Answered step by step
Verified Expert Solution
Question
1 Approved Answer
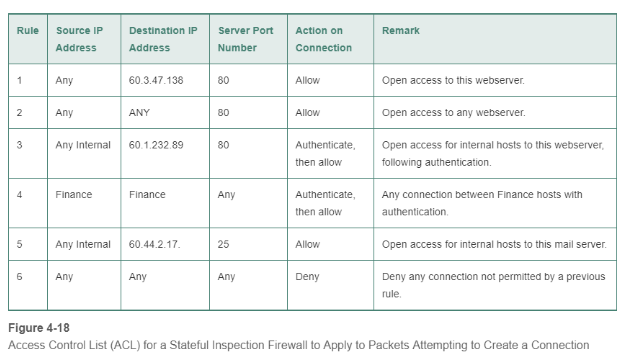
a) In Figure 4-18 , explain why Rule 1 brings more security than Rule 2. b) Explain why the last rule in an ACL should
a) In Figure 4-18, explain why Rule 1 brings more security than Rule 2. b) Explain why the last rule in an ACL should deny anything not previously approved by earlier rules. c) Why do you think authentication is sometimes required before accepting a connection? d) When a packet addressed to 60.1.232.89 arrives, what rule will the SPI firewall look at first? e) Why must Rule 2 come after Rule 1?
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


