any case, trything extra installed without direction will be deleted during the Saturday morning matenne period. For the lab your target machines reside in the 192.168.10.x IP range. When running scans, please exclude the following IP address from scan/attacks, for the noted 192.168.10.1 - this is the IP ads for your desktop machine 192.168.10.254-thie to the IP address for the Guacamole machine 192.168.10.255 - this is the broadcast address for the network sement The last problematic thing that you can do by attacking the above is drive yourself offline. The most problematie thing that you can do is drive other students ofline A filmtal of Kall includes a number of warning and custom prompts that you'll want to disable because your desktop machine is utally s Doder container, ban on the Kali distribution). Run the following to connect Labo2-Scanning (2).pdf * Lab03-Theft pdf Game Materials loads/Lab02 Scanning%20(2).pdf meso complete the trane wiruso instantagem or packages. Please be patienten appears to have stalled. IMPORTANT: There are a ton of tools available for installation on your Kali desktops. Please refrain from Installing anything other than what's needed for the labs in this is a shared environment with somewhat limited resources. In any case, anything extra, installed without direction, will be deleted during the Saturday morning maintenance period For this lab, your target machines reside in the 192.168.10.x IP range. When running scans, please exclude the following IP address from scans/attacks, for the noted 192.168.10.1 - this is the IP address for your desktop machine 192.168.10.254 - this ts the IP address for the Guacamole machine . 192.168.10.255 - this is the broadcast address for the network segment The last problematic thing that you can do by attacking the above is drive yourself olie. The most problematic thing that you can do is drive other students offline A full install of all includes tumber of warning and custom prompts that you'll want to disable became your desktop machines acutally a Docker container, bund on the Kali distribution). Run the following to disable thowe warnings soch / butthogan Performing the shove should make your command line output much more readable by excluding the warning Also, you'll only need to perform this once as the Docker container for your desktop bus persistent storage for anything place in the root directory Step Network Seans - Pins E Conne X Lab03-Theft pdf Lab02-Scanning (2).pdf Game Mate ED mads/Labo2-Scanning%20(2) pdf Steps Network Scans - Ping 1) While you could (tally) plug each and every IP address (individually), a network-sized ping scan be performed with a simple script in your home directory, create a file called "pingsanah" so that it contains /bin/but for 3 12 253): do (pine 1192.168.10.$1 > /devulla echo 192.168.10.01) done In the above . for In (2.255)," tells us to loop through the dostatement while setting the variable to each vole in the range 2 thru 253 "do (ping-c1-192.168.10.51 /dev/well & echo si X) is the de statement "c1" tells ping to od only one pin pacat * telle plug to not perform DNS lookupe before winding the packet. If you omit the ", you'll likely receive a umber of "ping V No route to host warning 192.168.10.thefarget Paddrettheloopillabate with the value between 2 and 254) *> /devul redirects output from the pink command into oblivion cho Sl" tello bash that if the ring commund w ceful echo the Si variable to the ween "*" tells bash to run the echo statement in the background and excit, If you omit it, the script will not edit and you'll have to open another terminal window to kill the script doon spil the end of the loop. If he reached 254" theatriptilierementthe" vari- while and perform the down with the value 2) Make the script executabilely running chanda Pranh 3) Run the script (via the folkwinand wer bepingan" question in RTB Atver the Prime Sagastion in they entering the three detected IP in calating order with och Iwata from the best by a single pe Network Scans - NMap 4) A berunt the map tool A hasi nga, marformed by me of the following 293.160.10 2.253 193 16.10.2-253 each IP separate Network Scans - NMap 4) A similar scan be run using the map tool. A basic ping scan, using nmp, can be performed by running one of the following map -* -* 192.163.10.2-253 map - 192.168.10.2-253 The above two commands are more or less equivalent. The first line explictily tells map to perform just a ping scan of the given IP range("tels nmap to not perform DNS lookups) Since namp performs a ping scan as part of every scan (and will not port sean "empty" IPs), the second line implicitly tells nmap to not perform a port (TCP/UDP) or service scan. In other words, the only the pingsan" is implicit Both of these commande produce the same output. Test this An important thing to note is that the version of the above is considered deprecated and is likely to be removed in a future revision of map. 5) Another important thing to note is that not all machines will aww ping Linux (and firewall of just shout any kind) can telly be configured to ignore echo request (e ping) packets The good ws is that tmap doesn't juste echo request packets in pingan. As long as the target les in the network as the woning bond, map will alma (by default) od TCP SYN/ACK UDP, SCIP INIT, ATP, and 146 Neighbor Discovery prou. You can read more about it here Note The ARP TP Neighbor Discovery probes will not be employed if the target IP are outside Note the posle townmap on all ports, on all Pin a network rate without using pin mo, but it is the distride of the cope of this lab. Experiment on you want Then Game Materials Downloads/Labo2-Scanning%20(2).pdf An important thing to note is that the *-*P version of the above is considered "deprecated and is likely to be removed in a future revision of map 5) Another important thing to note is that not all machines will answer pig. Linux (and firewalls of just about any kind) can easily be configured to ignore echo request (le, ping) packets. The good news is that map doesn't just seecho request packets in pingsans. As long as the target is in the same network wegment as the scanning hot, map will also by default) send TCP SYN/ACK, UDP, SCTP INIT, ARP, and IPv6 Neighbor Discovery probes. You can read more about it here. Note: The ARP and IPv6 Neighbor Discovery probes will not be employed if the target IP are outside of the local network tot Noter it is posible to use map an all porta, on all IP in a network range, without using "ping" pwobles (PO), but it takes time and is considered outside of the scope of this lab. Experiment on your own if you want The points to get on with this part of the lab is *) KNOW YOUR ENVIRONMENT. You'll need to remember which machine is configured to respond to what. OR b) If you don't know the environment. KNOW YOUR TOOLS' LIMITATIONS. 6) Look at the son output in step 4 (above). Determine which IP appeared in the map scan that didn't appear in the pingsan Enter that the answer to the map Hot Sean question in RTB Network Scans - Metasploit 7) in a later labs, you'll be running MSF to attack target machines. Then now, you'll fint want to perform a network in to determine target IP addre. The good news is that MSF Incorporates Map and can evebate Map' otput in a recall able table. Before you start MSF, you'll need to perform a comple steps to start the PostgreSQL service on which MSFr. This complished by run Vetc/init.d/start The output from the we will look something dek-O703 /etc/init.d/peater Bearing PL 13 e 1 If you're rum. MSF is your name you can enre your system to start agreSQL when your system. How became all machines actually Docker conta, it doesn't include the wyse command and you never to the method for starting and dopping the datab If this the time you'w MSF'll need to configure the date to apport MSP The complished via 3 loads appear in the ping scan. Enter that as the answer to the Nmap Host Scan Network Scans - Metasploit 7) In a later lab, you'll be running MSF to attack target machines. Then, as now, you'll first want to perform a network scan to determine target IP addresses. The good news is that MSF incorporates NMap and can eveb store Map's ouput a recall able table Before you start MSF, you'll need to perform a couple steps to start the PostgreSQL service on which MSF relies. This is accomplished by running fotelinit.d/postgresql start The output from the above will look something like zoutodesk-070:-1 /etc/init.d/postgresql start Starting PostgreSQL 13 database server main If you're running MSF in your own machine, you can configure your system to start PostgreSQL when your system boots. However, because your Kall machine is actually a Dockor container, it doesn't include the systemet command and you must revert to the older methods for starting and stopping the If this is the first time you ve MSF. you'll need to configure the PostgreSQL database to support MSF. This is accomplished in bant The output should look something like Bek OTOR INI System has not been booted with ayatend an init nyaten (PID 1). Can't operate. Failed 18 Conect to bus Bont is down Starting database Systen hast been booted with watendait system (ID 1). Can't operate. Failed to connect to but lost in down E GD Lab02.Scanning (2) pdf Lab03-Theft.pdf Game Matenals nloads/Lab02-Scanning%20(2).pdf Creating database user 'mat' c) Creating databases To Creating databases of test! Creating configuration file "/usr/shareetasploit-framework/config/database. yni' (0) Creating initial database aches From Tim: If there's a "Message from Kall developers" mixed into the above, ignore it/them. The developers didn't have enough foresight to remember that Kali is also distributed a Docker container and their disable this feature" feature is broken. With time, I'll have this defeated, Note: if you've previously performed the midb init" step, and you're re-running it, the command will complain about such and exit. This is a nour, no-foul situation and the warnings can be ignored. You only need to run it once. (In ITN-2015 ce, because the destops are rebuilt every Saturday morning, you'll need to run it weekly, after each maintense period.) 8) Expand the size of your terminal window so that it takes up much of the real estate on your desktop. 9) Start MSF by running console Till goes well, your terminal window should now show an ASCII graphic (it changes every time you rosole"), followed by a blurb about the current wrsion of MSF. Examples petasploit v0.0.26-day 2092 exploits - 1127 Blaty - 365 post 582 payloads - 45 cedere - 10 Bapa Wwtasploit sip Adapters can be used for IP par LIST ID As the prompt Indiester, you wering Metasploit 10) When you see the wall>prompt you can run bon command line table and the output will show (complet Woonfig). However, the output will not be fod hack into MSF. The local map Tomap, it's built into MSF. re-run the above map scan (from step 4) but mapind of map The Command witches can be The output from the cute to the command Lo pot tor 102.168.10:2 0.0000 latacy Lola Adres 02:16:31:00:56:00 (US) x Game Materials Lab02-Scanning (21.pdf X Labo.Theft pdf b connect ip and Downloads/Labo2-Scanning%2012).pdf 10) When you see the prompt, you can run just about any command line executable and the outpat will show as normal (example ifconfig). However, the output will not be fed back into MSF This includes map Towmapite built into MISF, the above map scan (from step :) but bump" tamp"The commande switches can be used In other words, Rana dbp. 192.168.10.2-253 The output from the should look quite ar to the normal' nmap commande 1688 192.168.10.2-253 Map Starting Map 7.81 (https://por A 2021-01-23 03: Col Saap! Noap Scan report for 192.168.10.2 Collapot is up (0.000266 latency) Leap! MAC Address: 02166:31:00:65:00 (Unknown Copiap scan report for 192.168.10.3 Claptons up prompt. Example 316 > tota Hosts address EC 06_Bano 05_flavor 05_sp purpose info COS 192.168.10.2 02:36:31:00:65:03 192.168.10.3 4E194:BALEEB1A7 192.168.10.4 00:03:BE:10:FF 192.168, 10,5 4:74:51:56:DE:74 IMPORTANT The above is just an emple. Your results will be different Host Scans - NMap Omen you have I below to thepet, you'll want to sain each IP wildress for pen ports, 11) Leave your MSF window open Open another terminal window so that you can performans with Map. You can eithet run each scan individually via something like 192.168.10,2 map -AT-17 192.168.10,9 op at EP 192.168.10.11 ERP STF 190.168.10.21 Alternatively, you om oregate the fourthotels into a single command by wpurting them with centras, va comething like Notes les both of the above tople op tells map to an all ports on the targe) your detected I will be diferent than the shown in the examples Acutally, the con can be din ny of the four octets but the most common in the fourth Host Scans - Metasploit 19) In the MSF endow, to the tal form och titing map" for umapit mand). Altbach output will be different from the above can, it will Vio wwnloads/Lab02-Scanning%20(2).pdf Host Scans - Metasploit 12) Back in the MSF window, re-run the aggregated form of the map scan (substituing "db_nmap" for "map" in the command). Although the output will be different from the above map scan, it will have the same content. Also, the output will be stored in a table that you can display by running the services command The output should look something like rvices Berri por prate te no 102 103 108 4483 Sep so. Cosapen 12.10.10 hp-bp open 102 16.10.13 pentrs opes 80 web pes Not Give that we be a port, the listed as being. For this pesan, the were taken from a look up table for the videre vie pe Service probe will be disa telah 13) that thered from toch (cally), the detected pont in the bott) 14) is the destep 12.fowach the feet the IP window the home de to that with to the teachi TB (31 Lab03-Thelt.pdf Labo2-Scanning (2) pdf Game Materials als/Labo2-Scanning%20(2).pdf ITN-261 - Lab 02 - Scanning Task: There are a number of machines in the 192.168.10.X network. In this lab, you'll employ ping, nmap, and Metasploit to detect them Set Up For this lab, you'll need to install NMap and the Metasploit Framework (aka MSF). If you hadn't already figured it out, your desktop machine is Kall-based. NMap and MSF can be accomplished by running the following apt-get update apt-get upgrade y apt-get install -y map netasploit framework netcat-traditional In the above, the first line tells apt-get to update its database of available packages. The second line tells apt-get to install packages for any out-of-date but already installed packages (they tells apt-get to not ask questions. The third line tells apt-get to install the not yet installed packages for nmap and the metaploit framework. Because Kull (and its Debian bose) are constantly updated, the second line will undoubtedly take a few minutes to complete. The third line will also install a large number of packages. Please be patient if ether appears to have alle. IMPORTANT: There are a ton of tools available for installation on your Kall desktops. Please refrain from installing anything other than what's needed for the Intes as this is a shared environment with somewhat limited resource. In any case, trything extra installed without direction will be deleted during the Saturday morning matenne period. For the lab your target machines reside in the 192.168.10.x IP range. When running scans, please exclude the following IP address from scan/attacks, for the noted 192.168.10.1 - this is the IP ads for your desktop machine 192.168.10.254-thie to the IP address for the Guacamole machine 192.168.10.255 - this is the broadcast address for the network sement The last problematic thing that you can do by attacking the above is drive yourself offline. The most problematie thing that you can do is drive other students ofline A filmtal of Kall includes a number of warning and custom prompts that you'll want to disable because your desktop machine is utally s Doder container, ban on the Kali distribution). Run the following to connect Labo2-Scanning (2).pdf * Lab03-Theft pdf Game Materials loads/Lab02 Scanning%20(2).pdf meso complete the trane wiruso instantagem or packages. Please be patienten appears to have stalled. IMPORTANT: There are a ton of tools available for installation on your Kali desktops. Please refrain from Installing anything other than what's needed for the labs in this is a shared environment with somewhat limited resources. In any case, anything extra, installed without direction, will be deleted during the Saturday morning maintenance period For this lab, your target machines reside in the 192.168.10.x IP range. When running scans, please exclude the following IP address from scans/attacks, for the noted 192.168.10.1 - this is the IP address for your desktop machine 192.168.10.254 - this ts the IP address for the Guacamole machine . 192.168.10.255 - this is the broadcast address for the network segment The last problematic thing that you can do by attacking the above is drive yourself olie. The most problematic thing that you can do is drive other students offline A full install of all includes tumber of warning and custom prompts that you'll want to disable became your desktop machines acutally a Docker container, bund on the Kali distribution). Run the following to disable thowe warnings soch / butthogan Performing the shove should make your command line output much more readable by excluding the warning Also, you'll only need to perform this once as the Docker container for your desktop bus persistent storage for anything place in the root directory Step Network Seans - Pins E Conne X Lab03-Theft pdf Lab02-Scanning (2).pdf Game Mate ED mads/Labo2-Scanning%20(2) pdf Steps Network Scans - Ping 1) While you could (tally) plug each and every IP address (individually), a network-sized ping scan be performed with a simple script in your home directory, create a file called "pingsanah" so that it contains /bin/but for 3 12 253): do (pine 1192.168.10.$1 > /devulla echo 192.168.10.01) done In the above . for In (2.255)," tells us to loop through the dostatement while setting the variable to each vole in the range 2 thru 253 "do (ping-c1-192.168.10.51 /dev/well & echo si X) is the de statement "c1" tells ping to od only one pin pacat * telle plug to not perform DNS lookupe before winding the packet. If you omit the ", you'll likely receive a umber of "ping V No route to host warning 192.168.10.thefarget Paddrettheloopillabate with the value between 2 and 254) *> /devul redirects output from the pink command into oblivion cho Sl" tello bash that if the ring commund w ceful echo the Si variable to the ween "*" tells bash to run the echo statement in the background and excit, If you omit it, the script will not edit and you'll have to open another terminal window to kill the script doon spil the end of the loop. If he reached 254" theatriptilierementthe" vari- while and perform the down with the value 2) Make the script executabilely running chanda Pranh 3) Run the script (via the folkwinand wer bepingan" question in RTB Atver the Prime Sagastion in they entering the three detected IP in calating order with och Iwata from the best by a single pe Network Scans - NMap 4) A berunt the map tool A hasi nga, marformed by me of the following 293.160.10 2.253 193 16.10.2-253 each IP separate Network Scans - NMap 4) A similar scan be run using the map tool. A basic ping scan, using nmp, can be performed by running one of the following map -* -* 192.163.10.2-253 map - 192.168.10.2-253 The above two commands are more or less equivalent. The first line explictily tells map to perform just a ping scan of the given IP range("tels nmap to not perform DNS lookups) Since namp performs a ping scan as part of every scan (and will not port sean "empty" IPs), the second line implicitly tells nmap to not perform a port (TCP/UDP) or service scan. In other words, the only the pingsan" is implicit Both of these commande produce the same output. Test this An important thing to note is that the version of the above is considered deprecated and is likely to be removed in a future revision of map. 5) Another important thing to note is that not all machines will aww ping Linux (and firewall of just shout any kind) can telly be configured to ignore echo request (e ping) packets The good ws is that tmap doesn't juste echo request packets in pingan. As long as the target les in the network as the woning bond, map will alma (by default) od TCP SYN/ACK UDP, SCIP INIT, ATP, and 146 Neighbor Discovery prou. You can read more about it here Note The ARP TP Neighbor Discovery probes will not be employed if the target IP are outside Note the posle townmap on all ports, on all Pin a network rate without using pin mo, but it is the distride of the cope of this lab. Experiment on you want Then Game Materials Downloads/Labo2-Scanning%20(2).pdf An important thing to note is that the *-*P version of the above is considered "deprecated and is likely to be removed in a future revision of map 5) Another important thing to note is that not all machines will answer pig. Linux (and firewalls of just about any kind) can easily be configured to ignore echo request (le, ping) packets. The good news is that map doesn't just seecho request packets in pingsans. As long as the target is in the same network wegment as the scanning hot, map will also by default) send TCP SYN/ACK, UDP, SCTP INIT, ARP, and IPv6 Neighbor Discovery probes. You can read more about it here. Note: The ARP and IPv6 Neighbor Discovery probes will not be employed if the target IP are outside of the local network tot Noter it is posible to use map an all porta, on all IP in a network range, without using "ping" pwobles (PO), but it takes time and is considered outside of the scope of this lab. Experiment on your own if you want The points to get on with this part of the lab is *) KNOW YOUR ENVIRONMENT. You'll need to remember which machine is configured to respond to what. OR b) If you don't know the environment. KNOW YOUR TOOLS' LIMITATIONS. 6) Look at the son output in step 4 (above). Determine which IP appeared in the map scan that didn't appear in the pingsan Enter that the answer to the map Hot Sean question in RTB Network Scans - Metasploit 7) in a later labs, you'll be running MSF to attack target machines. Then now, you'll fint want to perform a network in to determine target IP addre. The good news is that MSF Incorporates Map and can evebate Map' otput in a recall able table. Before you start MSF, you'll need to perform a comple steps to start the PostgreSQL service on which MSFr. This complished by run Vetc/init.d/start The output from the we will look something dek-O703 /etc/init.d/peater Bearing PL 13 e 1 If you're rum. MSF is your name you can enre your system to start agreSQL when your system. How became all machines actually Docker conta, it doesn't include the wyse command and you never to the method for starting and dopping the datab If this the time you'w MSF'll need to configure the date to apport MSP The complished via 3 loads appear in the ping scan. Enter that as the answer to the Nmap Host Scan Network Scans - Metasploit 7) In a later lab, you'll be running MSF to attack target machines. Then, as now, you'll first want to perform a network scan to determine target IP addresses. The good news is that MSF incorporates NMap and can eveb store Map's ouput a recall able table Before you start MSF, you'll need to perform a couple steps to start the PostgreSQL service on which MSF relies. This is accomplished by running fotelinit.d/postgresql start The output from the above will look something like zoutodesk-070:-1 /etc/init.d/postgresql start Starting PostgreSQL 13 database server main If you're running MSF in your own machine, you can configure your system to start PostgreSQL when your system boots. However, because your Kall machine is actually a Dockor container, it doesn't include the systemet command and you must revert to the older methods for starting and stopping the If this is the first time you ve MSF. you'll need to configure the PostgreSQL database to support MSF. This is accomplished in bant The output should look something like Bek OTOR INI System has not been booted with ayatend an init nyaten (PID 1). Can't operate. Failed 18 Conect to bus Bont is down Starting database Systen hast been booted with watendait system (ID 1). Can't operate. Failed to connect to but lost in down E GD Lab02.Scanning (2) pdf Lab03-Theft.pdf Game Matenals nloads/Lab02-Scanning%20(2).pdf Creating database user 'mat' c) Creating databases To Creating databases of test! Creating configuration file "/usr/shareetasploit-framework/config/database. yni' (0) Creating initial database aches From Tim: If there's a "Message from Kall developers" mixed into the above, ignore it/them. The developers didn't have enough foresight to remember that Kali is also distributed a Docker container and their disable this feature" feature is broken. With time, I'll have this defeated, Note: if you've previously performed the midb init" step, and you're re-running it, the command will complain about such and exit. This is a nour, no-foul situation and the warnings can be ignored. You only need to run it once. (In ITN-2015 ce, because the destops are rebuilt every Saturday morning, you'll need to run it weekly, after each maintense period.) 8) Expand the size of your terminal window so that it takes up much of the real estate on your desktop. 9) Start MSF by running console Till goes well, your terminal window should now show an ASCII graphic (it changes every time you rosole"), followed by a blurb about the current wrsion of MSF. Examples petasploit v0.0.26-day 2092 exploits - 1127 Blaty - 365 post 582 payloads - 45 cedere - 10 Bapa Wwtasploit sip Adapters can be used for IP par LIST ID As the prompt Indiester, you wering Metasploit 10) When you see the wall>prompt you can run bon command line table and the output will show (complet Woonfig). However, the output will not be fod hack into MSF. The local map Tomap, it's built into MSF. re-run the above map scan (from step 4) but mapind of map The Command witches can be The output from the cute to the command Lo pot tor 102.168.10:2 0.0000 latacy Lola Adres 02:16:31:00:56:00 (US) x Game Materials Lab02-Scanning (21.pdf X Labo.Theft pdf b connect ip and Downloads/Labo2-Scanning%2012).pdf 10) When you see the prompt, you can run just about any command line executable and the outpat will show as normal (example ifconfig). However, the output will not be fed back into MSF This includes map Towmapite built into MISF, the above map scan (from step :) but bump" tamp"The commande switches can be used In other words, Rana dbp. 192.168.10.2-253 The output from the should look quite ar to the normal' nmap commande 1688 192.168.10.2-253 Map Starting Map 7.81 (https://por A 2021-01-23 03: Col Saap! Noap Scan report for 192.168.10.2 Collapot is up (0.000266 latency) Leap! MAC Address: 02166:31:00:65:00 (Unknown Copiap scan report for 192.168.10.3 Claptons up prompt. Example 316 > tota Hosts address EC 06_Bano 05_flavor 05_sp purpose info COS 192.168.10.2 02:36:31:00:65:03 192.168.10.3 4E194:BALEEB1A7 192.168.10.4 00:03:BE:10:FF 192.168, 10,5 4:74:51:56:DE:74 IMPORTANT The above is just an emple. Your results will be different Host Scans - NMap Omen you have I below to thepet, you'll want to sain each IP wildress for pen ports, 11) Leave your MSF window open Open another terminal window so that you can performans with Map. You can eithet run each scan individually via something like 192.168.10,2 map -AT-17 192.168.10,9 op at EP 192.168.10.11 ERP STF 190.168.10.21 Alternatively, you om oregate the fourthotels into a single command by wpurting them with centras, va comething like Notes les both of the above tople op tells map to an all ports on the targe) your detected I will be diferent than the shown in the examples Acutally, the con can be din ny of the four octets but the most common in the fourth Host Scans - Metasploit 19) In the MSF endow, to the tal form och titing map" for umapit mand). Altbach output will be different from the above can, it will Vio wwnloads/Lab02-Scanning%20(2).pdf Host Scans - Metasploit 12) Back in the MSF window, re-run the aggregated form of the map scan (substituing "db_nmap" for "map" in the command). Although the output will be different from the above map scan, it will have the same content. Also, the output will be stored in a table that you can display by running the services command The output should look something like rvices Berri por prate te no 102 103 108 4483 Sep so. Cosapen 12.10.10 hp-bp open 102 16.10.13 pentrs opes 80 web pes Not Give that we be a port, the listed as being. For this pesan, the were taken from a look up table for the videre vie pe Service probe will be disa telah 13) that thered from toch (cally), the detected pont in the bott) 14) is the destep 12.fowach the feet the IP window the home de to that with to the teachi TB