Answered step by step
Verified Expert Solution
Question
1 Approved Answer
4 Moving to the next question prevents changes to this answer Question 12 Steal customer data Obtain backupIntereptHack media email fileserver Burglarize Bribe admin Hack
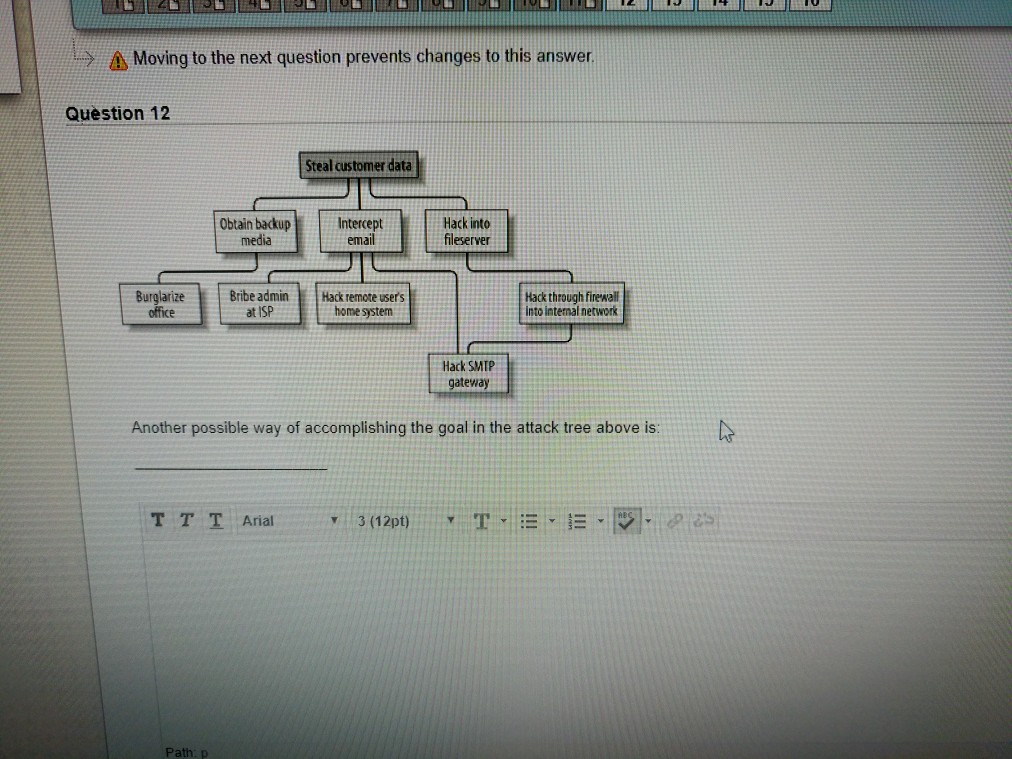
4 Moving to the next question prevents changes to this answer Question 12 Steal customer data Obtain backupIntereptHack media email fileserver Burglarize Bribe admin Hack remote users Hack through firewall into internal network office at ISP home system Hack SMIP gateway Another possible way of accomplishing the goal in the attack tree above is: ?//3(12pt) T. Y Path: p
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


