Question: a) Explain the principle of least privilege b) What does the following protocol prove to Bob about the party claiming to be Alice? What does
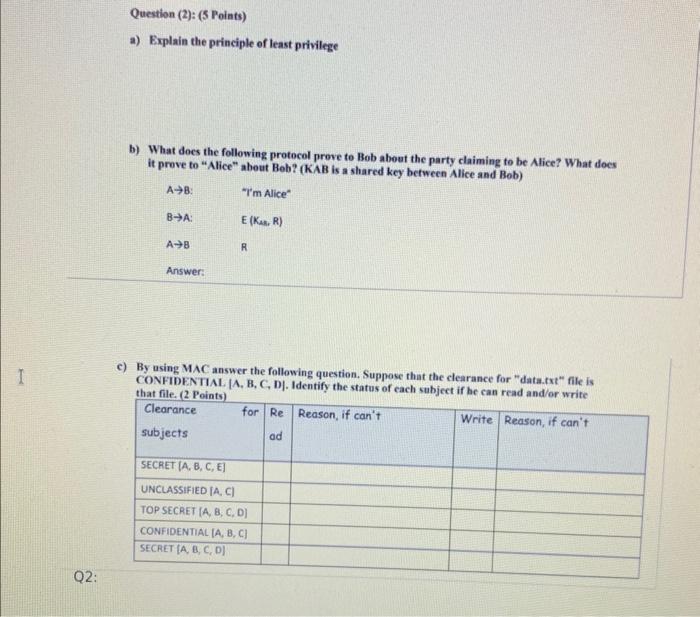
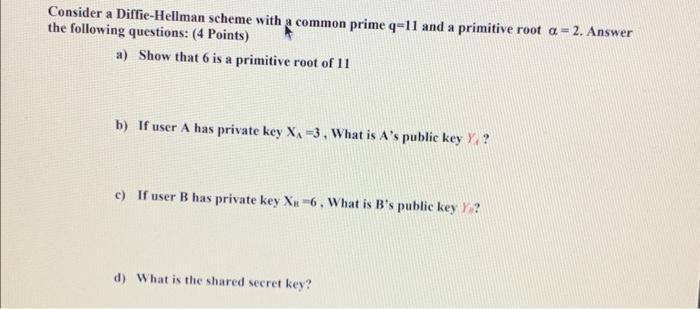

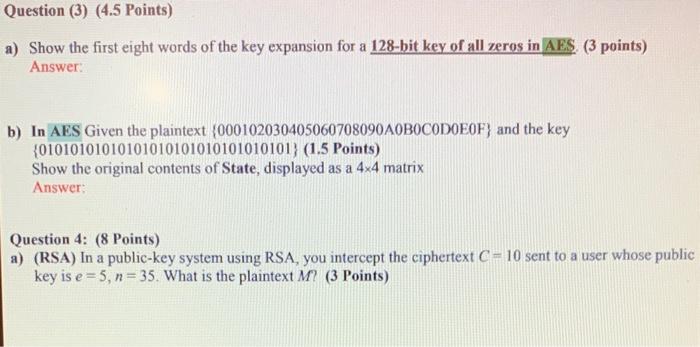
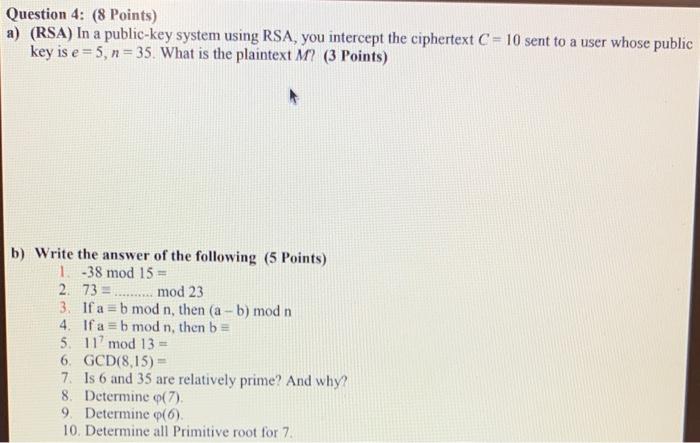
a) Explain the principle of least privilege b) What does the following protocol prove to Bob about the party claiming to be Alice? What does it prove to "Alice" about Beb? (KAB is a shared key between Alice and Bob) c) By using MAC answer the following question. Suppose that the clearance for "data.rxt" file is CONFIDENTIAL. [A, B, C, D]. Identify the status of each subject if he can read and/or write that file. (2 Points) Consider a Diffie-Hellman scheme with a common prime q=11 and a primitive root =2. Answer he following questions: (4 Points) a) Show that 6 is a primitive root of 11 b) If user A has private key XA=3, What is A 's public key YA ? c) If user B has private key XB=6, What is B 's public key n ? ? d) What is the shared secret key? Question (3): (3 Points) LinkedIn confirmed that it had experienced a data breach that likely compromised the e-mail addresses and passwords of 6.5 million of its users. This confirmation followed the posting of the password hashes for these users in a public forum. One criticism of Linkedin is that they used unsalted password hashes. In this question, we'll explore this criticism. Assume that each stolen password record had two fields in it: [user_email, Hash (password)] and that a user login would be verified by looking up the appropriate record based on user_email, and then checking if the corresponding hashed password field matched the hash of the password inputted by the user trying to log in. By contrast, if Linkedin had used a salted scheme, then cach record would have had three fields: [user_cmail, salt, Hash (password + salt)] and login verification would similarly require looking up the salt and using it when matching hashes. Given this: a) Suppose the attacker's goal is to break your password via a dictionary attack. Does the lack of salting in Linkedin's scheme make this goal substantially easier? b) Suppose the attacker's goal is to break at least half of the passwords via a dictionary attack. Does the lack of salting in this scheme make this goal substantially easier? c) Suppose you are contacted by the attacker and given a set of password hashes (that's it, no user_name, no salt). Assuming the hash function is known, is there a measurement you could make in order to infer if the hashes are likely salted or not? a) Show the first eight words of the key expansion for a 128-bit key of all zeros in AES. (3 points) Answer: b) In AES Given the plaintext {000102030405060708090 A0B0C0D0E0F } and the key {01010101010101010101010101010101} (1.5 Points) Show the original contents of State, displayed as a 44 matrix Answer: Question 4: (8 Points) a) (RSA) In a public-key system using RSA, you intercept the ciphertext C=10 sent to a user whose public key is e=5,n=35. What is the plaintext M ? (3 Points) Question 4: (8 Points) a) (RSA) In a public-key system using RSA, you intercept the ciphertext C=10 sent to a user whose public key is e=5,n=35. What is the plaintext M ? (3 Points) b) Write the answer of the following (5 Points) 1. 38mod15= 2. 73=..mod23 3. If a=bmodn, then (ab)modn 4. If abmodn, then b 5. 117mod13= 6. GCD(8,15)= 7. Is 6 and 35 are relatively prime? And why? 8. Determine (7). 9. Determine (6). 10. Determine all Primitive root for 7
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


