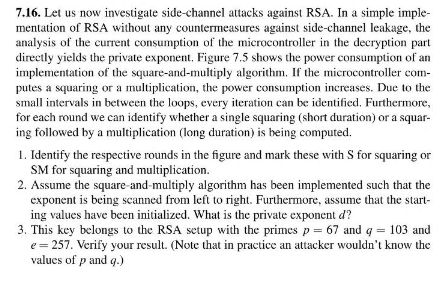
7.16. Let us now investigate side-channel attacks against RSA. In a simple imple mentation of RSA without any countermeasures against side-channel leakage, the analysis of the current consumption of the microcontroller in the decryption part directly yields the private exponent. Figure 7.5 shows the power consumption of an implementation of the square-and-multiply algorithm. If the microcontroller com- putes a squaring or a multiplication, the power consumption increases. Due to the small intervals in between the loops, every iteration can be identified, Furthermore, for each round we can identify whether a single squaring (short duration) or a squar ing followed by a multiplication (ong duration) is being computed. 1. Identify the respective rounds in the figure and mark these with S for squaring or SM for squaring and multiplication. 2. Assume the square-and-multiply algorithm has been implemented such that the exponent is being scanned from left to right. Furthermore, assume that the start- ing values have been initialized. What is the private exponent d? 3. This key belongs to the RSA setup with the primes p 67 and g 103 and 257. Verify your result. (Note that in practice an attacker wouldn't know the values of p and q.) 7.16. Let us now investigate side-channel attacks against RSA. In a simple imple mentation of RSA without any countermeasures against side-channel leakage, the analysis of the current consumption of the microcontroller in the decryption part directly yields the private exponent. Figure 7.5 shows the power consumption of an implementation of the square-and-multiply algorithm. If the microcontroller com- putes a squaring or a multiplication, the power consumption increases. Due to the small intervals in between the loops, every iteration can be identified, Furthermore, for each round we can identify whether a single squaring (short duration) or a squar ing followed by a multiplication (ong duration) is being computed. 1. Identify the respective rounds in the figure and mark these with S for squaring or SM for squaring and multiplication. 2. Assume the square-and-multiply algorithm has been implemented such that the exponent is being scanned from left to right. Furthermore, assume that the start- ing values have been initialized. What is the private exponent d? 3. This key belongs to the RSA setup with the primes p 67 and g 103 and 257. Verify your result. (Note that in practice an attacker wouldn't know the values of p and q.)








