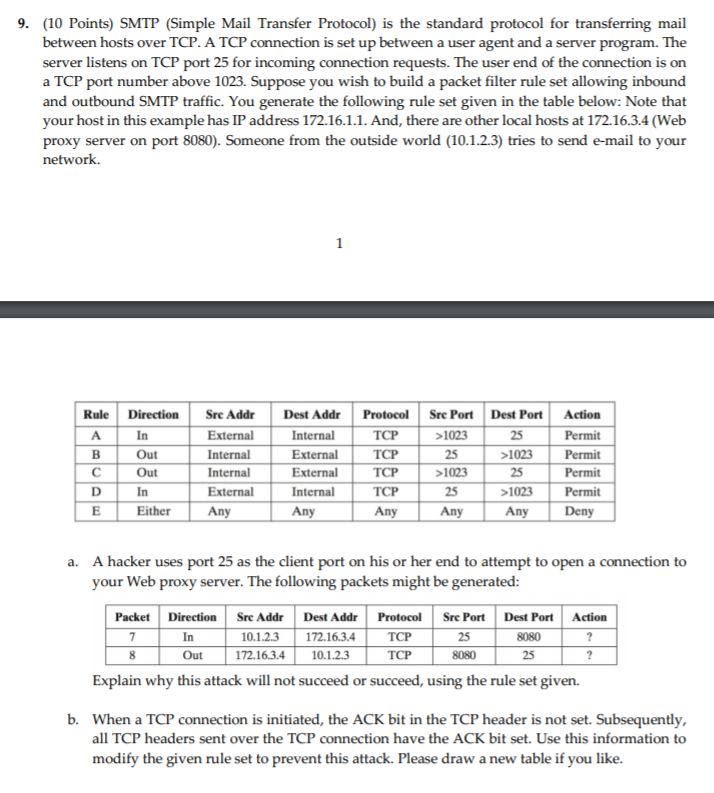
9. (10 Points) SMTP (Simple Mail Transfer Protocol) is the standard protocol for transferring mail between hosts over TCP. A TCP connection is set up between a user agent and a server program. The server listens on TCP port 25 for incoming connection requests. The user end of the connection is on a TCP port number above 1023. Suppose you wish to build a packet filter rule set allowing inbound and outbound SMTP traffic. You generate the following rule set given in the table below: Note that your host in this example has IP address 172.16.1.1. And, there are other local hosts at 172.16.3.4 (Web proxy server on port 8080). Someone from the outside world 10.1.2.3) tries to send e-mail to your Rule Direction Sre Addr Dest Addr Protcol Sre Port Dest Port Action In 25 Internal External 1023 1023 Permit Out Internal 1023 In Internal TCP 1023 Either External Ernal TCP Any Any Deny A hacker uses port 25 as the client port on his or her end to attempt to open a connection to your Web proxy server. The following packets might be generated: a. PacketDirection Sre AddrDest Addr ProtocolSre Port Dest PortAction In 0.1.2.3 172.16.3.4TC 172.16.3.4 10.1.2.3 Explain why this attack will not succeed or succeed, using the rule set given. b. When a TCP connection is initiated, the ACK bit in the TCP header is not set. Subsequently, all TCP headers sent over the TCP connection have the ACK bit set. Use this information to modify the given rule set to prevent this attack. Please draw a new table if you like. 9. (10 Points) SMTP (Simple Mail Transfer Protocol) is the standard protocol for transferring mail between hosts over TCP. A TCP connection is set up between a user agent and a server program. The server listens on TCP port 25 for incoming connection requests. The user end of the connection is on a TCP port number above 1023. Suppose you wish to build a packet filter rule set allowing inbound and outbound SMTP traffic. You generate the following rule set given in the table below: Note that your host in this example has IP address 172.16.1.1. And, there are other local hosts at 172.16.3.4 (Web proxy server on port 8080). Someone from the outside world 10.1.2.3) tries to send e-mail to your Rule Direction Sre Addr Dest Addr Protcol Sre Port Dest Port Action In 25 Internal External 1023 1023 Permit Out Internal 1023 In Internal TCP 1023 Either External Ernal TCP Any Any Deny A hacker uses port 25 as the client port on his or her end to attempt to open a connection to your Web proxy server. The following packets might be generated: a. PacketDirection Sre AddrDest Addr ProtocolSre Port Dest PortAction In 0.1.2.3 172.16.3.4TC 172.16.3.4 10.1.2.3 Explain why this attack will not succeed or succeed, using the rule set given. b. When a TCP connection is initiated, the ACK bit in the TCP header is not set. Subsequently, all TCP headers sent over the TCP connection have the ACK bit set. Use this information to modify the given rule set to prevent this attack. Please draw a new table if you like







