Answered step by step
Verified Expert Solution
Question
1 Approved Answer
A bank requires for their customers to access their online banking accounts to provide as User Id (or user name) the last 8 digits
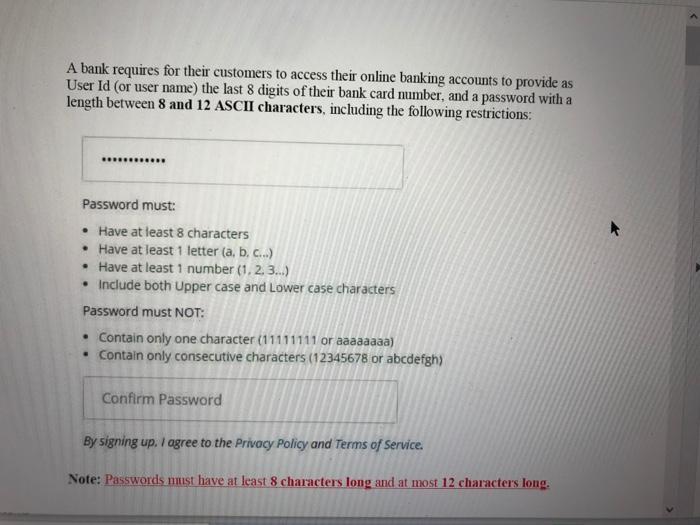

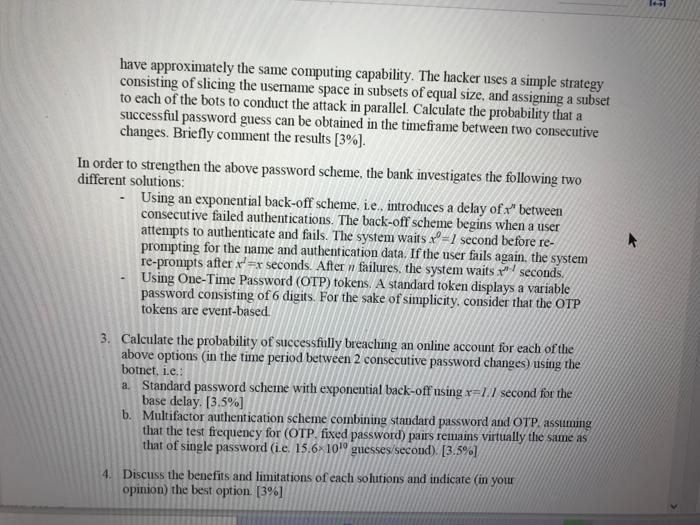
A bank requires for their customers to access their online banking accounts to provide as User Id (or user name) the last 8 digits of their bank card number, and a password with a length between 8 and 12 ASCII characters, including the following restrictions: Password must: Have at least 8 characters Have at least 1 letter (a, b, c.) Have at least 1 number (1, 2.3.) Include both Upper case and Lower case characters Password must NOT: Contain only one character (11111111 or aaaaaaaa) Contain only consecutive characters (12345678 or abcdefgh) Confirm Password By signing up. I agree to the Privacy Policy and Terms of Service. Note: Passwords nust have at least 8 characters long and at most 12 characters long. By signing up. I agree to the Privacy Policy and Terms of Service. Note: Passwords must have at least 8 characters long and at most 12 characters long. The bank also requires that each password be changed at least once every five years. 1. Assume that by conducting the attack using an average modern GPU 15.61010 passwords can be tested per second, calculate the probability that a hacker can guess a password in the timeframe between two consecutive changes. [2%] 2. A hacker controls a network of compromised machines (botnet) that can be used to launch the attack. The network consists of 1 million compromised machines (bots) located in different countries around the globe. Assume that the machines have approximately the same computing capability. The hacker uses a simple strategy consisting of slicing the usemame space in subsets of equal size, and assigning a subset to each of the bots to conduct the attack in parallel. Calculate the probability that a successful password guess can be obtained in the timeframe between two consecutive changes. Briefly comment the results [3%]. In order to strengthen the above password scheme, the bank investigates the following two different solutions: Using an exponential back-off schenme, ie., introduces a delay of " between consecutive failed authentications. The back-off scheme begins when a user attempts to authenticate and fails. The system waits x=1 second before re- prompting for the name and authentication data. If the user fails again. the system re-prompts after r=x seconds. After n failures, the system waits seconds. Using One-Time Password (OTP) tokens. A standard token displays a variable password consisting of 6 digits. For the sake of simplicity, consider that the OTP tokens are event-based 3. Calculate the probability of successfully breaching an online account for each of the above options (in the time period between 2 consecutive password changes) using the botnet, i.e.: a. Standard pasSword scheme with exponential back-off using x=1.1 second for the base delay. [3.5%] b. Multifactor authentication scheme combining standard password and OTP. assuming that the test frequency for (OTP. fixed password) pairs remains virtually the same as that of single password (ie. 15.61019 guesses/second). [3.5%) 4. Discuss the benefits and limitations of cach solutions and indicate (in your opinion) the best option. [3%]
Step by Step Solution
★★★★★
3.38 Rating (154 Votes )
There are 3 Steps involved in it
Step: 1
Required code in C include using namespace std selectArray is a utility function that is used to randomly generate a integer in the range 1 to 4 both inclusive int selectArray srandtimeNULL int i rand ...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


